🚨NEW REPORT: first forensic confirmation of #Paragon mercenary spyware infections in #Italy...
Known targets: Activists & journalists.
We also found deployments around the world. Including ...Canada?
So #Paragon makes zero-click spyware marketed as better than NSO's Pegasus...
Harder to find...

...And more ethical too!
This caught our attention at #Citizenlab. And we were skeptical.

So.. it was time to start digging.

We got a tip about a single bit of #Paragon infrastructure & my brilliant colleague Bill Marczak developed a technique to fingerprint some of the mercenary spyware infrastructure (both victim-facing & customer side) globally.

So much for invisibility.
What we found startled us.
We found a bunch of apparent deployments of Paragon's mercenary spyware in places like #Australia, #Denmark, #Israel, #Cyprus #Singapore and... #Canada.
Fun.

We also found interesting stuff at a datacenter in #Germany

Caveats: the methodology we use only surfaces a subset of customers at a particular time.
So ...about #Canada.
My colleagues on the legal side began digging. The more they pulled, the more questions surfaced about whether the Ontario Provincial Police is rolling mercenary spyware.

While investigating, we found signs #WhatsApp was being used as a vector for infections.
We shared our analysis with Meta which had an ongoing investigation into Paragon.
They shared findings with WhatsApp which discovered & mitigated a zero-click attack.
They went public, and notified ~90 users that they believed were targeted.

WhatsApp's notifications to targets turbocharged what we all knew about #Paragon.

Cases began coming out: an investigative journalist in #Italy and sea rescue activists were among the first. Francesco Cancellato. Editor in Chief of Fanpage.it, & Luca Casarini and Dr. Giuseppe “Beppe” Caccia of Mediterranea Saving Humans
They consented to us doing a forensic analysis...

Sure enough, we found traces of infection on several Androids.
We call the indicator #BIGPRETZEL & #WhatsApp confirms that they believe BIGPRETZEL is associated with #Paragon's spyware.
In the weeds a bit: Android log forensics are tricky. Logs get overwritten fast, are captured sporadically & may not go back very far. So, not finding BIGPRETZEL on a targeted phone wouldn't be enough to say it wasn't infected. In such a case, the only safe course of action for a notified Paragon target would be to presume they had been infected.

Our analysis is ongoing.
.... but There's more!
There's more! We'd been analyzing the iPhone of human rights activist David Yambio, who is focused on abuses against migrants in Libya (they are often victims of torture, trafficking, and killings) who works closely with the other targets.

Last year he got notified by Apple that he was targeted with sophisticated spyware.
We've forensically confirmed the infection & shared details with Apple.

Apple confirms they fixed the vectors used to target him as of iOS 18.
We're not doing a full technical attribution of this novel spyware to a particular company yet. But it's not like anything we've seen.
Troublingly, timeline of David's spyware targeting lines up with when he was providing information to the International Criminal Court about torture by human traffickers in #Libya.
But there's even more spying afoot against this cluster of activists!
Luca also got a notification last February about targeting with a different kind of surveillance tech.

He wasn't alone. Father Mattia Ferrari, chaplain of Luca's lifesaving organization' also got a notification.

#Italy's response to the unfolding #Paragon scandal has been exceptionally chaotic. So we included a little timeline.
Denials, then admissions, then refusals to say more citing secrecy.

Honestly, deja vu of how Pegasus-abusing governments have handled PR...
TAKEAWAYS:
TAKEAWAY 1: you can't abuse-proof mercenary spyware. Selling just democracies won't prevent abuses. Most democracies have plenty of historic examples of surveillance abuses. Why should spyware be different?

TAKEAWAY 2: #Paragon's technical tradeoffs to be less detectable didn't prevent them getting discovered.
Just made it harder.

TAKEAWAY 3: I think we're only looking at the tip the #Paragon hackberg
For example, the ~90 notification number from #WhatsApp
only represents 1 infection vector that got caught & notified.
There may be non-notified spyware victims walking around right now who were infected via a different mechanism.
In #Italy, too we also need to better understand the other surveillance technologies pointed at this cluster of people.
Finally, we gave #Paragon room to respond to a summary of our key findings.
Their US Executive Chairman, a 30+ year #CIA veteran, responded in a way that sounded very familiar to how NSO Group did PR.

1 - Say there are inaccuracies..
2- ..But refuse to specify them
3-Cite customer confidentiality as a reason to not say more.

We welcome any clarifications they have now that they've read our full report.
FINAL NOTES: our #citizenlab investigations are usually big, collaborative team productions. Smart co-authors, awesome collaborators.

The key to nearly all our research into spyware is targets' brave choice to speak out.
And work with us to forensically analyze their devices... We are very grateful to them.
This is how we collectively get a better understanding of mercenary spyware abuses.
And journey towards accountability.
Thanks for reading! Drop questions in the replies!
READ THE FULL REPORT

The Citizen Lab
Virtue or Vice? A First Look at Paragon’s Proliferating Spyware Operations - The Citizen Lab
In our first investigation into Israel-based spyware company, Paragon Solutions, we begin to untangle multiple threads connected to the proliferati...



 “In Serbia, you can hire a hitman for a half of the money...what else would they be prepared to pay for?!” - a spyware-targeted reporter.
Indeed.
“In Serbia, you can hire a hitman for a half of the money...what else would they be prepared to pay for?!” - a spyware-targeted reporter.
Indeed.
 Notice that the targeting is happening over a messenger program with a link, not a zero-click?
The why is unclear. Maybe Pegasus didn't have a working exploit against those phones. Or maybe the customer didn't get the platinum zero click package and so had to do some social engineering. Interesting.
BACKGROUND:
This is the THIRD report of Pegasus abuses in Serbia in 2 years.
And nearly a decade after the first Pegasus abuses got reported, NSO Group is still fueling attacks against freedom of speech.
We're here because spyware companies still don't feel meaningful consequences.
Notice that the targeting is happening over a messenger program with a link, not a zero-click?
The why is unclear. Maybe Pegasus didn't have a working exploit against those phones. Or maybe the customer didn't get the platinum zero click package and so had to do some social engineering. Interesting.
BACKGROUND:
This is the THIRD report of Pegasus abuses in Serbia in 2 years.
And nearly a decade after the first Pegasus abuses got reported, NSO Group is still fueling attacks against freedom of speech.
We're here because spyware companies still don't feel meaningful consequences.
 And DC is home to a seemingly-infinite number of lobbyists that are willing to help them try to get off sanctions lists...
READ THE REPORT by Amnesty Tech & BIRN.
And DC is home to a seemingly-infinite number of lobbyists that are willing to help them try to get off sanctions lists...
READ THE REPORT by Amnesty Tech & BIRN. 
 This is a consequence.
Companies intrusively soak up your personal data, get breached, and nobody blinks.
This is a consequence.
Companies intrusively soak up your personal data, get breached, and nobody blinks.  Breaches are one of the first places attackers go when they want to target.
Breaches are one of the first places attackers go when they want to target.
 This is why password re-use is dangerous. And two factor authentication is key.
If your favorite 'strong password' is in a breach, an attacker is going to try it against every other account you have.
This is why password re-use is dangerous. And two factor authentication is key.
If your favorite 'strong password' is in a breach, an attacker is going to try it against every other account you have.
 Story:
Story: 
 How did a reporter get added? Well, the use of encrypted chat is ubiquitous but not explicitly accepted, supported or discussed in most institutions.
Which means users are left to fend for themselves in how they use & understand these tools.
And are usually about 1 mistake away from self-doxxing group contents.
How did a reporter get added? Well, the use of encrypted chat is ubiquitous but not explicitly accepted, supported or discussed in most institutions.
Which means users are left to fend for themselves in how they use & understand these tools.
And are usually about 1 mistake away from self-doxxing group contents.
 This also left me wondering: is anyone screening these devices for mercenary spyware like Pegasus?
This also left me wondering: is anyone screening these devices for mercenary spyware like Pegasus?
 Experience tells me the answer is: maybe not.
Article:
Experience tells me the answer is: maybe not.
Article: 
 (Machine translated)
Original (FR):
(Machine translated)
Original (FR): 

 ...And more ethical too!
This caught our attention at #Citizenlab. And we were skeptical.
...And more ethical too!
This caught our attention at #Citizenlab. And we were skeptical.  So.. it was time to start digging.
So.. it was time to start digging.  We got a tip about a single bit of #Paragon infrastructure & my brilliant colleague Bill Marczak developed a technique to fingerprint some of the mercenary spyware infrastructure (both victim-facing & customer side) globally.
We got a tip about a single bit of #Paragon infrastructure & my brilliant colleague Bill Marczak developed a technique to fingerprint some of the mercenary spyware infrastructure (both victim-facing & customer side) globally.  So much for invisibility.
What we found startled us.
We found a bunch of apparent deployments of Paragon's mercenary spyware in places like #Australia, #Denmark, #Israel, #Cyprus #Singapore and... #Canada.
Fun.
So much for invisibility.
What we found startled us.
We found a bunch of apparent deployments of Paragon's mercenary spyware in places like #Australia, #Denmark, #Israel, #Cyprus #Singapore and... #Canada.
Fun.  We also found interesting stuff at a datacenter in #Germany
We also found interesting stuff at a datacenter in #Germany  Caveats: the methodology we use only surfaces a subset of customers at a particular time.
So ...about #Canada.
My colleagues on the legal side began digging. The more they pulled, the more questions surfaced about whether the Ontario Provincial Police is rolling mercenary spyware.
Caveats: the methodology we use only surfaces a subset of customers at a particular time.
So ...about #Canada.
My colleagues on the legal side began digging. The more they pulled, the more questions surfaced about whether the Ontario Provincial Police is rolling mercenary spyware.  While investigating, we found signs #WhatsApp was being used as a vector for infections.
We shared our analysis with Meta which had an ongoing investigation into Paragon.
They shared findings with WhatsApp which discovered & mitigated a zero-click attack.
They went public, and notified ~90 users that they believed were targeted.
While investigating, we found signs #WhatsApp was being used as a vector for infections.
We shared our analysis with Meta which had an ongoing investigation into Paragon.
They shared findings with WhatsApp which discovered & mitigated a zero-click attack.
They went public, and notified ~90 users that they believed were targeted.
 WhatsApp's notifications to targets turbocharged what we all knew about #Paragon.
WhatsApp's notifications to targets turbocharged what we all knew about #Paragon.
 Cases began coming out: an investigative journalist in #Italy and sea rescue activists were among the first. Francesco Cancellato. Editor in Chief of Fanpage.it, & Luca Casarini and Dr. Giuseppe “Beppe” Caccia of Mediterranea Saving Humans
They consented to us doing a forensic analysis...
Cases began coming out: an investigative journalist in #Italy and sea rescue activists were among the first. Francesco Cancellato. Editor in Chief of Fanpage.it, & Luca Casarini and Dr. Giuseppe “Beppe” Caccia of Mediterranea Saving Humans
They consented to us doing a forensic analysis...  Sure enough, we found traces of infection on several Androids.
We call the indicator #BIGPRETZEL & #WhatsApp confirms that they believe BIGPRETZEL is associated with #Paragon's spyware.
In the weeds a bit: Android log forensics are tricky. Logs get overwritten fast, are captured sporadically & may not go back very far. So, not finding BIGPRETZEL on a targeted phone wouldn't be enough to say it wasn't infected. In such a case, the only safe course of action for a notified Paragon target would be to presume they had been infected.
Sure enough, we found traces of infection on several Androids.
We call the indicator #BIGPRETZEL & #WhatsApp confirms that they believe BIGPRETZEL is associated with #Paragon's spyware.
In the weeds a bit: Android log forensics are tricky. Logs get overwritten fast, are captured sporadically & may not go back very far. So, not finding BIGPRETZEL on a targeted phone wouldn't be enough to say it wasn't infected. In such a case, the only safe course of action for a notified Paragon target would be to presume they had been infected.
 Our analysis is ongoing.
.... but There's more!
There's more! We'd been analyzing the iPhone of human rights activist David Yambio, who is focused on abuses against migrants in Libya (they are often victims of torture, trafficking, and killings) who works closely with the other targets.
Our analysis is ongoing.
.... but There's more!
There's more! We'd been analyzing the iPhone of human rights activist David Yambio, who is focused on abuses against migrants in Libya (they are often victims of torture, trafficking, and killings) who works closely with the other targets.  Last year he got notified by Apple that he was targeted with sophisticated spyware.
We've forensically confirmed the infection & shared details with Apple.
Last year he got notified by Apple that he was targeted with sophisticated spyware.
We've forensically confirmed the infection & shared details with Apple.
 Apple confirms they fixed the vectors used to target him as of iOS 18.
We're not doing a full technical attribution of this novel spyware to a particular company yet. But it's not like anything we've seen.
Troublingly, timeline of David's spyware targeting lines up with when he was providing information to the International Criminal Court about torture by human traffickers in #Libya.
But there's even more spying afoot against this cluster of activists!
Luca also got a notification last February about targeting with a different kind of surveillance tech.
Apple confirms they fixed the vectors used to target him as of iOS 18.
We're not doing a full technical attribution of this novel spyware to a particular company yet. But it's not like anything we've seen.
Troublingly, timeline of David's spyware targeting lines up with when he was providing information to the International Criminal Court about torture by human traffickers in #Libya.
But there's even more spying afoot against this cluster of activists!
Luca also got a notification last February about targeting with a different kind of surveillance tech.  He wasn't alone. Father Mattia Ferrari, chaplain of Luca's lifesaving organization' also got a notification.
He wasn't alone. Father Mattia Ferrari, chaplain of Luca's lifesaving organization' also got a notification.
 #Italy's response to the unfolding #Paragon scandal has been exceptionally chaotic. So we included a little timeline.
Denials, then admissions, then refusals to say more citing secrecy.
#Italy's response to the unfolding #Paragon scandal has been exceptionally chaotic. So we included a little timeline.
Denials, then admissions, then refusals to say more citing secrecy.  Honestly, deja vu of how Pegasus-abusing governments have handled PR...
TAKEAWAYS:
TAKEAWAY 1: you can't abuse-proof mercenary spyware. Selling just democracies won't prevent abuses. Most democracies have plenty of historic examples of surveillance abuses. Why should spyware be different?
Honestly, deja vu of how Pegasus-abusing governments have handled PR...
TAKEAWAYS:
TAKEAWAY 1: you can't abuse-proof mercenary spyware. Selling just democracies won't prevent abuses. Most democracies have plenty of historic examples of surveillance abuses. Why should spyware be different?
 TAKEAWAY 2: #Paragon's technical tradeoffs to be less detectable didn't prevent them getting discovered.
Just made it harder.
TAKEAWAY 2: #Paragon's technical tradeoffs to be less detectable didn't prevent them getting discovered.
Just made it harder.
 TAKEAWAY 3: I think we're only looking at the tip the #Paragon hackberg
For example, the ~90 notification number from #WhatsApp
only represents 1 infection vector that got caught & notified.
There may be non-notified spyware victims walking around right now who were infected via a different mechanism.
In #Italy, too we also need to better understand the other surveillance technologies pointed at this cluster of people.
Finally, we gave #Paragon room to respond to a summary of our key findings.
Their US Executive Chairman, a 30+ year #CIA veteran, responded in a way that sounded very familiar to how NSO Group did PR.
TAKEAWAY 3: I think we're only looking at the tip the #Paragon hackberg
For example, the ~90 notification number from #WhatsApp
only represents 1 infection vector that got caught & notified.
There may be non-notified spyware victims walking around right now who were infected via a different mechanism.
In #Italy, too we also need to better understand the other surveillance technologies pointed at this cluster of people.
Finally, we gave #Paragon room to respond to a summary of our key findings.
Their US Executive Chairman, a 30+ year #CIA veteran, responded in a way that sounded very familiar to how NSO Group did PR.
 1 - Say there are inaccuracies..
2- ..But refuse to specify them
3-Cite customer confidentiality as a reason to not say more.
1 - Say there are inaccuracies..
2- ..But refuse to specify them
3-Cite customer confidentiality as a reason to not say more.
 We welcome any clarifications they have now that they've read our full report.
FINAL NOTES: our #citizenlab investigations are usually big, collaborative team productions. Smart co-authors, awesome collaborators.
We welcome any clarifications they have now that they've read our full report.
FINAL NOTES: our #citizenlab investigations are usually big, collaborative team productions. Smart co-authors, awesome collaborators.  The key to nearly all our research into spyware is targets' brave choice to speak out.
And work with us to forensically analyze their devices... We are very grateful to them.
This is how we collectively get a better understanding of mercenary spyware abuses.
And journey towards accountability.
Thanks for reading! Drop questions in the replies!
READ THE FULL REPORT
The key to nearly all our research into spyware is targets' brave choice to speak out.
And work with us to forensically analyze their devices... We are very grateful to them.
This is how we collectively get a better understanding of mercenary spyware abuses.
And journey towards accountability.
Thanks for reading! Drop questions in the replies!
READ THE FULL REPORT 


 You haven't heard about this before because these orders are secret & there are typically bans on talking about them.
SHORT TERM IMPACT:
Apple will probably stop offering encrypted iCloud storage in the UK.
DETAILS:
the UK Home Secretary sent #Apple a so-called "Technical Capability Notice" which is a demand for access.
These flow from the 2016 Investigatory Powers Act (aka "Snooper's Charter") and is a mechanism for the government to *compel* companies to provide access.
ENFORCED SILENCE:
Among the more pernicious parts of this secret demand: Apple would be *FORBIDDEN* from telling users that the backdoor had been introduced into iCloud's Advanced Data Protection.
BIG PICTURE:
The public really doesn't realize it, but cloud backups of phones are constantly used for surveillance. Huge #privacy & #encryption gap.
By introducing optional Advanced Data Protection, Apple extended similar protections of device encryption to users' clouds.
So, since ADP was introduced in 2022, governments have been scheming to undermine it.
LOOKING INTO THE FUTURE:
It's only a matter of time before governments try to target Private Cloud Compute. And do so with the same secret legal tools.
REPORT:
You haven't heard about this before because these orders are secret & there are typically bans on talking about them.
SHORT TERM IMPACT:
Apple will probably stop offering encrypted iCloud storage in the UK.
DETAILS:
the UK Home Secretary sent #Apple a so-called "Technical Capability Notice" which is a demand for access.
These flow from the 2016 Investigatory Powers Act (aka "Snooper's Charter") and is a mechanism for the government to *compel* companies to provide access.
ENFORCED SILENCE:
Among the more pernicious parts of this secret demand: Apple would be *FORBIDDEN* from telling users that the backdoor had been introduced into iCloud's Advanced Data Protection.
BIG PICTURE:
The public really doesn't realize it, but cloud backups of phones are constantly used for surveillance. Huge #privacy & #encryption gap.
By introducing optional Advanced Data Protection, Apple extended similar protections of device encryption to users' clouds.
So, since ADP was introduced in 2022, governments have been scheming to undermine it.
LOOKING INTO THE FUTURE:
It's only a matter of time before governments try to target Private Cloud Compute. And do so with the same secret legal tools.
REPORT:

 Subaru's employee portal holds a year's worth of location data for all internet-connected cars.
Subaru's employee portal holds a year's worth of location data for all internet-connected cars.  We know this because it was vulnerable (now fixed). You could pull a year's worth of driving just with a license plate.
We know this because it was vulnerable (now fixed). You could pull a year's worth of driving just with a license plate.
 Props to Sam Curry & Shubham Shah for exposing it. Pic is a years' worth of Sam's mom's #Subaru locations.
I seriously doubt any owner has a clear idea that this data is being collected on them.
But the same thing is replicated for almost every car mfr (see the #Mozilla foundation report on car privacy link)
Literally no car owner has asked for their whip to be turned into a surveillance portal.
And yet..
Car companies feel basically no pressure to do right by customers, but experience a lot of incentives to mine their movements for money.
Sidenote: same (now closed) vulnerability also enabled remote unlocks & starts and a bunch of other highly undesirable things.
Reading list:
The Subaru research:
Props to Sam Curry & Shubham Shah for exposing it. Pic is a years' worth of Sam's mom's #Subaru locations.
I seriously doubt any owner has a clear idea that this data is being collected on them.
But the same thing is replicated for almost every car mfr (see the #Mozilla foundation report on car privacy link)
Literally no car owner has asked for their whip to be turned into a surveillance portal.
And yet..
Car companies feel basically no pressure to do right by customers, but experience a lot of incentives to mine their movements for money.
Sidenote: same (now closed) vulnerability also enabled remote unlocks & starts and a bunch of other highly undesirable things.
Reading list:
The Subaru research: 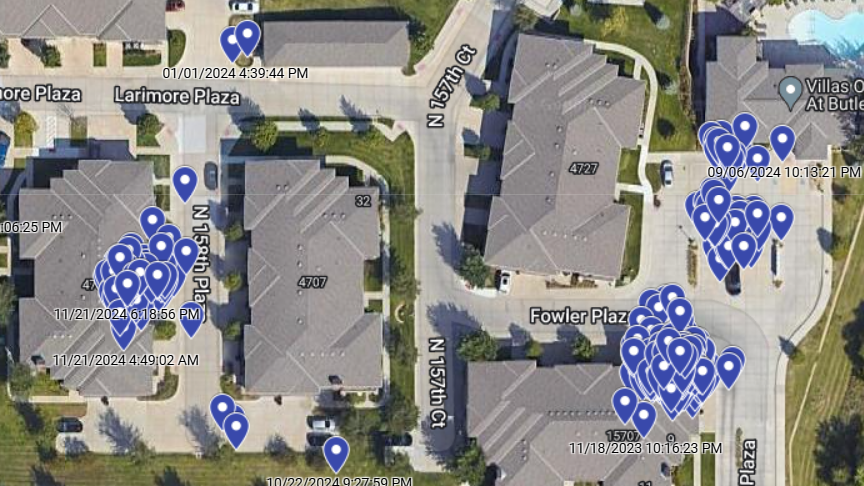








 Amit Forlit's alleged customer: a US lobbying firm named DCI Group...representing oil & gas giant ExxonMobil.
Amit Forlit's alleged customer: a US lobbying firm named DCI Group...representing oil & gas giant ExxonMobil.
 IT BEGINS
The criminal case was triggered back in 2018, when US-based nonprofits targeted by hackers whom we'd been working with requested that we notify the authorities.
We'd found an absolute raft of targeting and attributed the fingers-on-keyboards to an Indian hack-for-hire operation.
THE TARGETS
Targets ranged from environmental orgs to net neutrality advocates , everyone that asked questions about massive financial fraud by payment processor WireCard & so many more.
IT BEGINS
The criminal case was triggered back in 2018, when US-based nonprofits targeted by hackers whom we'd been working with requested that we notify the authorities.
We'd found an absolute raft of targeting and attributed the fingers-on-keyboards to an Indian hack-for-hire operation.
THE TARGETS
Targets ranged from environmental orgs to net neutrality advocates , everyone that asked questions about massive financial fraud by payment processor WireCard & so many more.
 Our friends at EFF also spotted the phishing against net neutrality orgs & reported on it, we later attributed it to the Indian group.
Our friends at EFF also spotted the phishing against net neutrality orgs & reported on it, we later attributed it to the Indian group.
 TIME TO NAME & SHAME
We published alongside Reuters, naming the Indian group (BellTrox) back in 2020.
TIME TO NAME & SHAME
We published alongside Reuters, naming the Indian group (BellTrox) back in 2020.  TWO ISRAELI PRIVATE SPIES...
Fast forward to today's efforts to extradite Amit Forlit, who was arrested at Heathrow last year.
He's actually the *second Israeli private investigator* charged in this massive hacking scheme.
The first, Aviram Azari, was arrested in 2019 on his way to Disney World, convicted & is serving out his sentence.
TWO ISRAELI PRIVATE SPIES...
Fast forward to today's efforts to extradite Amit Forlit, who was arrested at Heathrow last year.
He's actually the *second Israeli private investigator* charged in this massive hacking scheme.
The first, Aviram Azari, was arrested in 2019 on his way to Disney World, convicted & is serving out his sentence.  The US accuses Forlit of serving as a go-between for Indian hack-for-hire groups.. and a global client list.
The US accuses Forlit of serving as a go-between for Indian hack-for-hire groups.. and a global client list.  The US doesn't name the lobbying firm or the big oil and gas company in their filing.....but Forlit's own lawyer helpfully filled in the details, as reported by Reuters.
The US doesn't name the lobbying firm or the big oil and gas company in their filing.....but Forlit's own lawyer helpfully filled in the details, as reported by Reuters.  THE SCHEME
The operation targeting environmental groups is pretty wild, and when we timelined phishing attempts against their advocacy strategies. The targeting was smart & super-aware of relationships between the targets.
THE SCHEME
The operation targeting environmental groups is pretty wild, and when we timelined phishing attempts against their advocacy strategies. The targeting was smart & super-aware of relationships between the targets.  When hacking is corporate, they make memos.
When hacking is corporate, they make memos.


 Epic line: The kind of message that prosecutors of...
TAKEAWAY
Today, many legal fights, including attacks on nonprofits & civil liberties groups, have a secret undercurrent of hacking-for-hire.
Epic line: The kind of message that prosecutors of...
TAKEAWAY
Today, many legal fights, including attacks on nonprofits & civil liberties groups, have a secret undercurrent of hacking-for-hire.  The powerful interests that commission the hacking & benefit from the often-manipulated 'leaks' escape consequences.
But if you are around these issues, you may get targeted too.
This case goes further up the chain than any before. We'll see just how high, but it is great to see some consequence brought to this shady ecosystem.
I'll keep folks here updated.
Reading list:
Our Citizen lab investigation:
The powerful interests that commission the hacking & benefit from the often-manipulated 'leaks' escape consequences.
But if you are around these issues, you may get targeted too.
This case goes further up the chain than any before. We'll see just how high, but it is great to see some consequence brought to this shady ecosystem.
I'll keep folks here updated.
Reading list:
Our Citizen lab investigation:
