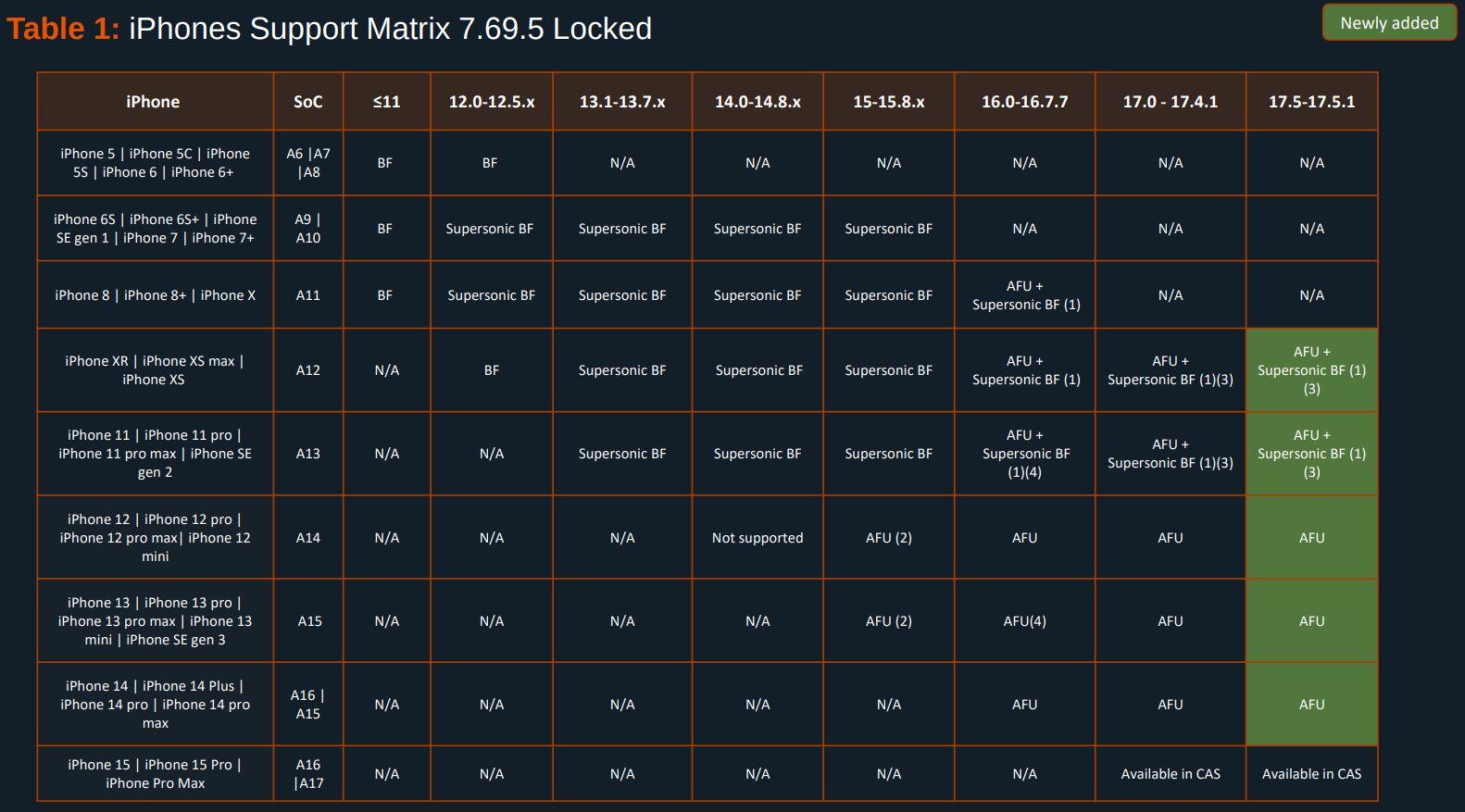
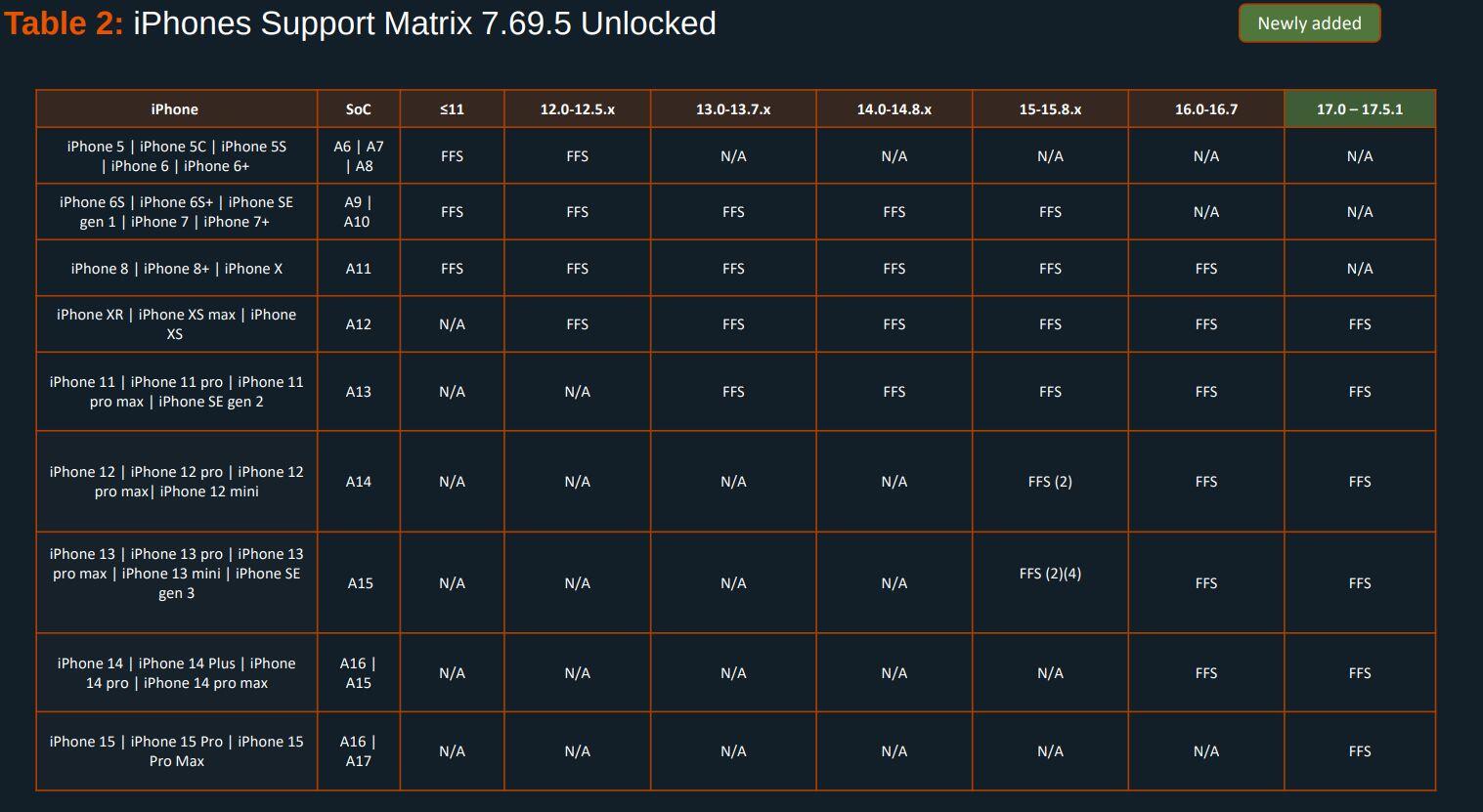
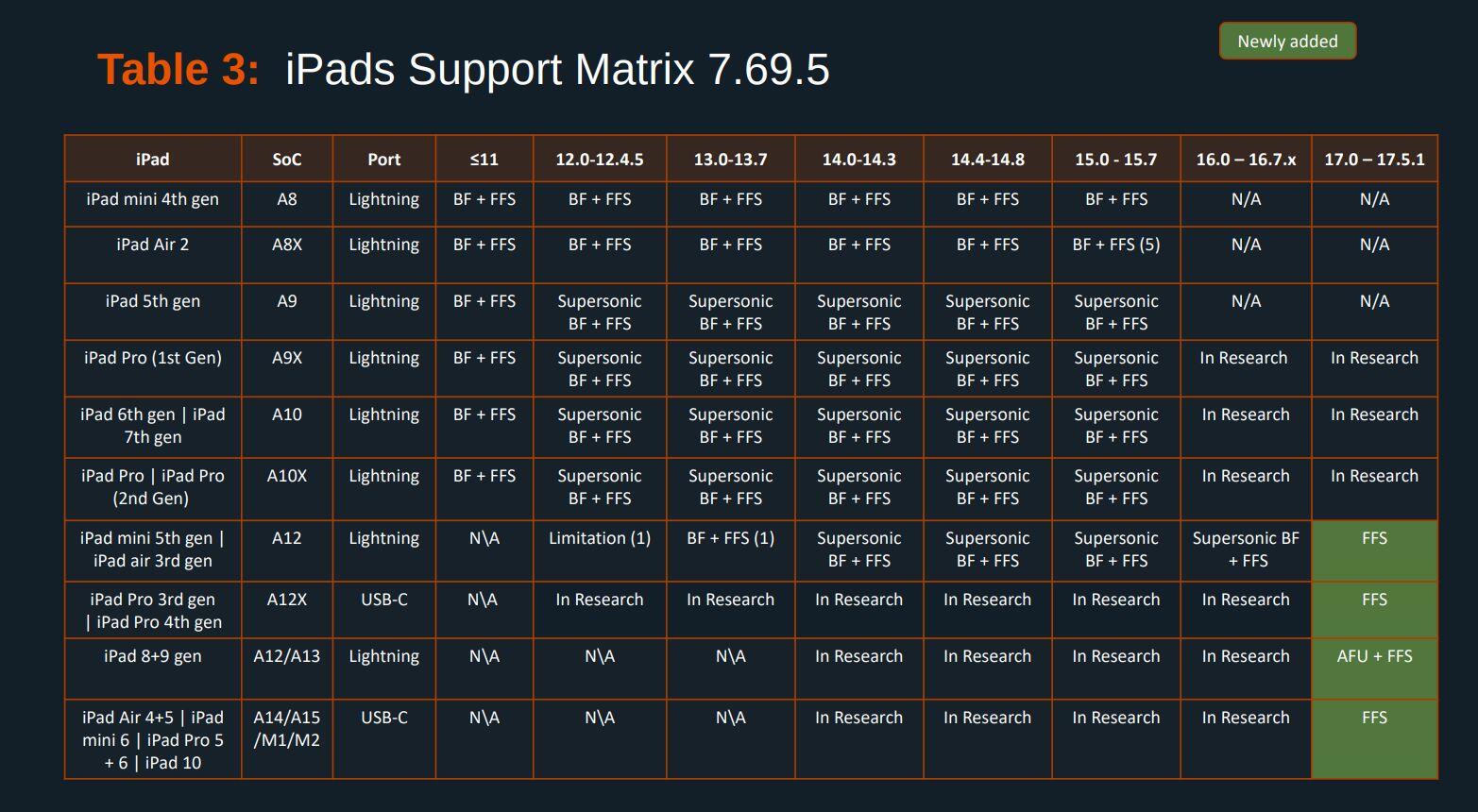
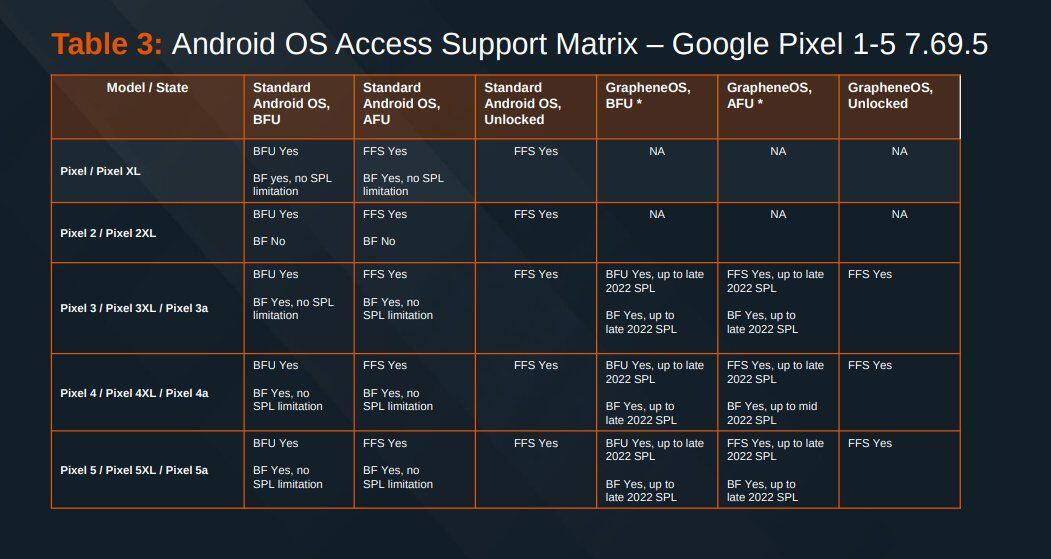
Unplugged have doubled down on false claims about GrapheneOS security, pretending people cannot buy devices with GrapheneOS installed and pretending it's hard to install along with promoting their blatantly insecure products with false marketing.

X (formerly Twitter)
The Andres Segovia (@_AndresSegovia) on X
Long before Unplugged delivered their first phone, they were under scrutiny because of it's founders. And while people can hear from co-founder Eri...
We have an existing thread going through many of their false claims and debunking them:

X (formerly Twitter)
GrapheneOS (@GrapheneOS) on X
Unplugged are a recent entry in the crowded space of selling insecure hardware with significantly worse privacy and security than an iPhone as high...
We also responded to their lies about GrapheneOS directly. They've read our posts and have chosen to continue peddling the same misinformation about GrapheneOS.
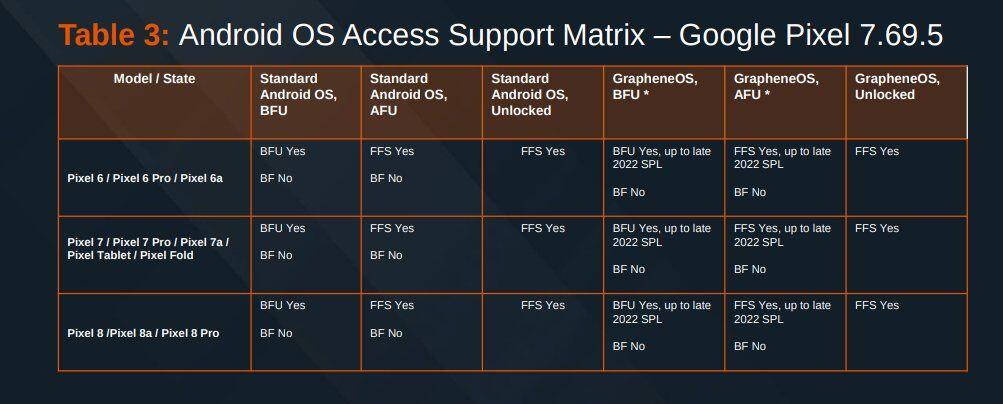
They keep pushing the false claim that Pixels supporting using another OS makes them less secure. The reality is that it's properly implemented in a secure way without adding any significant attack surface. The bottom of the barrel MediaTek Unplugged devices have awful security.
They still haven't ported to the initial release of Android 14 with Android 15 right around the corner. This means they're missing at least around a year of Moderate severity privacy/security patches and huge privacy/security improvements from the past year of Android releases.
Unplugged is using an SoC from MediaTek, a company known to have poor security practices, which fares poorly against real attackers and which has a history of repeatedly shipping actual backdoors. They're trying to portray that as more trustworthy and more secure hardware. Nope.
Unplugged was founded by Erik Prince, noted war criminal and illegal arms dealer. They make a point in talking about the involvement of their employees in enabling these kinds of operations:

X (formerly Twitter)
GrapheneOS (@GrapheneOS) on X
Here's an example of a "counterterrorism operation" by a U.S.-allied Western government targeting political opponents with NSO exploits:
https://t...
That doesn't imply competence, but explains the lack of ethics.
They're trying to present themselves as if they were leaders in the field and switched sides, but they never were and simply want money.
Unplugged is an affinity scam in the same vein as the Freedom Phone. Unplugged has built their product out of open source projects, but without complying with the licenses from projects like DivestOS and while trying to harm open source. Claiming to be in the process of replacing some of the code they were caught stealing doesn't change much...
![final [GrapheneOS] 📱👁️🗨️'s avatar](https://image.nostr.build/d837117ca56e292d9f16143a673f47fdb0c3f7273573a2394b1892b3c8c8a688.jpg)