final@zeuspay.com
View quoted note →

Final
final@stacker.news
npub1hxx7...g75y
Digital forensics and security specialist part of the GrapheneOS project.
Posts my own and not endorsed by my employer. AI slop and Nostr DMs ignored.
Matrix: f1nal:grapheneos.org
Finally working to go all in on using ZEUS.
Proud to say my 'Never Went to Black Hat' award is looking very shiny right now.
As our fully local text to speech engine is deployed in GrapheneOS soon, this will be the first of hopefully many major usability advancements in GrapheneOS for the year and next. With the OEM partnership developing and later generation flagship hardware providing more of what GrapheneOS needs for features, improving usability and accessibility will help for the influx of new users we will hope to welcome.
It is a good time to remind you that GrapheneOS is hiring remote developers. We have been for a while:
Hiring | GrapheneOS
This is a tablet PC with Cellebrite UFED, a mobile forensics acquisition software. Users plug a target device into it where it then will attempt to extract as much data on the device as possible. The software on the laptop is Physical Analyser which is for forensic analysis.
This video is dated, and Cellebrite UFED's UI, logo and capabilities have changed a lot since the video was released. This tool is also not exclusive to UK law enforcement and there are also competitor solutions, which many countries around the world use plus the competitors.
Cellebrite sell a variant of this product named Cellebrite Premium. The difference to standard UFED and Premium is that Premium comes with wider device extraction support through zero-day exploits. As described it also allows extraction of vulnerable devices that are locked.

 This business model is not exclusive. XRY Pro (MSAB) and GrayKey (Magnet Forensics) are other exclusive forensic tools. Cellebrite are the second-oldest of the three companies (on joining the forensics market) but are one of the most capable thanks to their funding and location.
How and if these tools are able to extract your device's data depends on:
- The device you are using
- The installed OS and version
- The lock state of the device
- Configured security settings of the device
- Strength of your phone's unlock credential
For a locked device exploiting security vulnerabilities is required to extract data almost all of the time. There are two different device lock states on Android and iOS: After first unlock (AFU, Hot) and before first unlock (BFU, Cold). This is due to how encryption works.
Modern Android and iOS encrypt all users' data by default with keys derived from the user's credentials. When a device is unlocked once, data is no longer encrypted at rest and is accessible during that boot session. When a device is BFU, all sensitive data is at rest.
Data not being at rest provides more OS attack surface to exploit bypassing lock screens or other measures and access to the data without needing the original PIN/password to decrypt it. For BFU devices brute forcing is required to decrypt data first and the only data not encrypted is a minimal footprint of the OS used for unlocking the device and global OS configuration and metadata.
To make extraction impossible make sure your device is powered off and you use a secure, high-entropy passphrase before seizure. GrapheneOS provides a configurable, automatic inactivity reboot feature.
We also provide several other countermeasures to these tools as well. GrapheneOS locked devices as a whole is unsupported by Cellebrite.
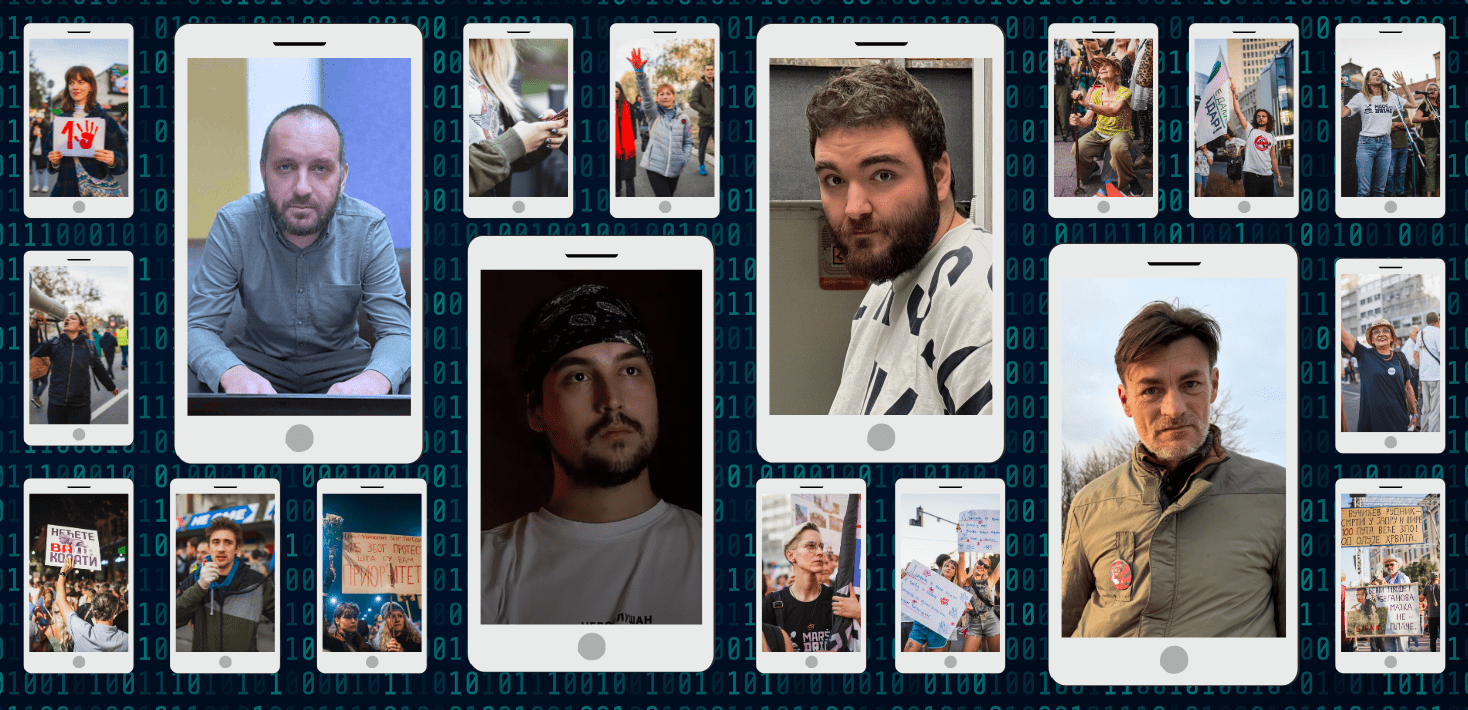
If you are an opposition activist in a high-risk country you should be concerned about potential attacks from such tools. They have been abused to target activists in numerous countries like Serbia and Jordan.
This business model is not exclusive. XRY Pro (MSAB) and GrayKey (Magnet Forensics) are other exclusive forensic tools. Cellebrite are the second-oldest of the three companies (on joining the forensics market) but are one of the most capable thanks to their funding and location.
How and if these tools are able to extract your device's data depends on:
- The device you are using
- The installed OS and version
- The lock state of the device
- Configured security settings of the device
- Strength of your phone's unlock credential
For a locked device exploiting security vulnerabilities is required to extract data almost all of the time. There are two different device lock states on Android and iOS: After first unlock (AFU, Hot) and before first unlock (BFU, Cold). This is due to how encryption works.
Modern Android and iOS encrypt all users' data by default with keys derived from the user's credentials. When a device is unlocked once, data is no longer encrypted at rest and is accessible during that boot session. When a device is BFU, all sensitive data is at rest.
Data not being at rest provides more OS attack surface to exploit bypassing lock screens or other measures and access to the data without needing the original PIN/password to decrypt it. For BFU devices brute forcing is required to decrypt data first and the only data not encrypted is a minimal footprint of the OS used for unlocking the device and global OS configuration and metadata.
To make extraction impossible make sure your device is powered off and you use a secure, high-entropy passphrase before seizure. GrapheneOS provides a configurable, automatic inactivity reboot feature.
We also provide several other countermeasures to these tools as well. GrapheneOS locked devices as a whole is unsupported by Cellebrite.
If you are an opposition activist in a high-risk country you should be concerned about potential attacks from such tools. They have been abused to target activists in numerous countries like Serbia and Jordan.

 Despite if a business claims this use of their product like this is unauthorised, it doesn't change the fact that they will be used like this again, that they don't know about it until after it has violated someone's rights and that the security vulnerabilities remain unpatched.
GrapheneOS provides an auto-reboot to put data at rest, a USB-C port control to disable data transfer or the port entirely when booted into the OS, clearing sensitive data of memory and exploit protection features.
View quoted note →
Despite if a business claims this use of their product like this is unauthorised, it doesn't change the fact that they will be used like this again, that they don't know about it until after it has violated someone's rights and that the security vulnerabilities remain unpatched.
GrapheneOS provides an auto-reboot to put data at rest, a USB-C port control to disable data transfer or the port entirely when booted into the OS, clearing sensitive data of memory and exploit protection features.
View quoted note →



The Citizen Lab
From Protest to Peril: Cellebrite Used Against Jordanian Civil Society - The Citizen Lab
Through a multi-year investigation, we find that the Jordanian security apparatus has deployed forensic extraction products manufactured by Cellebr...

Amnesty International
Serbia: Authorities using spyware and Cellebrite forensic extraction tools to hack journalists and activists
Serbian authorities are using spyware and Cellebrite forensic extraction tools to hack journalists and activists in a surveillance campaign.
You may have been aware of my posts about TTS / SST. Heres more info:
View quoted note →
Seeing Proton get heat on social media for their marketing again so lets repost this. Treat these email services for what they are: Alternatives to Gmail or Outlook with a security perspective and automated encryption features.
Yes, people on social media can't read, but IMO they should approach their service in a different way ("A reasonably secure email provider" is my suggestion) If they don't want people ratioing them all the time... Most of these people getting the wrong answer is because their site can be pretty ambiguous about the technical details without searching a few pages deep for it. Posteo is an email provider that does openly clarify they can be compelled to intercept incoming emails in a better way than how Proton says it.
Still doesn't mean these services are a bad thing though.
View quoted note →
Late to post about this but the security preview variant of this release fixes SIX **CRITICIAL** CVEs that will not be fixed elsewhere for a while except in #GrapheneOS because security patches are not included into an Android Security Bulletin until around 3-4 months after their release.
- Critical: CVE-2026-0039, CVE-2026-0040, CVE-2026-0041, CVE-2026-0042, CVE-2026-0043, CVE-2026-0044
OEMs do not deliver security patches in a timely manner. In a rare case it is sometimes only done in part, and often will only do so after the ASB is released. That dangerously long period of security vulnerabilities being known and unlatched is unacceptable.
View quoted note →
Last two Vanadium updates provided some functionality improvements:
The upstream motion sensors toggle for the browser is improved with a per-site toggle for the sensors per site (Vanadium already had the global toggle disabled by default).
Our inbuilt content filtering also adds support for additional supplementary language/regional content filters. Users with a set language will get EasyList filters plus the filter of their respective language. This supports Arabic, Bulgarian, Spanish, French, German, Hebrew, Indian, Indonesian, Italian, Korean, Lithuanian, Latvian, Dutch, Nordic, Polish, Portuguese, Romanian, Russian, Vietnamese and Chinese. #GrapheneOS
View quoted note →
What this means that notifications will work for users not wishing to use play services sandboxed or otherwise.
Most android apps do notifications via FCM, which is Google's, and depends on a Play services implementation. If you ever wonder why app notifications barely work on AOSP distributions without Google services then now you know.
By using an app like Sunup (on Accrescent) you can use Mozilla's notification service via UnifiedPush for apps that use UnifiedPush notifications - such as this one.
Tell your developers to support notifications without Google.
View quoted note →
The regressions with the Terminal app originate from the stock OS, including the VPN issue. The VM data also breaks and data can't be recovered at times. Don't store sensitive data without backups or run anything for production but feel free to try it out.
We do improve the Terminal app in a few ways and these fixes is something we need to look into but because it's still an experimental developer option it's priority isn't so high. If the stock OS deals with it first then it's less work on our plate. Desktop Mode needs to be first for all the cool stuff to happen.
What users see now will likely be very different to what our plans are should we be able to execute them. We don't want to just have a terminal but rather a VM manager capable of running other operating systems and GUI apps. Debian alone isn't desirable for our use case and we'd want a hardened OS like secureblue instead (ARM builds is beta). Virtualization could be extended to GrapheneOS or individual apps too.
#GrapheneOS version 2026010800 released.
• raise declared patch level to 2026-01-05 which has been provided since we moved to Android 16 QPR2 in December due to Pixels shipping CVE-2025-54957 in December
• re-enable the system keyboard at boot if it's disabled
• switch to the system keyboard when device boots to the Safe Mode
• add "Reboot to Safe Mode" power menu button in Before First Unlock state to make Safe Mode much more discoverable for working around app issues such as a broken third party keyboard
• add workaround for upstream UsageStatsDatabase OOM system_server crash
• add workaround for upstream WindowContext.finalize() system_server crash
• disable buggy upstream disable_frozen_process_wakelocks feature causing system_server crashes for some users
• Sandboxed Google Play compatibility layer: fix phenotype flags not working in Play services clients
• Sandboxed Google Play compatibility layer: add MEDIA_CONTENT_CONTROL as a requested permission for Android Auto as part of our toggles for it to avoid needing to grant the far more invasive notification access permission
• Sandboxed Google Play compatibility layer: extend opt-in Android Auto Bluetooth support to allow A2dpService.setConnectionPolicy() to fix Bluetooth functionality (previously worked around with a GmsCompatConfig update avoiding a crash)
• switch to new upstream PackageInstallerUI implementation added in Android 16 QPR2 and port our changes to it
• update SQLite to 3.50.6 LTS release
• add an extra layer of USB port protection on 10th gen Pixels based on upstream functionality to replace our USB gadget control which was causing compatibility issues with the Pixel 10 USB drivers
• allow SystemUI to access NFC service on 10th gen Pixels to fix the NFC quick tile • disable the upstream Android USB data protection feature since it conflicts with our more advanced approach and causes issues
• issue CHARGING_ONLY_IMMEDIATE port control command in more cases
• fix an issue in our infrastructure for spoofing permission self-checks breaking automatically reading SMS one-time codes for certain apps
• add workaround for upstream KeySetManagerService system_server crash causing a user to be stuck on an old OS version due to it causing a boot failure when booting a the new OS version after updating
• wipe DPM partition on 10th gen Pixels as part of installation as we do on earlier Pixels since it's always meant to be zeroed on production devices
• Settings: disable indexing of the unsupported "Parental controls" setting which is not currently available in AOSP
• Settings: disable redundant indexing of widgets on lockscreen contents which is already indexed another way
• skip all pseudo kernel crash reports caused by device reboot to avoid various false positive crash reports
• Vanadium: update to version 143.0.7499.192.0
All of the Android 16 security patches from the current January 2026, February 2026, March 2026, April 2026, May 2026 and June 2026 Android Security Bulletins are included in the 2026010801 security preview release. List of additional fixed CVEs:
• High: CVE-2025-32348, CVE-2025-48561, CVE-2025-48615, CVE-2025-48630, CVE-2025-48641, CVE-2025-48642, CVE-2025-48644, CVE-2025-48645, CVE-2025-48646, CVE-2025-48649, CVE-2025-48652, CVE-2025-48653, CVE-2026-0014, CVE-2026-0015, CVE-2026-0016, CVE-2026-0017, CVE-2026-0018, CVE-2026-0020, CVE-2026-0021, CVE-2026-0022, CVE-2026-0023, CVE-2026-0024, CVE-2026-0025
Releases | GrapheneOS