Looks like something’s finally happening…
#btc #bitcoin #ethereum #bull


Public transportation is often called a mirror of a nation’s civility. Why? Because you can learn a lot about a society by observing how people behave in those crowded buses and minibuses at the crack of dawn. A country’s level of development may not be measured by the number of buses per capita, but whether those buses are on time, the seats are clean, the driver is courteous, or at least if people make an effort to give up their seats – even discreetly – says a great deal.
The quality of public transportation is a subtle yet striking indicator of the “true” level of civilization in a region. Imagine this: as someone hanging onto a bus handle in the early morning, still half asleep, you find yourself given a seat, not out of kindness, but simply as a matter of “duty.” A silent scream rises within you, “Is this for real?” Yet, as the bus fills to the brim and punctuality becomes a luxury overlooked, it’s not hard to see how deeply ingrained – or absent – mutual respect, empathy, and even societal peace truly are in that country.
In a place where the metro runs like clockwork, schedules are reliable to the minute, and people actually line up to board – and yes, there are such places – that society has not only mastered public transportation but achieved a level of respect and trust among people. But where public transit triggers arguments before the next stop, where a missed announcement has everyone looking around, wide-eyed, asking, “What’s going on now?” there, a certain unease is surfacing. Because the chaos in public transportation is a miniature of a greater chaos.
We live this chaos every day; the pushing and shoving, sweaty faces, buses that never arrive on time… In a system without punctuality, people’s daily stresses are a stark reminder that what we call “civility” may exist only on the surface. It’s like a polite slap in the face; we may believe we live in a civilized society, but maybe we’re just part of a “survival” game.
Sometimes, even a one-minute delay, a seemingly minor problem at first, can set people into a downward spiral of negativity. A person who arrives late to work because the bus was late may stew in that stress all day long. By the time they get home in the evening, that single delay has essentially drained their entire day. So, the quality of public transport – its timing, comfort, and reliability – serves as the lubricant in the machinery of societal peace. When this machinery runs smoothly, people are at ease; when it doesn’t, everyone lives in a state of tension with one another.
In short, the quality of public transportation is an indirect yet sharp reflection of a nation’s level of civility, of the respect people hold for each other and for life itself. And let’s not forget: “If a country forces its citizens to endure cramped, sweat-filled commutes, then that veneer of civility may only be a superficial smile plastered on the surface.”

Whenever I ask AI to create a meme about the future and blockchain, it always ends up being the most hardcore cyberpunk 😁
#meme #blockchain #cyberpunk #nostr #bitcoin #btc #ai

I hate my sleep problem. First, I stay awake for hours until morning, unable to sleep, and after I finally fall asleep, I can’t wake up for hours because I didn’t sleep enough. It’s terrifying to have so little control over my brain when it comes to something as basic as sleep.
“Solar Opposites” drags us into the adventures of an alien family on Earth. But the real intrigue comes from discovering The Wall in this series by the creators of Rick and Morty. The Wall is where abducted humans, shrunk by Yumyulack, build their own society filled with power games and tales of resistance. We witness the darker sides of human nature in this enclosed community. Each episode pulls me deeper into this society, transforming the show from just an animation to something thought-provoking and questioning. “Solar Opposites,” with its Rick and Morty-like absurdity and critical approach, totally captivates me. I liked it a lot👍🏻
👁️🗨️ #meme

The view of Hurricane Milton from the International Space Station is terrifying and mesmerizing
As more data falls into the hands of governments and malicious actors, the value of Nostr grows. In a world where data is increasingly vulnerable, Nostr’s importance as a secure and censorship-resistant platform becomes even more critical.
Day by day…
Does it really take CEX exchanges ripping people off for volumes on DEXs to increase and the arbitrage differences there to decrease?
#dex
Iran and Israel taking turns to announce where they’ll strike next feels more like a strategy game than actual conflict. Each side moves like they’re saying, “It’s my turn now.” First, Iran: “This time, I’m hitting that base.” Then Israel: “Alright, I’m targeting this facility.” It’s more like they’re playing Civilization than engaging in real warfare. 🤦🏼♂️

Current Crypto Security and SHA-256
SHA-256 is a cryptographic hash function that underpins the security of Bitcoin and many other cryptocurrencies. It transforms data into a fixed-size output that is nearly impossible to reverse or find two different inputs with the same hash. For today’s classical and supercomputers, breaking SHA-256 would take longer than the lifespan of the universe, making it extremely secure at present.
The Rise of Quantum Computers and Their Threat Potential
Quantum computers offer exponential speedups over classical computers for certain tasks. Algorithms like Grover’s can theoretically reduce the breaking process of SHA-256 from 2^256 to 2^128 possibilities. However, this is still a vast number and beyond the capabilities of today’s quantum computers. Therefore, SHA-256 remains unbreakable with current quantum technology.
Future Scenario and Quantum-Resistant Cryptography
As quantum computing evolves, cryptocurrencies will need quantum-resistant security. Cryptographic methods such as lattice-based, code-based, and hash-based algorithms are being developed to counter potential quantum threats. In the future, cryptocurrencies can transition to these algorithms to ensure their security.
Algorithm Complexity and System Impact
Quantum-resistant algorithms are more complex than classical methods, requiring more processing power, larger data sizes, and increased energy consumption. This could lead to larger signatures and transaction data, impacting processing time and costs. However, as technology advances, these complexities are expected to become less of an issue.
Technological Progress and Future Adaptability
As computing power, storage capacity, and network infrastructure continue to advance, the additional load from quantum-resistant algorithms will be manageable. Cryptography and blockchain communities will develop optimizations and solutions to facilitate this transition.
Conclusion
Cryptocurrencies using SHA-256 are secure today, and quantum computers do not pose an immediate threat. However, as quantum technology advances, cryptocurrencies will adapt by shifting to quantum-resistant algorithms. Future technological progress and adaptation strategies will ensure that crypto assets remain secure while minimizing performance losses.
#Blockchain #SHA256 #QuantumComputing #Cryptography #CryptoSecurity #QuantumThreat #Cybersecurity #PostQuantum #Decentralization #Cryptocurrency #DigitalSecurity #QuantumResistant #btc #nostr #bitcoin #zk

The brain is truly fascinating. During the day, when we recall the past, it tends to highlight our pleasant memories, filling us with a sense of peace. Yet, as soon as we lie down to sleep, it brings forth our most embarrassing memories, robbing us of sleep. It’s almost as if the brain’s existence is like a form of natural schizophrenia.
This duality can be explained from an evolutionary perspective. Our brain has a tendency to suppress negative memories over time and emphasize positive ones, a phenomenon known as “positive illusion.” This mechanism might have evolved to protect our mental well-being and to maintain our motivation for survival. Constantly dwelling on traumatic or negative events could lead to chronic stress, which would lower our chances of survival. By highlighting the positive, the brain helps us stay resilient, and this sense of nostalgia is further reinforced by the release of hormones such as serotonin and oxytocin, which enhance feelings of warmth and tranquility.
On the other hand, the brain’s tendency to bring up shameful memories just before sleep can also be traced back to evolutionary functions. The moments before sleep involve a shift to alpha and theta brainwave states, where our connection with the subconscious becomes more pronounced. The brain might be presenting these memories to process them, ensuring that we don’t repeat socially risky behaviors in the future. Especially before important days or in moments of stress, this might serve as a preparatory process, allowing us to learn from past mistakes.
Additionally, since moments before sleep or before an important day tend to be more anxiety-inducing, the brain’s focus on past embarrassing events could be an attempt to rehearse avoiding similar situations, even though in modern life this mechanism often becomes counterproductive…
Sometimes going back to old songs feels like a nostalgic therapy

What is Post-Quantum Cryptography and Why is it Important?
Post-quantum cryptography refers to encryption techniques designed to be secure even against the power of quantum computers. Current encryption methods such as RSA, DSA, and ECC rely on mathematical problems that are practically impossible for classical computers to solve. However, quantum computers have the potential to break these codes quickly. As a result, post-quantum cryptography focuses on using mathematical problems that even quantum computers find incredibly difficult to solve.
Alice and Bob’s Post-Quantum Security Adventure
To illustrate, let’s revisit our classic characters, Alice and Bob. Alice wants to send a secure message to Bob, but she knows that there’s a risk of Eve, a malicious eavesdropper equipped with a quantum computer, intercepting the message. Alice needs to use post-quantum encryption techniques to ensure her communication remains secure.
1. Lattice-Based Cryptography
- Scenario: Alice decides to use lattice-based cryptography to send a post-quantum secure message to Bob.
- How It Works: In lattice-based cryptography, Alice represents her message as a point within a large, multi-dimensional grid (lattice). She then sends Bob a "short vector" that helps him locate the correct point within this grid, allowing him to decode the message.
- Alice’s Steps:
1. Constructs a large, multi-dimensional lattice and encodes her message as a point within this grid.
2. Encrypts this point with a special key and sends it, along with a "short vector," to Bob.
- Bob’s Steps:
1. Uses the short vector and the key to navigate the lattice and find Alice’s original message.
- Eve’s Challenge: Even with a quantum computer, Eve faces an overwhelming mathematical challenge to decode the message. The complexity of the lattice makes it virtually impossible to determine the correct point without the proper vector and key.
2. Code-Based Cryptography
- Scenario: Alice and Bob use a code-based encryption technique to communicate.
- How It Works: Alice encodes her message using a random error-correcting code and sends it to Bob. While Bob has the necessary key to correct these errors, Eve cannot decipher the message without it.
- Alice’s Steps:
1. Takes her message and encodes it with random errors using a code-based encryption technique.
2. Sends the encoded message to Bob.
- Bob’s Steps:
1. Uses his secret decoding key to correct the errors and extract Alice’s original message.
- Eve’s Challenge: Without the error-correction key, Eve faces an insurmountable task in decoding Alice’s message, even with a quantum computer.
3. Hash-Based Signatures
- Scenario: Alice needs to send a digitally signed message to Bob to ensure its authenticity.
- How It Works: Alice generates a hash (a condensed representation) of her message and then uses her private key to create a digital signature. This signature, along with the original message, is sent to Bob, who can verify its authenticity using Alice's public key.
- Alice’s Steps:
1. Creates a hash of her message.
2. Signs the hash using her private key and sends both the message and the signature to Bob.
- Bob’s Steps:
1. Uses Alice’s public key to verify that the signature matches the hash, ensuring the message’s authenticity.
- Eve’s Challenge: The hash function is designed to be computationally infeasible to reverse, even for quantum computers, meaning Eve cannot forge Alice’s signature or tamper with the message.
Quantum Computers’ Cracking Abilities: Shor and Grover Algorithms
- Shor’s Algorithm: This quantum algorithm efficiently factors large numbers, which would compromise RSA and ECC encryption methods.
- Grover’s Algorithm: It accelerates the search process for finding pre-images of hash functions, but post-quantum cryptographic methods are constructed to withstand even this enhanced capability.
Hybrid Encryption: A Practical Approach
In practical applications, Alice and Bob may use a combination of post-quantum algorithms alongside traditional encryption methods to maximize security:
- Alice uses a post-quantum algorithm to encrypt a shared secret key.
- She then uses a classical encryption method, like AES, to encrypt the actual message using that key.
This hybrid approach provides protection against both current classical threats and future quantum threats.
The Real-World Importance and Applications of Post-Quantum Cryptography
Post-quantum cryptography is not just a theoretical concept; it has started to be implemented in various applications* . From financial transactions to secure communication, integrating post-quantum algorithms into existing systems offers early protection against the emerging quantum threat. This shift is essential to safeguard data against the possibility of future quantum attacks.
Conclusion
Post-quantum cryptography represents a critical advancement in safeguarding data against the potential dangers posed by quantum computers. Lattice-based, code-based, and hash-based encryption techniques provide layers of security that are designed to withstand even the most advanced quantum attacks. Through Alice and Bob’s journey, we've explored how these post-quantum algorithms function and why they are so vital for future-proofing our digital security.
As the capabilities of quantum computers continue to grow, the adoption of post-quantum cryptographic techniques will be an essential step in ensuring that our information remains protected. This isn't just a temporary fix but a foundational element in securing a future where quantum threats are a reality.
* For example: mullvad vpn, which I love to use, uses these algorithms practically. Not advertising
#privacy #cryptography #freeinternet #nostr #edu #postquantum #xmr #monero #btc #bitcoin
These streaming platforms’ subscription systems have gone to shit
On Nostr, there are now replyguys who respond even to the replies of other replyguys🤦🏼♂️ I wonder if these people have a rational reason for their existence that I’m unaware of
#nostr #asknostr
:,) #meme #memes #love


Similarities Between Religions and Blockchains
When we consider the similarities between religions and blockchains, it’s fascinating to discover how they share some intriguing commonalities.
First of all, both systems revolve around a “type of book.” Religions center around sacred texts, while blockchains create their own “ledgers” (blockchain records). Religious teachings are often found in holy books, and although these books may have been written at different times, they essentially contain compatible messages. Similarly, blockchains maintain records in each block, which are linked over time to form a chain. Both aim for a sense of continuity and coherence.
Throughout history, religions have given rise to many versions, with some “forking” the original texts to create new interpretations🤣. In the same way, blockchains evolve through various “forks.” A group of developers might take an existing blockchain and create a new version. This is like a group of devoted followers creating a “new commentary” on an old religion.
#btc #bitcoin #nostr #religion #blockchain #meme #memes
In Nostr, the ease of increasing follower count (as easy as writing a software bot) makes it gradually lose its significance. The self-censorship that follower counts induce on traditional social media disappears here. This enables us to use social media more freely. Simplicity can sometimes lead to insignificance, but this insignificance can liberate us. It creates a space where we can share our thoughts without being concerned about follower numbers.
#nostr #grownostr #damus

How Are Atomic Swaps Secure Even Though They Are Off-Chain?
On-Chain vs. Off-Chain Swaps:
Atomic swaps can occur both on-chain and off-chain. Off-chain swaps happen outside the main blockchain, which speeds up transactions and reduces the load on the network. However, the primary concern is how to ensure security in off-chain transactions. Off-chain atomic swaps are often executed through second-layer solutions like the Lightning Network.
In off-chain swaps, security is primarily maintained using Hashed Time-Locked Contracts (HTLCs) and cryptographic verifications. HTLCs are crucial in both on-chain and off-chain atomic swaps.
Technical Details:
What Are HTLCs?
HTLCs are smart contracts that impose conditions based on time and cryptographic hash values. They ensure that a transaction will only complete if a specific encrypted value (hash) is revealed within a set time frame. If the value is not revealed, the transaction is canceled, and the funds are returned. These two mechanisms maintain security.
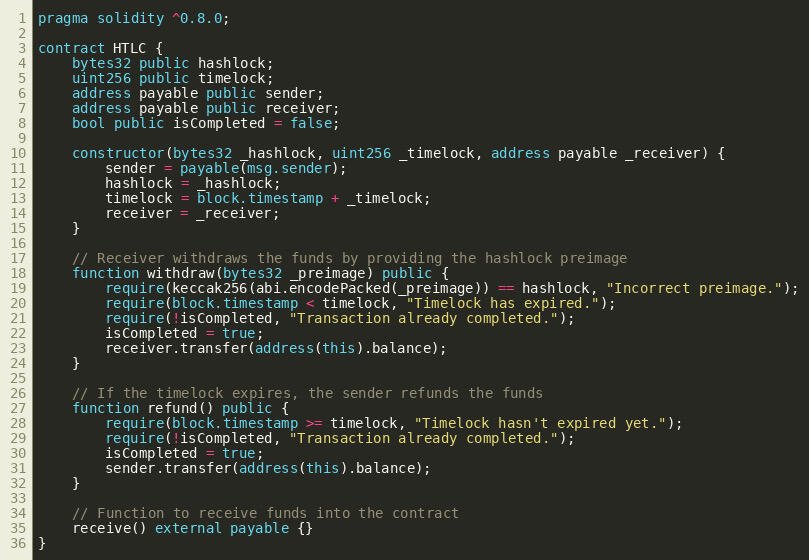
uploaded as image HTLC code example
What’s Happening Here?
1. Contract Creation: Alice initiates the contract to swap with Bob. Alice creates a hash value (hashlock), and Bob needs to unlock it by providing the preimage. There is also a time limit (timelock) defined; if the swap is not completed in time, Alice can retrieve her funds.
2. Withdraw Function: Bob unlocks Alice’s funds by providing the correct preimage. The contract checks whether the preimage matches the hashed value using keccak256 hashing.
3. Refund Function: If Bob fails to provide the preimage within the time limit, Alice can call the refund function to retrieve her funds.
The security of this system relies on the cryptographic hash lock and the time-bound conditions. Both parties must act within the time constraints and with the correct information, or the funds will be refunded, ensuring no loss of assets.
Additional Security in Off-Chain Atomic Swaps:
In off-chain atomic swaps, additional security is ensured through second-layer solutions like the Lightning Network. Transactions happen outside the main blockchain and are finalized without being recorded on-chain. Security is ensured using multi-signature wallets and signed data that validate every step of the process.
Example: When Alice and Bob perform an atomic swap through the Lightning Network, they open payment channels. These channels ensure that funds cannot be moved without both parties’ signatures. In case of a dispute, the payment channels are closed, and the funds revert to the main blockchain, guaranteeing security.
#btc #bitcoin #xmr #monero #eth #ethereum #evm #contract #solidity #code #atomic #swap #edu