I recommended you a few times in the past not to overhype the privacy state of Lightning. I suggest you align your documentation with this: 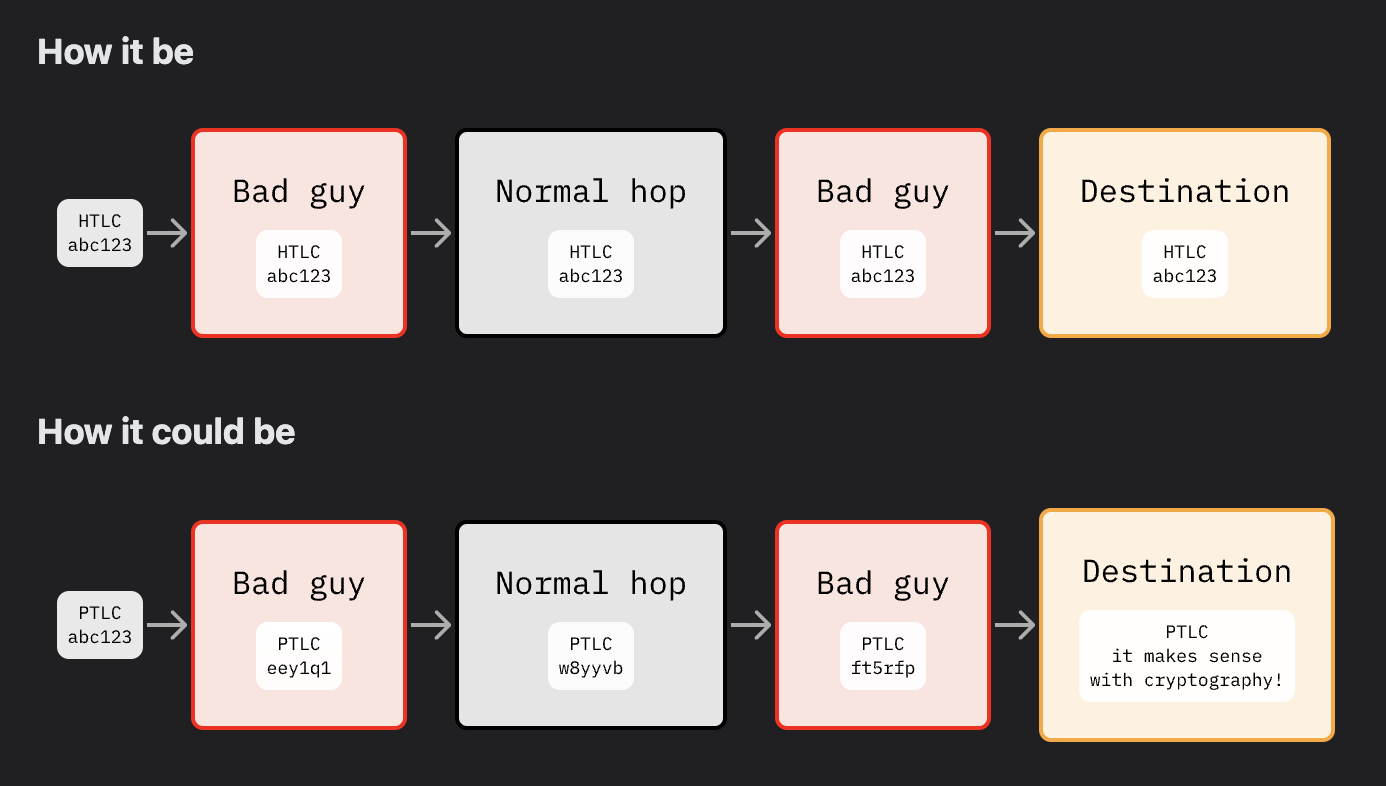

Lightning Privacy Research
Lightning Privacy Introduction | Lightning Privacy Research
An introduction to Lightning privacy

