Let me know if you need a invite to try the new #proton #wallet

ᑎOᔕTᖇ
Nostr@carlostkd.ch
npub1k3dv...k7dv
If something does not go right
Go to #nostr
Delinea Local Privilege Escalation
#infosec #cybersecurity #ethicalhacking #news #privacy


Identity Crisis: The Curious Case of a Delinea Local Privilege Escalation Vulnerability
During a recent customer engagement, the CyberArk Red Team discovered and exploited an Elevation of Privilege (EoP) vulnerability (CVE-2024-39708) ...
Exploit the Prisma ORM to leak sensitive data.
#infosec #cybersecurity #ethicalhacking #news #privacy
plORMbing your Prisma ORM with Time-based Attacks - elttam
elttam is a globally recognised, independent information security company, renowned for our advanced technical security assessments.
Universal Code Execution by Chaining Messages in Browser Extensions
#infosec #cybersecurity #ethicalhacking #news #privacy
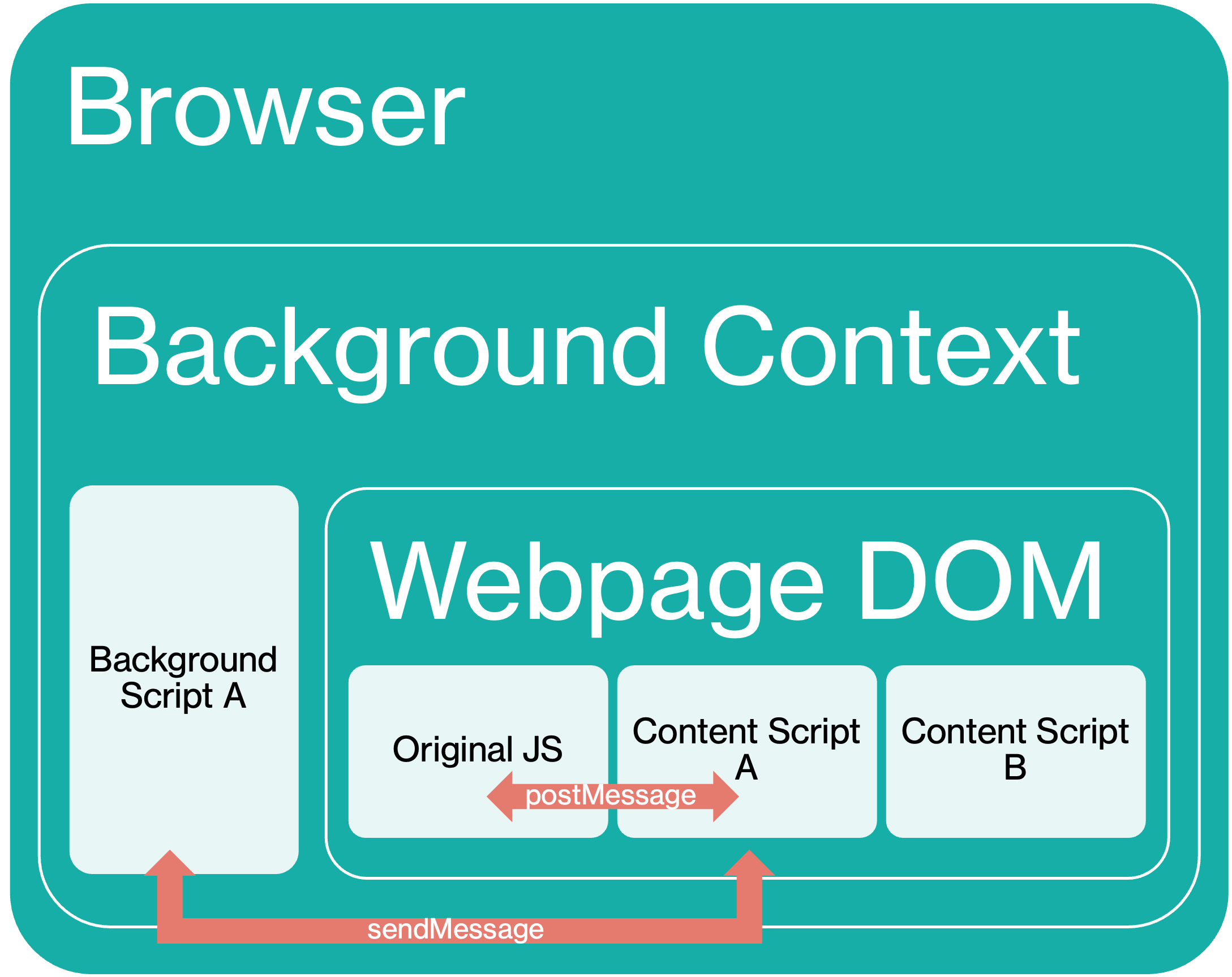

Universal Code Execution by Chaining Messages in Browser Extensions
By chaining various messaging APIs in browsers and browser extensions, I demonstrate how we can jump from web pages to “universal code execut...
No more secrets
#infosec #cybersecurity #ethicalhacking #news #privacy


Summoning Team
There are no Secrets || Exploiting Veeam CVE-2024-29855
This vulenrability is due to the fact that JWT secret used to generate authentication tokens was a hardcoded value which means an unauthenticated a...
YetiHunter
An open-source tool to detect suspicious activities in Snowflake
#infosec #cybersecurity #ethicalhacking #news #privacy


Introducing YetiHunter: An open-source tool to detect and hunt for suspicious activity in Snowflake
YetiHunter is an open source tool that combines the indicators that Snowflake, Mandiant, DataDog and Permiso have into one easy to run script to de...
Exploiting Gradio to (still) Steal Secrets from Hugging Face Spaces
#infosec #cybersecurity #ethicalhacking #news #privacy


Horizon3.ai
Exploiting File Read Vulnerabilities in Gradio to Steal Secrets from Hugging Face Spaces
Exploiting file read vulnerabilities in Gradio to steal secrets from Hugging Face Spaces.
Shut down a website by triggering WAF rule.
#infosec #cybersecurity #ethicalhacking #news #privacy #nostr
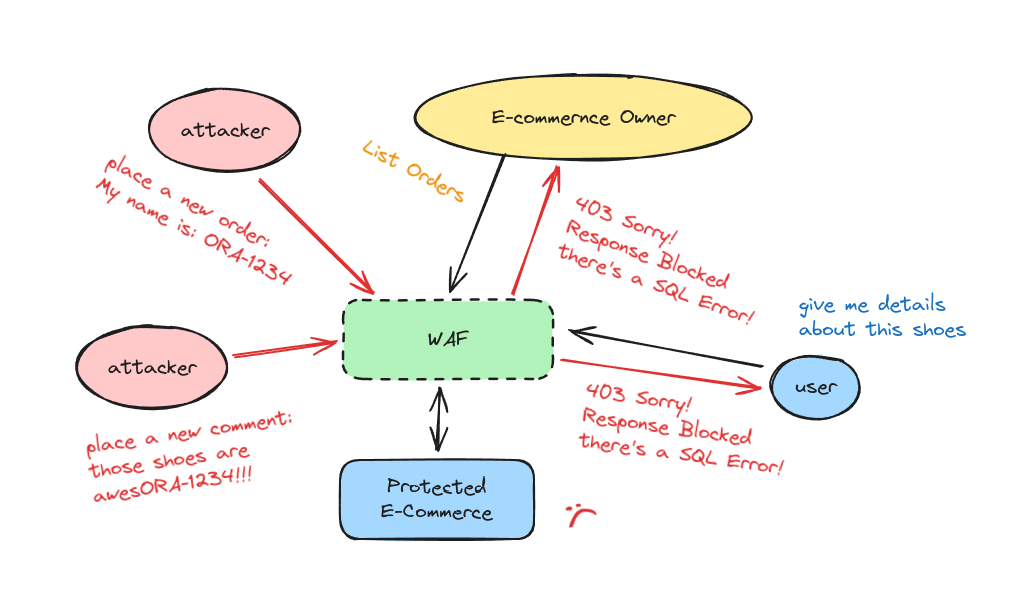

Sicuranext Blog
Response Filter Denial of Service (RFDoS): shut down a website by triggering WAF rule
TL;DR: Basically, if a target website is protected by a WAF using the OWASP Core Rule Set or Comodo Rule Set or Atomicorp Rule Set, you can send th...
Postman leaked secrets
#infosec #cybersecurity #ethicalhacking #news #privacy #nostr


(The) Postman Carries Lots of Secrets ◆ Truffle Security Co.
Postman, the popular API testing platform, hosts the largest collection of public APIs. Unfortunately, it’s become one of the largest public sour...
Backdooring Dotnet Applications
#infosec #cybersecurity #ethicalhacking #news #privacy #nostr
StarkeBlog - Backdooring Dotnet Applications
DHEat DoS attack against SSH
#infosec #cybersecurity #ethicalhacking #news #privacy #nostr
Positron Security
Grafana backend sql injection affected all version
#infosec #cybersecurity #ethicalhacking #news #privacy #nostr


0xfd's blog
Grafana backend sql injection affected all version
Grafana backend sql injection affected all versionVuln DescriptionThe open-source platform for monitoring and observability to exploit this sql inj...
18 vulnerabilities in Brocade SANnav
#infosec #cybersecurity #ethicalhacking #news #privacy #nostr
18 vulnerabilities in Brocade SANnav - IT Security Research by Pierre
Command Injection Vulnerability
In Progress Flowmon
#infosec #cybersecurity #ethicalhacking #news #privacy


Rhino Security Labs
CVE-2024-2389: Command Injection Vulnerability In Progress Flowmon
CVE-2024-2389 unauthenticated command injection vulnerability found in Progress Flowmon server.
Vulnerability on the official #Matrix client for #Android
#element
#infosec #cybersecurity #ethicalhacking #news #privacy #nostr


Shielder
Shielder - Element Android CVE-2024-26131, CVE-2024-26132 - Never Take Intents From Strangers
A writeup about two intent-based Android vulnerabilities CVE-2024-26131 and CVE-2024-26132 in Element (Matrix).
An Obscure Actions Workflow Vulnerability in Google’s Flank
#infosec #cybersecurity #ethicalhacking #news #privacy #nostr


Adnan Khan - Security Research
An Obscure Actions Workflow Vulnerability in Google
An Obscure Actions Workflow Vulnerability in Google
LosdMaster csrf vulnerability
#infosec #cybersecurity #ethicalhacking #news #privacy #nostr


Rhino Security Labs
CVE-2024-2448: Authenticated Command Injection In Progress Kemp LoadMaster
This blog covers 2 vulnerabilities discovered by Rhino Security Labs in Kemp LoadMaster load balancers: CVE-2024-2448 and CVE-2024-2449.
OpenSecurityTraining2
Architecture 1005: RISC-V Assembly
OpenSecurityTraining2
#infosec #cybersecurity #ethicalhacking #news #privacy
Architecture 1005: RISC-V Assembly
This class teaches RISC-V assembly language. It requires you know C programming.
Architecture 1005: RISC-V Assembly
OpenSecurityTraining2
#infosec #cybersecurity #ethicalhacking #news #privacy
Architecture 1005: RISC-V Assembly
This class teaches RISC-V assembly language. It requires you know C programming.
