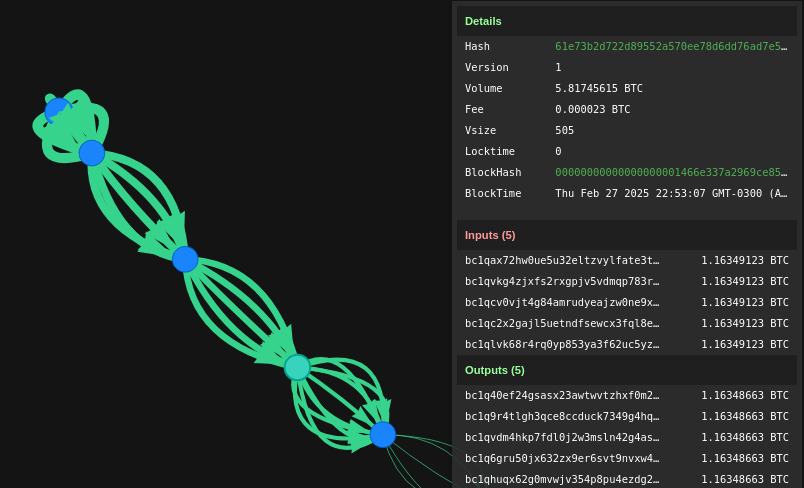
Now someone please get her to spend some sats!
View quoted note →
lontivero
_@lontivero.github.io
npub1nccw...z7mj
Bitcoin privacy warrior.
Immediately after Turbolay and me received Wasabi, everybody suggested that we start looking for some grants to support the development effort. After all, Wasabi is just a FOSS software without any source of revenue, and there wasn't a company to pay our salaries anymore. The most resounding alternatives were OpenSats and the HRF grants, and I was suggested to apply to both of them. However, I wanted to avoid asking for money from the HRF, and for that reason, I applied to OpenSats even though I knew that many of the people behind it were not the biggest fans of Wasabi. Anyway, I preferred to ask for help from those who I perceive as part of the community. My application was rejected. Turbolay applied before me but his application was rejected too.
Turbolay then decided to apply for one of the HRF grants and asked me if I was okay with him applying for both of us together as the "Wasabi team," and I agreed. So he did it. It was a mistake; I shouldn't have agreed, but I knew that even though they usually highlight how important privacy is for democracy, they would not support us (maybe they cannot do it, who knows). The application was rejected.
After that, Turbolay started looking for a job, and fortunately, he found a non-fiat one! But I cannot avoid feeling that if I had released the Wasabi Silent Payment donation button earlier, he would still be 100% available for Wasabi. Even though Turbolay is still making great contributions, he's a fucking hero, a real one 🫡
I worked for a credit card company, and they always denied all kinds of reports. To illustrate how far they went in that practice, it is enough to mention that after a release, many users started reporting that the home banking website was displaying porn site ads, but the support team just blamed users for having their computers infected.
After a few days, the top management saw the ads and finally called the dev team. There was a JavaScript added by the InfoSec team using the reverse proxy. That script was provided by the local branch of Visa.
A Visa developer created a silly script to do something, but it seems he believed that his code had to be "protected" somehow, so he pasted his code into an online JavaScript "encryptor," which returned a self-decrypting version of his script plus something else.
I told the managers what the problem was, and they called Prisma (Visa), who denied the problem. I created an extremely detailed analysis with a step-by-step guide showing how the script worked, but they simply denied it.
Meanwhile, I suggested removing the script, but InfoSec said no because, as Visa partners, they needed it. I could have also fixed the script, but you learn that somehow that backfires on you, so it is not 100% incompetence but the logic of the system.
One day after, InfoSec decided to remove the script, and the problem disappeared. It wasn't until other partners started to complain that Prisma finally accepted that their script was injecting ads.
Something funny is that nobody detected that earlier because porn ads are blocked in all banking offices.
ON ERROR Resume Next