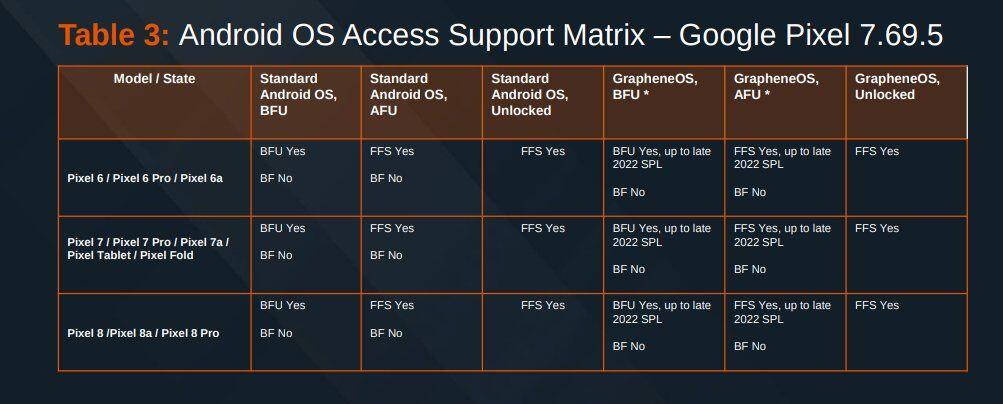
#GrapheneOS version 2025070900 released.
- Settings: extend standard fingerprint enrollment stages with proper support for devices with power button fingerprint scanners (Pixel Fold, Pixel Tablet) which is not present in AOSP (Pixel Fold was still usable, but it had become incredibly hard to successfully register new fingerprints on the Pixel Tablet)
- improve warning for 32-bit-only apps by explaining why the warning is shown, how to resolve it for apps that are still developed and that we plan to phase out support for it on 5th/6th generation Pixels where it's still available
- show warning for 32-bit-only apps on each launch instead of only once
- kernel (Pixel 7, Pixel 7 Pro, Pixel 7a, Pixel Tablet, Pixel Fold, Pixel 8, Pixel 8 Pro, Pixel 8a): disable 32-bit ABI support to substantially decrease kernel size and attack surface and raise mmap_min_addr to the standard 65536 for 64-bit-only ARM
- kernel (5.15): update to latest GKI LTS branch revision including update to 5.15.158
- adevtool: update file removal for 8th gen Pixels to skip Family Space related files
- GmsCompatConfig: update to version 122
- Vanadium: update to version 126.0.6478.122.3


![final [GrapheneOS] 📱👁️🗨️'s avatar](https://image.nostr.build/d837117ca56e292d9f16143a673f47fdb0c3f7273573a2394b1892b3c8c8a688.jpg)