About the recent #BTC Crash:
What was the cause? Rumors..
Before discussing the current market situation, I would like to share with you the most probable reason for what happened on Friday (without conspiracy theories).
The Binance exchange allowed the use of USDe (the ENA stablecoin), wBETH (wrapped ether), and BNSOL as collateral for margin positions.
But there was a problem with the exchange. The exchange's system valued these 3 assets based on the price in its own order book, rather than relying on external sources. This means that if someone inside the exchange dumps a critical volume of these assets, their price would instantly drop. The exchange's internal system would automatically consider the collateral assets depreciated and start liquidating clients' positions.
The exchange knew about this problem and announced on October 6th that it would switch from its own order book to oracles (a service that takes price data for an asset from all sources and provides an average value - giving an objective price and not accounting for manipulations on individual exchanges). However, the new system was only scheduled to start working on October 14th (8 days remained until the vulnerability was closed).
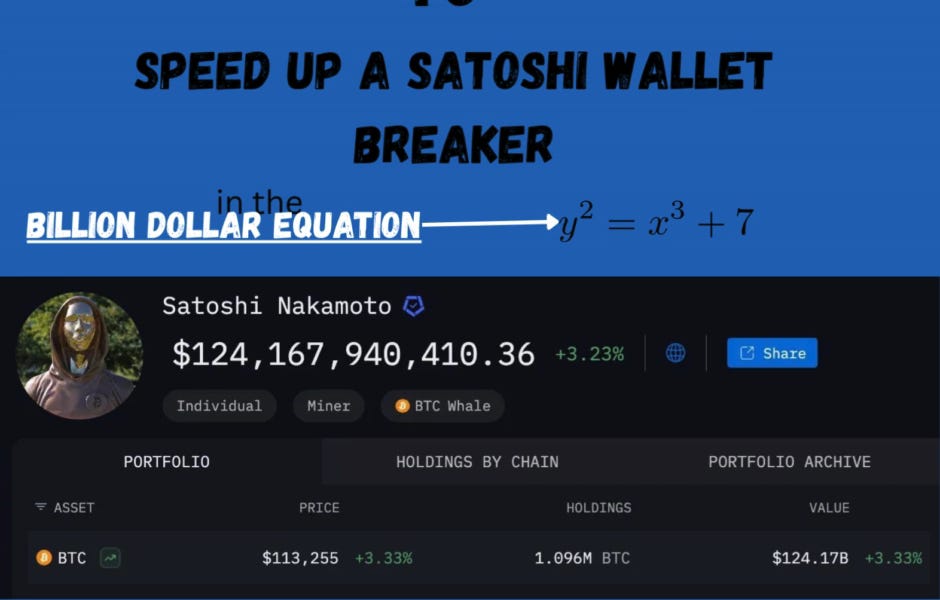
On October 10th, a large whale, who owns coins from the Satoshi Nakamoto era of Bitcoin (since 2011) and had been actively moving them to Ethereum in recent months, opened a SHORT position of over $1,000,000,000 on BTC and ETH on the HyperLiquid exchange (most likely a close insider).
Just a few minutes before Trump began making aggressive statements about China and announcing new tariffs...
At that moment, someone intentionally dumped ~80M USDe on Binance (the price inside the exchange dropped from $1 to $0.65 - while it remained stable everywhere else). If oracles had been working, everything would have been fine. But the exchange's system, relying on the quote in its order book, decided that the "collateral" had depreciated and began liquidations of around ~$800M - $1B (including market maker positions).
Against the backdrop of Trump's statements, the crowd was in a state of panic and started closing their long positions / getting liquidated (selling), opening short positions (selling), dumping spot on emotions (selling). The algorithms of the largest exchanges/managers are oriented towards Binance (the largest and most liquid exchange) and automatically started selling/hedging/reducing liquidity to avoid losses.
And instantly, the $80M USDe dump in the order book, combined with the panic from the news, triggered an unprecedented cascade of liquidations of ~$19B according to public data, and more than $80B (according to rumors).
Outcomes:
1. The short positions of the insider whale from the Satoshi Nakamoto era made a profit of $192M in a matter of minutes (and he has been converting his bitcoins to ether all year - he believes in the growth prospects of the alt market).
2. The market was completely cleared of leverage, loans (favorable). The capital of overconfident retail investors moved into the hands of insiders.
3. Binance has already stated that the technical problems were on their end and they are fixing the situation (switching to oracles), which means it is very likely that something similar will not happen again (now everyone will be afraid of a repeat). And technology like ChainLink is necessary for the stable functioning of exchanges in the future.
The situation is terrible, insidious, but the market is also high-risk. Most likely, this is a one-time, systemic problem and will be fixed soon. The manipulation was "covered" by the news of Trump's speech. CZ is silent (although he usually urges to buy the dip and not panic), this is unsettling. From the beginning of the week, we will get more accurate data on what happened, the guilty parties, the consequences for them, and the victims (it might be volatile).

🔄 REPOSTING FROM REDDIT
🚨 Post:
Why centralised KYC exchanges allow ZEC. Clarification on the current state of ZEC Trusted Setup in their production blockchain.
I have conducted a small research with DeepSeek and real persons from r/zec involved, and the conclusion is the following:
Indeed, ZEC production blockchain has been upgraded to the Halo2 cryptographic system that allows to gradually eliminate and fade out the dependence on the well known and pain famous Trusted Setup ceremony by systematic updates of the Universal Reference String (URS). Halo2 does theoretically allow any blockchain participant to update the URS by some procedure.
But DE FACTO, the URS string generated in the Trusted Setup ceremony stays UNMODIFIED on the current production blockchain of ZEC.
This fact signifies if just one of the ceremony participants has not wiped out his key, all the ZEC hidden transactions on the production blockchain still can be traced out.
Furthermore, in ZEC network, no production blockchain participant can easily update the URS because it does require the whole ZEC network protocol upgrade used in the production blockchain.
The decision on protocol upgrade can be made only by ZEC core developers in their Electric Coin Company (ECC). It is like a hard fork, thus, extremely epic operation, that involves into cooperation all the blockchain participants.
So, if just one key from Trusted Setup has not been wiped out, all the hidden transactions on the ZEC production blockchain can be traced by 3rd party, namely FBI and other 3-letters agencies belong to government authorities.
That’s why ZEC can be easily listed on virtually all KYC centralised exchanges: a dedicated group of people can trace all the hidden transactions because there exists a key that has not been properly wiped out.
Note, at the methodological point of view, we have no duty to prove there exists a key that has not been wiped out, it is SUFFICIENT we can’t prove it HAS BEEN wiped out.
So, being growing in listings on KYC centralised exchanges, the ZEC price is skyrocketing, what we do exactly observe.
🚨 OP comments:
1. Pegasus malware backed by government, etc etc.
2. If the toxic waste for the production URS exists and is known to an adversary, then the privacy and integrity of the current ZCash production blockchain's Orchard pool are broken:
All the today-made hidden transactions can be gradually traced out.
ZEC coins can be created from thin air and spent out.
That’s exactly why Halo2 was introduced at all: it allows a gradual RECOVERY from the compromised state to the secure state by updating URS value in the new Trusted Setup from URS1 (proven compromised) to URS2 (considered as honest).
In a nutshell: if ZEC core devs do share URS1 , URS2, etc with FBI, the total project is a fully devastating SCAM. Halo2 can’t save us in this situation.
Unlike in Monero only open source code matters. Monero core devs CAN NOT share something with FBI to explore our transactions!
Now you see how devastating is the world: ZEC is skyrocketing and Nobody cares IT IS NOT a privacy coin at all.
Because, I repeat, at methodological point of view we have no duty to prove that URS value is not compromised.
It is SUFFICIENT we can’t prove it IS NOT compromised (by FBI, etc).
ZEC is a fatal and fundamental philosophical SCAM because we always MUST TRUST in ZEC network.
Actually, ZEC is an ideal model for traditional KYC financial institutions where a dedicated group of people MUST know all your transaction history.
That’s precisely why they meet KYC so easily, appearing on most centralised exchanges and their price is skyrocketing like Bitcoin price.
But, while Bitcoin does declare it is NOT private , it is NOT a scam.
But ZEC declares it is Private but actually it is NOT, so they simply directly, pedantically lie. So they are SCAM by definition.
https://www.reddit.com/r/Monero/comments/1o453e3/why_centralised_kyc_exchanges_allow_zec/

All drugs containing acetaminophen:
OTC
1. Tylenol: The most well-known brand for acetaminophen.
2. Excedrin: Often used for headaches, it combines acetaminophen with aspirin and caffeine.
3. NyQuil: A cold and flu medication that includes acetaminophen for pain relief.
4. DayQuil: Similar to NyQuil but formulated for daytime use.
5. Advil Dual Action: Combines ibuprofen and acetaminophen for enhanced pain relief.
6. Alka-Seltzer Plus: Some formulations include acetaminophen for cold and flu relief.
7. Midol: Often used for menstrual pain, some versions contain acetaminophen.
8. Aspirin-Free Excedrin: Contains acetaminophen, caffeine, and other ingredients for headache relief.
9. Bayer Back & Body: Combines acetaminophen with aspirin for back pain relief.
10. Aleve-D: Some formulations may include acetaminophen for added pain relief.
11. Tylenol Extra Strength: A higher dose formulation of acetaminophen for more severe pain.
12. Advil PM: Some formulations may include acetaminophen along with diphenhydramine.
Cold and Allergy Medications
1. Zyrtec-D: Some formulations may include acetaminophen for allergy relief.
2. Sudafed PE: Certain combinations may contain acetaminophen for cold symptoms.
3. Robitussin Cough + Chest Congestion DM: Some versions include acetaminophen for pain relief.
4. Vicks DayQuil: A daytime cold and flu relief option that contains acetaminophen.
5. Benadryl Allergy Plus Congestion: Certain formulations may contain acetaminophen for added relief.
6. Claritin-D: Some versions may include acetaminophen for allergy relief.
RX
1. Percocet: A combination of oxycodone and acetaminophen used for pain relief.
2. Tylenol with Codeine: Combines acetaminophen with codeine for more severe pain.
3. Fioricet: Contains acetaminophen, butalbital, and caffeine, often prescribed for migraines.
4. Vicodin: A combination of hydrocodone and acetaminophen, used for moderate to severe pain.
5. Lortab: Another combination of hydrocodone and acetaminophen.
6. Norco: Similar to Vicodin, it combines hydrocodone with acetaminophen.
7. Roxicet: A combination of oxycodone and acetaminophen, used for pain management.
8. Cocet: Combines acetaminophen with oxycodone for pain relief.
9. Fentanyl Combination Products: Some formulations may combine fentanyl with acetaminophen for pain management.
10. Lorcet: A combination of hydrocodone and acetaminophen.
11. Percodan: Combines oxycodone with acetaminophen for pain management.
12. Tylenol with Tramadol: A combination of acetaminophen and tramadol for moderate to severe pain.
Combination Products
1. Cold and Flu Formulations: Many products for cold and flu symptoms contain acetaminophen, such as Theraflu and Robitussin.
2. Pain Relievers: Some multi-symptom pain relievers may include acetaminophen along with other active ingredients.
3. Robitussin Multi-Symptom: Contains acetaminophen along with other ingredients for cough and cold relief.
4. Theraflu: Various formulations include acetaminophen for symptom relief.
5. Excedrin Tension Headache: Specifically formulated for tension headaches, containing acetaminophen.
6. Mucinex: Some formulations include acetaminophen for cold and flu symptom relief.
7. Coricidin HBP: Certain versions contain acetaminophen for cold symptoms, designed for those with high blood pressure.
8. Sominex: Some formulations may include acetaminophen for sleep aid with pain relief.
Pediatric
1. Children's Tylenol: Liquid formulations specifically designed for children.
2. Infants' Tylenol: Liquid acetaminophen specifically designed for infants.
3. Children's Motrin: Some formulations may include acetaminophen alongside ibuprofen.
4. Children's Advil: Some formulations may include acetaminophen alongside ibuprofen.
5. Pediatric Fever Reducers: Various brands offer liquid acetaminophen specifically for children.

How to Track the People Tracking YOU
Discover “Chasing Your Tail,” an open-source surveillance detection tool you can build with a Raspberry Pi. In this exclusive Black Hat interview, creator Matt explains how it tracks Wi-Fi, Bluetooth, and even tire sensors to spot if you’re being followed, then flips the script to map where your followers spend time. Learn the origins of this tool, from avoiding surprise visits to protecting informants and aiding search & rescue. We cover the tech stack (Kismet, Python, GPS integration), real-world success stories, and how you can set it up yourself for under $100. Perfect for security pros, privacy
advocates, and tech enthusiasts.
Chasing Your Tail (CYT)

GitHub
GitHub - ArgeliusLabs/Chasing-Your-Tail-NG: MUCH Improved version of the Python Chasing Your Tail Tool to help you determine if you're being followed
MUCH Improved version of the Python Chasing Your Tail Tool to help you determine if you're being followed - ArgeliusLabs/Chasing-Your-Tail-NG
A comprehensive WiFi probe request analyzer that monitors and tracks wireless devices by analyzing their probe requests. The system integrates with Kismet for packet capture and WiGLE API for SSID geolocation analysis, featuring advanced surveillance detection capabilities.
Features:
Real-time Wi-Fi monitoring with Kismet integration
Advanced surveillance detection with persistence scoring
Automatic GPS integration - extracts coordinates from Bluetooth GPS via Kismet
GPS correlation and location clustering (100m threshold)
Spectacular KML visualization for Google Earth with professional styling and interactive content
Multi-format reporting - Markdown, HTML (with pandoc), and KML outputs
Time-window tracking (5, 10, 15, 20 minute windows)
WiGLE API integration for SSID geolocation
Multi-location tracking algorithms for detecting following behavior
Enhanced GUI interface with surveillance analysis button
Organized file structure with dedicated output directories
Comprehensive logging and analysis tools
Requirements:
Python 3.6+
Kismet wireless packet capture
Wi-Fi adapter supporting monitor mode
Linux-based system
WiGLE API key (optional)

🧫 PARASITE CLEANSE PROTOCOL (30–90 Days)
A full-body strategy to eliminate parasites, break biofilms, support detox pathways, and heal the gut for long-term health. You will find a simplified version of this protocol in the comments. There is also a heavy metal detox guide on this page which is recommended to do first.
✅ Step 1: PREP PHASE (7–10 Days)
🎯 Goal: Prepare your body by opening detox and drainage pathways — like the liver, lymphatic system, and bowels.
Why it matters: If you jump straight into killing parasites, your body may struggle to eliminate the toxins they release. This leads to "die-off" symptoms (see below).
*Think of this like unclogging a sink before pouring anything else down the drain.
🔓 Open Detox Pathways:
- Castor Oil Packs (3–4x/week)
Apply a warm castor oil-soaked cloth over your liver (upper right abdomen).
Cover with plastic wrap and a heating pad for 30–60 minutes.
This gently stimulates liver drainage, bile flow, and lymph movement.
Great for constipation and hormonal balance, too.
- Magnesium Citrate or Oxy-Magnesium (like Oxy-Powder)
Helps you poop daily — non-negotiable during detox.
If you’re constipated, waste and toxins get reabsorbed.
Start low (200–300 mg) and increase to achieve 1–2 daily bowel movements.
- Liver-Supportive Herbs
Milk Thistle: Regenerates liver cells.
Dandelion Root: Stimulates bile flow.
Burdock: Gentle blood cleanser.
You can also use a liver detox tincture (like Gaia Liver Cleanse or Herb Pharm Liver).
- Lymphatic Movement
Dry brushing: Use a soft brush on dry skin before showering — always brush toward the heart.
Rebounding: Jumping on a mini trampoline moves lymph.
Infrared sauna or red light therapy: Help sweat out toxins and boost circulation.
💧 Daily Add-ons:
- Apple Cider Vinegar (1–2 tsp in warm water before meals)
Stimulates stomach acid and digestive enzymes.
Aids in breaking down food and creating a hostile environment for parasites.
- Herbal teas (1–2 cups/day):
Dandelion root: Liver detox
Nettle: Nourishing + mineralizing
Lemon-ginger: Gut soothing and cleansing
- Water: 2–3 liters/day of clean, filtered water
Add electrolytes or trace minerals to support cellular detox.
⚔️ Step 2: ACTIVE PARASITE CLEANSE (30–60 Days)
🎯 Goal: Kill parasites, break down their protective biofilms, flush out eggs, and mop up released toxins.
⚠️ Warning: Don’t start killing before Step 1! You must prepare the body or risk overwhelming detox reactions.
🧪 Choose 2–4 Core Anti-Parasitics
Rotate them every 2–3 weeks to prevent adaptation. Many parasites develop resistance when exposed to the same herb for too long.
🌿 Common anti-parasitics:
- Mimosa Pudica Seed
A sticky, fibrous seed that grabs parasites and biofilms in your intestines like a sponge.
Take 2 capsules on an empty stomach in the morning.
Expect to see stringy, rope-like material in your stool (often biofilms + worms).
- Black Walnut Hull
Powerful against adult parasites, fungi, and bacteria.
Use tincture or capsule.
- Wormwood (Artemisia)
Excellent for roundworms and threadworms.
Often used in combination formulas (e.g., with black walnut and clove).
- Clove
Kills parasite eggs — crucial so the life cycle doesn’t restart.
Use daily during cleanse.
- Neem
Multipurpose: antifungal, anti-worm, antibacterial.
- Berberine, Olive Leaf, or Oregano Oil
Target bacterial imbalances, yeast, and parasites.
Berberine also supports gut repair and blood sugar regulation.
- Diatomaceous Earth (Food Grade Only!)
Fine silica powder that physically shreds parasites in the gut.
Take 1 tsp in water on an empty stomach.
Avoid inhaling powder — use caution.
🔓 Biofilm Disruptors
Parasites hide in protective “slime layers” (biofilms) in the gut and organs. Break these open to expose them.
- NAC (N-Acetylcysteine): 600–1200 mg/day
Powerful antioxidant + biofilm disruptor.
Supports liver by increasing glutathione.
- Enzymes
Use proteolytic enzyme blends that digest proteins:
InterFase Plus, Biofilm Defense, SerraFlora, Lumbrokinase
Best taken away from food, 1–2x/day
- Optional: EDTA
Chelator that pulls metals (often embedded in biofilms).
Advanced; best with practitioner guidance.
🧲 Don’t Skip the BINDERS
When parasites die, they release ammonia, mold, heavy metals, and endotoxins. Binders catch them so your body can safely eliminate them through stool.
Activated Charcoal, Bentonite Clay, or Chlorella
Take 1–2x daily, away from food/supplements/meds by at least 1–2 hours.
Charcoal = general toxin binder
Clay = binds positively charged toxins
Chlorella = heavy metals + mold
Gentler options: Pectin, fulvic/humic acids, ZeoBind (zeolite)
🧬 Step 3: GUT REPAIR & IMMUNE REBALANCE (30+ Days)
🎯 Goal: Once the parasites are gone, rebuild your gut lining and microbiome. Otherwise, new ones can take hold again.
🛠 Heal the Gut Lining:
- L-Glutamine: 5–10g/day — strengthens intestinal walls
- Aloe Vera Juice: Soothes inflammation, supports healing
- Collagen or Bone Broth: Rich in amino acids like glycine
- Soothing Herbs:
Slippery elm, marshmallow root, DGL licorice
- Zinc carnosine, quercetin – reduce gut inflammation
🌱 Rebuild Microbiome:
- Spore-based probiotics (e.g. Just Thrive, MegaSporeBiotic)
More stable than regular probiotics; survive stomach acid.
- Saccharomyces boulardii
Probiotic yeast that helps crowd out bad bugs.
- Prebiotic fibers (start slow):
PHGG, acacia fiber, green banana flour — feed the good bugs.
🔁 CYCLIC DOSING: 4 DAYS ON / 3 DAYS OFF
Why it works: Parasites have life cycles. Pulsing disrupts those cycles and allows your organs to catch up on detox.
4 Days ON: Take your antiparasitics, enzymes, and biofilm disruptors
3 Days OFF: Take only binders and drainage support — give your system a break
Repeat for 4–6 weeks minimum (up to 90 days for chronic cases)
🌕 FULL MOON INTENSIFICATION
Why? Parasites become more active during the full moon — possibly due to lower melatonin and higher serotonin.
From 3 days before to 3 days after full moon:
- Increase antiparasitics by 25–50%
- Increase binders, water, and electrolytes
You may notice more symptoms — this is when many people pass the most.
⚠️ DIE-OFF SYMPTOMS (Herxheimer Reactions)
Common reactions as parasites and pathogens die off:
- Headaches, fatigue, joint pain
- Skin rashes, brain fog
- Nausea, mood swings, worsened old symptoms
How to reduce it:
- Drink more water + add minerals (sea salt, trace minerals)
- Take binders religiously
- Use detox tools:
Epsom salt baths (draw out toxins via skin)
Infrared sauna
Dry brushing or rebounding
Coffee enemas (for advanced users: clears bile + toxins from liver/gut)
If you feel awful, lower dosage or take a break. The goal is sustainable, steady progress — not suffering.
🧪 OPTIONAL TESTING
To confirm parasites or monitor healing:
- GI-MAP or GI Effects: Advanced stool testing
- OAT (Organic Acids Test): Shows fungal + bacterial metabolites
- Stool microscopy + PCR (Doctor’s Data, Genova)
- Blood tests:
Eosinophils or Total IgE may rise during parasitic infections
🧠 LIFESTYLE ADD-ONS
Create an inner terrain where parasites can’t thrive:
- Eliminate their food supply:
Sugar, gluten, processed carbs, seed oils, dairy
- Eat anti-parasitic foods daily:
Raw garlic, pumpkin seeds, papaya seeds, raw carrots, beets, cilantro
- Get sunlight and sleep (7–9 hours)
- Reduce chronic stress – stress suppresses immune defense
📦 RECOMMENDED CLEANSE KITS
Save time and confusion with these well-designed, practitioner kits:
CellCore Para Kit – Strong for chronic illness, mold, Lyme
Microbe Formulas Protocol – Multi-phase system with drainage + gut repair
Dr. Clark Store Cleanse – Simple and affordable
Mimosa Pudica + Para 1/2/3 – For deeper parasite and toxin cleansing