Would be awesome
View quoted note →

nym
nym@primal.net
npub1hn4z...htl5

There you are.
View quoted note →
Quake III Arena in your web browser
originally posted at 
Quake III Arena Demo
Stacker News
Quake III Arena in your web browser \ stacker news
@nym stacked 525 sats posting https://thelongestyard.link/q3a-demo/ [2 comments]
Sleep Baseball
 Northwoods Baseball Sleep Radio is a full-length fake baseball game. There is no yelling, no loud commercials, no weird volume spikes. Fans call it "baseball radio ASMR".
It is the perfect podcast for sleeping or relaxing, if you're into that kind of thing.
Available wherever you get your podcasts.
"You don't listen to it, you listen through it"

originally posted at
Northwoods Baseball Sleep Radio is a full-length fake baseball game. There is no yelling, no loud commercials, no weird volume spikes. Fans call it "baseball radio ASMR".
It is the perfect podcast for sleeping or relaxing, if you're into that kind of thing.
Available wherever you get your podcasts.
"You don't listen to it, you listen through it"

originally posted at 
sleepbaseball.com
The Northwoods Baseball Radio Network
Is On The Air.
Stacker News
Sleep Baseball \ stacker news
Northwoods Baseball Sleep Radio is a full-length fake baseball game. There is no yelling, no loud commercials, no weird volume spikes. Fans call it...
More than 1,100 inmates help Cal Fire battle fires for less than $30 a day
https://abc7.com/post/inmates-work-less-30-day-help-cal-fire-battle-eaton-palisades-fires/15813591/
Sal Almanza has worked 24-hour shifts in grueling terrain, cutting fire lines and hauling away brush trying to keep ahead of fires that have devastated several Los Angeles neighborhoods. But when the fires are finally out, he won't be going back to his family: He'll be returning to the prison "fire camp" where he's serving time for drunken driving that injured someone.
"I wanted to do something positive while I was here," the 42-year-old said. "Something that would contribute back to the community and just help me feel better about my situation and right the wrongs that I did."

Over 1,100 California inmates have been working around the clock in challenging conditions - including howling winds and toxic smoke - to help Cal Fire battle the Eaton and Palisades fires, the largest and most destructive of about a half-dozen fires that burned in the Los Angeles area in the past two weeks.
They become firefighters for the chance to cut time off their sentences, to get outside the prison walls and for training that might help them land a job once they're out.
But some say the inmates, many earning less than $30 a day for their efforts, deserve better after risking their lives: to be paid on par with other firefighters.
originally posted at 
Stacker News
deleted by author \ stacker news
deleted by author
Silver Spoon
 Silver Spoon" is an allegorical tale that critiques the evolution of governmental control and societal organization. The story contrasts an idealized past of voluntary cooperation and individual freedom with the gradual emergence of controlling systems, symbolized by magical utensils (Silver Spoon, Jade Chopsticks, Golden Fork, and Bronze Ladle). Through these symbols, it illustrates how authority structures establish themselves through initial benefits before expanding into oppressive control systems. The narrative explores themes of surveillance, monetary control, propaganda, and the loss of personal freedoms, while questioning how societies surrender autonomy in exchange for promised security and order.

originally posted at
Silver Spoon" is an allegorical tale that critiques the evolution of governmental control and societal organization. The story contrasts an idealized past of voluntary cooperation and individual freedom with the gradual emergence of controlling systems, symbolized by magical utensils (Silver Spoon, Jade Chopsticks, Golden Fork, and Bronze Ladle). Through these symbols, it illustrates how authority structures establish themselves through initial benefits before expanding into oppressive control systems. The narrative explores themes of surveillance, monetary control, propaganda, and the loss of personal freedoms, while questioning how societies surrender autonomy in exchange for promised security and order.

originally posted at 

Silver Spoon
"Silver Spoon" is an allegorical tale that critiques the evolution of governmental control and societal organization. The story contrasts an ideali...
Stacker News
Silver Spoon \ stacker news
Silver Spoon" is an allegorical tale that critiques the evolution of governmental control and societal organization. The story contrasts an idealiz...
WireGuard at Modal: Static IPs for Serverless Containers
 At Modal, we built a high-availability, Go-based VPN proxy called vprox.
This is a deployment of WireGuard, so it operates on Layer 3 (IP) of the network stack and allows us to funnel outbound traffic from containers around the world through static IPv4 addresses. In the event of a single-node failure, its static IPs are associated with other proxy nodes, and containers reconnect within seconds.
The year is 2024, and you are deciding on a serverless cloud platform. You stumble upon Modal. Run pip install modal, write a short Python function, and modal deploy it. Amazing, now you’ve got a cron job and API endpoint in the cloud, within seconds.
Modal functions run on hardware around the world, in dozens of regions across multiple cloud providers. This is how we optimize the prices on your compute and scale dynamically to meet demand. It’s all to make developers happy, since now you don’t have to think about this stuff. (We get it, we’re infrastructure engineers.)
But now let’s say you want to connect your serverless function to your MongoDB cloud database, and it requires a specific IP access list. Uh oh…

Usually, with a traditional provider you’d deploy some VMs and assign them a static IP address or two, then distribute them across your machines and add those to your access list. So now your application runs on cloud hosts at some particular IPs, like 20.21.20.21. Only these machines can access your MongoDB database, and no one else can around the world.
But if you’re running a serverless computing workload, which can not only run in any data center around the world, but also scale up and down… you won’t know what IP address your code is running on! So that access list would have thousands of entries and will be constantly changing, which really isn’t going to cut it.
Plus, Modal has an isolated container runtime that lets us share each host’s CPU and memory between workloads. If a host has one IP, your container and another customer’s container on that host would have the same IP, so that bypasses the security of your access list.
originally posted at
At Modal, we built a high-availability, Go-based VPN proxy called vprox.
This is a deployment of WireGuard, so it operates on Layer 3 (IP) of the network stack and allows us to funnel outbound traffic from containers around the world through static IPv4 addresses. In the event of a single-node failure, its static IPs are associated with other proxy nodes, and containers reconnect within seconds.
The year is 2024, and you are deciding on a serverless cloud platform. You stumble upon Modal. Run pip install modal, write a short Python function, and modal deploy it. Amazing, now you’ve got a cron job and API endpoint in the cloud, within seconds.
Modal functions run on hardware around the world, in dozens of regions across multiple cloud providers. This is how we optimize the prices on your compute and scale dynamically to meet demand. It’s all to make developers happy, since now you don’t have to think about this stuff. (We get it, we’re infrastructure engineers.)
But now let’s say you want to connect your serverless function to your MongoDB cloud database, and it requires a specific IP access list. Uh oh…

Usually, with a traditional provider you’d deploy some VMs and assign them a static IP address or two, then distribute them across your machines and add those to your access list. So now your application runs on cloud hosts at some particular IPs, like 20.21.20.21. Only these machines can access your MongoDB database, and no one else can around the world.
But if you’re running a serverless computing workload, which can not only run in any data center around the world, but also scale up and down… you won’t know what IP address your code is running on! So that access list would have thousands of entries and will be constantly changing, which really isn’t going to cut it.
Plus, Modal has an isolated container runtime that lets us share each host’s CPU and memory between workloads. If a host has one IP, your container and another customer’s container on that host would have the same IP, so that bypasses the security of your access list.
originally posted at 

Modal
WireGuard at Modal: Static IPs for Serverless Containers
Now your Modal containers around the world can have static outbound IPs. Featuring WireGuard, policy-based routing, and NAT.
Stacker News
WireGuard at Modal: Static IPs for Serverless Containers \ stacker news
At Modal, we built a high-availability, Go-based VPN proxy called vprox. This is a deployment of WireGuard, so it operates on Layer 3 (IP) of the n...
Private Keys in the Fortigate Leak
A few days ago, a download link for a leak of configuration files for Fortigate/Fortinet devices was posted on an Internet forum. It appears that the data was collected in 2022 due to a security vulnerability known as CVE-2022-40684. According to a blog post by Fortinet in 2022, they were already aware of active exploitation of the issue back then. It was first reported by heise, a post by Kevin Beaumont contains further info.
What has not been widely recognized is that this leak also contains TLS and SSH private keys. As I am developing badkeys, a tool to identify insecure and compromised keys, this caught my attention. (The following analysis is based on an incomplete subset of the leak. I may update the post if I get access to more complete information.)
They also include corresponding certificates and keys in OpenSSH format. As you can see, these private keys are encrypted. However, above those keys, we can find the encryption password.
The password line contains a Base64 string that decodes to 148 bytes. The first four bytes, padded with 12 zero bytes, are the initialization vector. The remaining bytes are the encrypted payload. The encryption uses AES-128 in CBC mode. The decrypted passwords appear to be mostly hex numbers and are padded with zero bytes - and sometimes other characters. (I am unaware of their meaning.)
In case I lost you here with technical details, the important takeaway is that in almost all cases, it is possible to decrypt the private key. (I may share a tool to extract the keys at a later point in time.)
The use of a static encryption key is a known vulnerability, tracked as CVE-2019-6693. According to Fortinet's advisory from 2020, this was "fixed" by introducing a setting that allows to configure a custom password.
originally posted at 
Private Keys in the Fortigate Leak - Hanno's blog
Stacker News
deleted by author \ stacker news
deleted by author [1 comment]
Football, Fiat and the Bitcoin Renaissance
 Does Football Still Feel the Same?
Close your eyes for a moment and think back to when you first fell in love with football. What was it that pulled you in and wouldn’t let go? Was it the roar of the crowd as your team netted a stoppage-time winner? The thrill of an underdog beating the odds? Or maybe it was simpler—the chants, the rivalries, the raw, unfiltered chaos of the game.
Now open your eyes. Does football still feel like that?

You know it doesn’t. The spark is still there but the magic feels muted. Matches feel more like polished products, rivalries are starting to feel manufactured and even the moments of brilliance seem a little…hollow.
You hear the pundits blame it on “greedy owners” or “commercialisation of the game,” but football has always been tied to money. From the grand stadiums to the global superstars, wealth has always flowed to the game we love. So, what’s really wrong?
originally posted at
Does Football Still Feel the Same?
Close your eyes for a moment and think back to when you first fell in love with football. What was it that pulled you in and wouldn’t let go? Was it the roar of the crowd as your team netted a stoppage-time winner? The thrill of an underdog beating the odds? Or maybe it was simpler—the chants, the rivalries, the raw, unfiltered chaos of the game.
Now open your eyes. Does football still feel like that?

You know it doesn’t. The spark is still there but the magic feels muted. Matches feel more like polished products, rivalries are starting to feel manufactured and even the moments of brilliance seem a little…hollow.
You hear the pundits blame it on “greedy owners” or “commercialisation of the game,” but football has always been tied to money. From the grand stadiums to the global superstars, wealth has always flowed to the game we love. So, what’s really wrong?
originally posted at 

Football, Fiat and the Bitcoin Renaissance
Remember when football made your heart race? When rivalries felt real, players lit up the pitch with genius and every match was a story waiting to ...
Stacker News
Football, Fiat and the Bitcoin Renaissance \ stacker news
Does Football Still Feel the Same? Close your eyes for a moment and think back to when you first fell in love with football. What was it that pulle...
Advanced Python Development Workflow in Emacs
Emacs is not just an editor — it’s an extensible platform for crafting highly personalized development environments. With tools like company, yasnippet, lsp-mode and dap-mode, Emacs transforms into a feature-rich Python IDE capable of competing with PyCharm or VS Code.
This guide explores how to evolve Emacs into a robust Python IDE. Whether you’re writing simple scripts or managing large-scale projects, you’ll find a setup that aligns with your engineering needs and reflects the power of Emacs customization.
The purpose of this guide is to meticulously explore how Emacs can be transformed into a advanced Python IDE. This is not a universal manual intended for everyone — it is deeply tailored to my specific needs, preferences, and engineering rigor. Throughout this document, I aim to combine practical usability with transparent configuration, balancing power and simplicity.
This guide reflects my personal journey in creating an IDE that meets my own standards of excellence. Could Emacs be made “better”? Absolutely, because the concept of “better” is always contextual. Could someone else choose different tools than I did? Certainly. The tools I selected represent the choices I made based on my criteria and understanding, which I will detail throughout the guide.
At its core, this is a collection of my thoughts, experiments, and findings — a snapshot of my current understanding of how to make Emacs the ultimate Python development environment. While it may not suit everyone, I hope it inspires others to refine their workflows and explore the potential of Emacs as a highly customizable IDE.
A note on some conscious exclusions: I do not use use-package in my personal Emacs configuration and this guide. While it may be a popular choice in the Emacs community, I have not found it particularly valuable for my workflow. I manage my configuration manually, and this approach works perfectly for me. If you are a use-package user, you might need to adapt discussed configuration to fit your own setup — I leave this as an exercise for you.
originally posted at 
Serghei's Blog
Advanced Python Development Workflow in Emacs
This guide explores how to evolve Emacs into a robust Python IDE. Whether you’re writing simple scripts or managing large-scale projects, you’l...
Stacker News
Advanced Python Development Workflow in Emacs \ stacker news
Emacs is not just an editor — it’s an extensible platform for crafting highly personalized development environments. With tools like company, y...
A New type of web hacking technique: DoubleClickjacking
 “Clickjacking” is becoming less practical as modern browsers set all cookies to “SameSite: Lax” by default. Even if an attacker site can frame another website, the framed site would be unauthenticated, because cross-site cookies are not sent. This significantly reduces the risk of successful clickjacking attacks, as most interesting functionality on websites typically requires authentication.
DoubleClickjacking is a new variation on this classic theme: instead of relying on a single click, it takes advantage of a double-click sequence. While it might sound like a small change, it opens the door to new UI manipulation attacks that bypass all known clickjacking protections, including the X-Frame-Options header, CSP's frame-ancestors and SameSite: Lax/Strict cookies. This technique seemingly affects almost every website, leading to account takeovers on many major platforms.

In simpler terms, DoubleClickjacking leverages the small gap between the start of a click and the end of the second click in multiple windows without utilizing any popunder tricks. It is a sleight of hand. Attackers load (or open) a new window for a legitimate seeming reason—like a “captcha verification,” for example. Then, just before the second click is pressed, the malicious site can quickly swap in a more sensitive window from the same browser session (e.g., an OAuth authorization prompt), effectively hijacking that second click. There are many ways to perform the “swap,” the most reliable and smooth method I found uses window.open.location.
One of the important pieces of this attack is exploiting the timing difference between mousedown and onclick events (favoring mousedown over click). The mousedown event fires immediately when the user presses the mouse button, while the click event waits for the complete click action so there is a few ms of delay we can siphon for the attack. One of the surprising things about doing it this way is it does not matter how slow or how fast the target double-clicks. favoring mousedown event handler allows exploiting this even for the fastest or slowest double clickers.
originally posted at
“Clickjacking” is becoming less practical as modern browsers set all cookies to “SameSite: Lax” by default. Even if an attacker site can frame another website, the framed site would be unauthenticated, because cross-site cookies are not sent. This significantly reduces the risk of successful clickjacking attacks, as most interesting functionality on websites typically requires authentication.
DoubleClickjacking is a new variation on this classic theme: instead of relying on a single click, it takes advantage of a double-click sequence. While it might sound like a small change, it opens the door to new UI manipulation attacks that bypass all known clickjacking protections, including the X-Frame-Options header, CSP's frame-ancestors and SameSite: Lax/Strict cookies. This technique seemingly affects almost every website, leading to account takeovers on many major platforms.

In simpler terms, DoubleClickjacking leverages the small gap between the start of a click and the end of the second click in multiple windows without utilizing any popunder tricks. It is a sleight of hand. Attackers load (or open) a new window for a legitimate seeming reason—like a “captcha verification,” for example. Then, just before the second click is pressed, the malicious site can quickly swap in a more sensitive window from the same browser session (e.g., an OAuth authorization prompt), effectively hijacking that second click. There are many ways to perform the “swap,” the most reliable and smooth method I found uses window.open.location.
One of the important pieces of this attack is exploiting the timing difference between mousedown and onclick events (favoring mousedown over click). The mousedown event fires immediately when the user presses the mouse button, while the click event waits for the complete click action so there is a few ms of delay we can siphon for the attack. One of the surprising things about doing it this way is it does not matter how slow or how fast the target double-clicks. favoring mousedown event handler allows exploiting this even for the fastest or slowest double clickers.
originally posted at 

Paulos Yibelo - Hacking Research
Paulos Yibelo - Hacking Research: DoubleClickjacking: A New Era of UI Redressing
data:blog.metaDescription
Stacker News
A New type of web hacking technique: DoubleClickjacking \ stacker news
“Clickjacking” is becoming less practical as modern browsers set all cookies to “SameSite: Lax” by default. Even if an attacker site can fr...
Is the World Becoming Uninsurable?
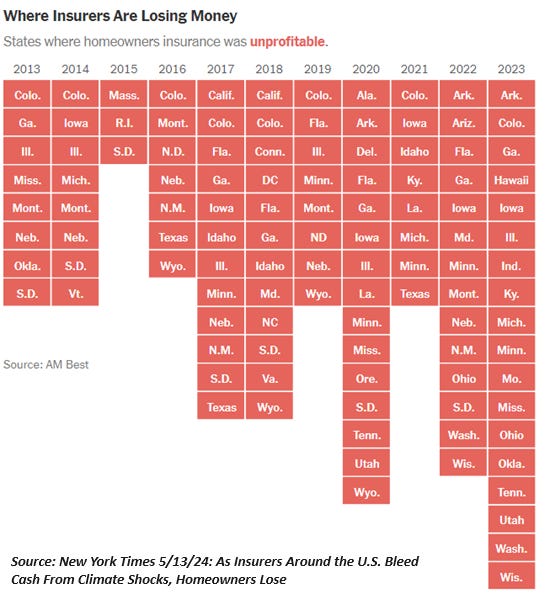 I ask the question, "is the world becoming uninsurable?" not as an expert on the insurance industry but as a homeowner who can no longer obtain hurricane insurance, and as an observer of long-term trends keenly interested in the way global risks pile up either unseen, denied or misinterpreted until it's too late to mitigate them.

This is not an abstraction, though many are treating it as a policy debate. As noted previously here, the insurance industry is not a charity, and insurers bear the costs that are increasing regardless of opinions and policy proposals. Insurers operate in the real world, and their decisions to pull out of entire regions, reduce coverage and increase premiums are all responses to soaring losses, a reality reflected in these charts.

originally posted at
I ask the question, "is the world becoming uninsurable?" not as an expert on the insurance industry but as a homeowner who can no longer obtain hurricane insurance, and as an observer of long-term trends keenly interested in the way global risks pile up either unseen, denied or misinterpreted until it's too late to mitigate them.

This is not an abstraction, though many are treating it as a policy debate. As noted previously here, the insurance industry is not a charity, and insurers bear the costs that are increasing regardless of opinions and policy proposals. Insurers operate in the real world, and their decisions to pull out of entire regions, reduce coverage and increase premiums are all responses to soaring losses, a reality reflected in these charts.

originally posted at 

Is the World Becoming Uninsurable?
You are receiving this email because you are a subscriber to Charles Hugh Smith / Of Two Minds.
Stacker News
Is the World Becoming Uninsurable? \ stacker news
I ask the question, "is the world becoming uninsurable?" not as an expert on the insurance industry but as a homeowner who can no longer obtain hur...
Earthstar - A database for private, distributed, offline-first applications
 Earthstar is a specification and JavaScript library for building connected applications owned and run by their users.
Works offline.Store music, photos, video.Actually delete stuff.Temporary documents.Live syncing.Use one or many identities.Sneakernets.Always self-hosted.Servers optional.No blockchain.No tokens.Free forever, in every sense.
Verification with ed25519.Works in the browser.Grant read-only access.Efficient sync.Streaming sync.One identity across many devices.Multiwriter.Storage drivers.Document write permissions.Deno.Node.
originally posted at
Earthstar is a specification and JavaScript library for building connected applications owned and run by their users.
Works offline.Store music, photos, video.Actually delete stuff.Temporary documents.Live syncing.Use one or many identities.Sneakernets.Always self-hosted.Servers optional.No blockchain.No tokens.Free forever, in every sense.
Verification with ed25519.Works in the browser.Grant read-only access.Efficient sync.Streaming sync.One identity across many devices.Multiwriter.Storage drivers.Document write permissions.Deno.Node.

originally posted at 

Earthstar
Storage for private, distributed, offline-first applications. Earthstar is a specification and JavaScript library for building connected applicatio...
Stacker News
Earthstar - A database for private, distributed, offline-first applications \ stacker news
Earthstar is a specification and JavaScript library for building connected applications owned and run by their users. Works offline. Store music, p...
News Minimalist — All news ranked by significance
https://www.newsminimalist.com/
News Minimalist is the only news aggregator that ranks news by significance.
originally posted at 
Stacker News
News Minimalist — All news ranked by significance \ stacker news
News Minimalist is the only news aggregator that ranks news by significance. [1 comment]
I tried moving my Google calendar to Proton (and failed)
 Basically, the title.
I've been building up the courage to transition since I started de-googling my digital life about three years ago. At first, there was the browser. It was the easiest — Firefox instead of Chrome, obviously. Then there was mail. I learned about SimpleLogin and started using them by routing all my aliases to a single Proton email address. This was long before their partnership with SimpleLogin. Next, I moved the drive and the documents stored in it. Lastly, there was the calendar.
**Why de-googling**
Everything about my life had been hosted within the Google's ecosystem. Personal documents, bank statements, you name it. But Google’s privacy practices have been increasingly concerning, if not alarming. I got tired of them using and selling my data for advertising — my browsing behavior, purchasing habits, and my email conversations. Google was, and unfortunately still is, everywhere. It is on my phone, in my bedroom, and in my friends' houses. The company's main business model is advertising, and so their revenue streams speak for themselves.
originally posted at
Basically, the title.
I've been building up the courage to transition since I started de-googling my digital life about three years ago. At first, there was the browser. It was the easiest — Firefox instead of Chrome, obviously. Then there was mail. I learned about SimpleLogin and started using them by routing all my aliases to a single Proton email address. This was long before their partnership with SimpleLogin. Next, I moved the drive and the documents stored in it. Lastly, there was the calendar.
**Why de-googling**
Everything about my life had been hosted within the Google's ecosystem. Personal documents, bank statements, you name it. But Google’s privacy practices have been increasingly concerning, if not alarming. I got tired of them using and selling my data for advertising — my browsing behavior, purchasing habits, and my email conversations. Google was, and unfortunately still is, everywhere. It is on my phone, in my bedroom, and in my friends' houses. The company's main business model is advertising, and so their revenue streams speak for themselves.
originally posted at 

shilin typing...
i tried moving my google calendar to proton (and failed)
Ever tried moving your Google Calendar to Proton? I did—and failed spectacularly. From de-googling my life to battling sync issues, here’s the ...
Stacker News
I tried moving my Google calendar to Proton (and failed) \ stacker news
Basically, the title. I've been building up the courage to transition since I started de-googling my digital life about three years ago. At first, ...
Linux arm64 hosted runners now available for free in public repositories
 Now in public preview, Linux arm64 hosted runners are available for free in public repositories. Following the release of arm64 larger hosted runners in June, this offering now extends to the open source-community. Powered by the Cobalt 100-based processors, these 4 vCPU runners can deliver up to a 40% performance boost compared to Microsoft Azure’s previous generation of Arm-based VMs, providing a power-efficient compute layer for your workloads. Arm-native developers can now build, test and deploy entirely within the arm64 architecture without the need for virtualization on your Actions runs.
originally posted at
Now in public preview, Linux arm64 hosted runners are available for free in public repositories. Following the release of arm64 larger hosted runners in June, this offering now extends to the open source-community. Powered by the Cobalt 100-based processors, these 4 vCPU runners can deliver up to a 40% performance boost compared to Microsoft Azure’s previous generation of Arm-based VMs, providing a power-efficient compute layer for your workloads. Arm-native developers can now build, test and deploy entirely within the arm64 architecture without the need for virtualization on your Actions runs.
originally posted at 

The GitHub Blog
Linux arm64 hosted runners now available for free in public repositories (Public Preview) - GitHub Changelog
Now in public preview, Linux arm64 hosted runners are available for free in public repositories. Following the release of arm64 larger hosted runne...
Stacker News
Linux arm64 hosted runners now available for free in public repositories \ stacker news
Now in public preview, Linux arm64 hosted runners are available for free in public repositories. Following the release of arm64 larger hosted runne...
SimpleX network: large groups and privacy-preserving content moderation
 Many people believe that it is impossible to moderate and prevent abuse in end-to-end encrypted conversations. This belief is incorrect — there is a way to prevent abuse and distribution of illegal content without any compromises to users' privacy and security of end-to-end encryption.
Anti-privacy lobbyists use this incorrect belief to advocate for scanning of private communications, which not only would fail to prevent abuse, but would make it worse — because our private data will become available to criminals.
So it's very important to understand how privacy preserving content moderation works, and educate the politicians who you voted for, and who is currently in the office, that we do not need to compromise privacy and security in any way to substantially reduce online crime and abuse.

originally posted at
Many people believe that it is impossible to moderate and prevent abuse in end-to-end encrypted conversations. This belief is incorrect — there is a way to prevent abuse and distribution of illegal content without any compromises to users' privacy and security of end-to-end encryption.
Anti-privacy lobbyists use this incorrect belief to advocate for scanning of private communications, which not only would fail to prevent abuse, but would make it worse — because our private data will become available to criminals.
So it's very important to understand how privacy preserving content moderation works, and educate the politicians who you voted for, and who is currently in the office, that we do not need to compromise privacy and security in any way to substantially reduce online crime and abuse.

originally posted at 

SimpleX network: large groups and privacy-preserving content moderation
Stacker News
SimpleX network: large groups and privacy-preserving content moderation \ stacker news
Many people believe that it is impossible to moderate and prevent abuse in end-to-end encrypted conversations. This belief is incorrect — there i...
How to set up BOLT12 Lightning payouts for OCEAN with Coinos
 First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9).
Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages.
originally posted at
First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9).
Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages.

originally posted at 

Primal
Live Free
Stacker News
How to set up BOLT12 Lightning payouts for OCEAN with Coinos \ stacker news
First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants t...
US Will Ban Cancer-Linked Red Dye No. 3 in Cereal And Other Foods
 US health officials banned the artificial food coloring Red No. 3, which has been linked to cancer and is currently in scores of products from candy to cold medicine.
The dye will no longer be allowed in US food starting Jan. 15, 2027, according to a Food and Drug Administration document posted online. Drugmakers who use the artificial coloring will have until Jan. 18, 2028 to reformulate their products, the agency said.
originally posted at
US health officials banned the artificial food coloring Red No. 3, which has been linked to cancer and is currently in scores of products from candy to cold medicine.
The dye will no longer be allowed in US food starting Jan. 15, 2027, according to a Food and Drug Administration document posted online. Drugmakers who use the artificial coloring will have until Jan. 18, 2028 to reformulate their products, the agency said.
originally posted at 

Bloomberg.com
US Will Ban Cancer-Linked Red Dye No. 3 in Cereal And Other Foods
US health officials banned the artificial food coloring Red No. 3, which has been linked to cancer and is currently in scores of products from cand...
Stacker News
US Will Ban Cancer-Linked Red Dye No. 3 in Cereal And Other Foods \ stacker news
US health officials banned the artificial food coloring Red No. 3, which has been linked to cancer and is currently in scores of products from cand...