Certificate and Public Key Pinning
 A nation state with control over a Certificate Authority could create SSL certs for any domain and easily perform a MITM. That's the risk.
First idea that comes to mind to mitigate it, would be to at least pin domains to CAs so that a random CA controlled by a nation state can't issue a new certificate for any domain without going unnoticed.
This might be overkill and apparently is not a good idea:
- PKI has significantly improved - browser vendors (Google, Mozilla, Apple, Microsoft) now strictly control CA trust stores and remove non-compliant CAs
- Certificate Transparency - all certificates must be publicly logged, making rogue certificates detectable
- CAA records - DNS records that specify which CAs can issue certificates for a domain
- Pinning creates major operational risks - misconfigured pins can cause complete outages that are difficult to recover from
But just out of curiosity, I'm trying a Firefox add-on that notifies you every time something changes in the certificate of a website that you had already visited. It can be configured to only notify you on a change of the issuer. So if a website goes from Let's Encrypt CA to CCP CA, you should worry xD
Here's the extension:
A nation state with control over a Certificate Authority could create SSL certs for any domain and easily perform a MITM. That's the risk.
First idea that comes to mind to mitigate it, would be to at least pin domains to CAs so that a random CA controlled by a nation state can't issue a new certificate for any domain without going unnoticed.
This might be overkill and apparently is not a good idea:
- PKI has significantly improved - browser vendors (Google, Mozilla, Apple, Microsoft) now strictly control CA trust stores and remove non-compliant CAs
- Certificate Transparency - all certificates must be publicly logged, making rogue certificates detectable
- CAA records - DNS records that specify which CAs can issue certificates for a domain
- Pinning creates major operational risks - misconfigured pins can cause complete outages that are difficult to recover from
But just out of curiosity, I'm trying a Firefox add-on that notifies you every time something changes in the certificate of a website that you had already visited. It can be configured to only notify you on a change of the issuer. So if a website goes from Let's Encrypt CA to CCP CA, you should worry xD
Here's the extension:  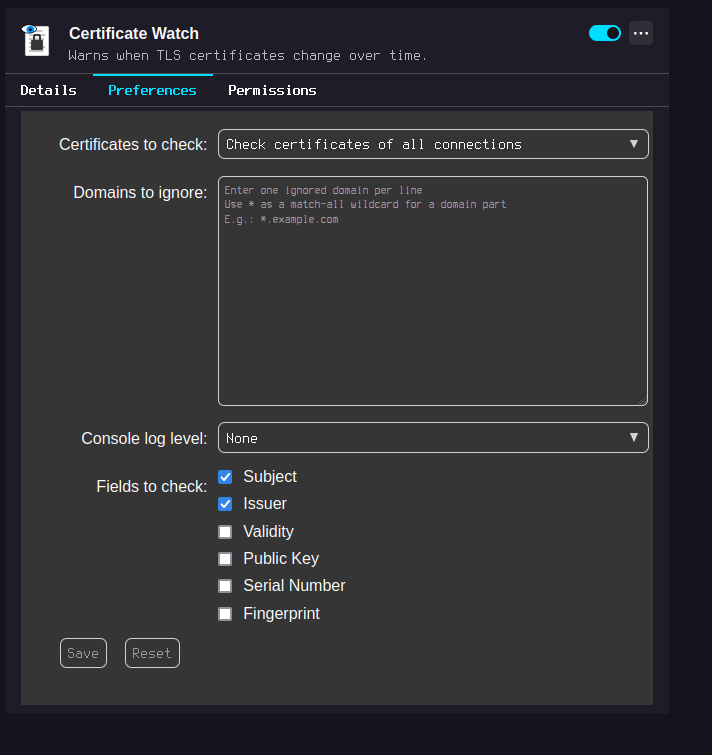


Certificate and Public Key Pinning | OWASP Foundation
Certificate and Public Key Pinning on the main website for The OWASP Foundation. OWASP is a nonprofit foundation that works to improve the security...
GitHub
GitHub - PilzAdam/CertificateWatch: A Firefox add-on that warns about changing certificates
A Firefox add-on that warns about changing certificates - PilzAdam/CertificateWatch
Stacker News
Certificate and Public Key Pinning \ stacker news ~tech
A nation state with control over a Certificate Authority could create SSL certs for any domain and easily perform a MITM. That's the risk. First id...
