Are you a #cybersecurity enthusiast and privacy minded?
Do you want to win #Threema license Key?
Rumor has it only those who can read logs will find the way in.
👀 Clues? Na....
👉 Move -> Fast #Threema #privacy
https://carlostkd.ch/threema

ᑎOᔕTᖇ
Nostr@carlostkd.ch
npub1k3dv...k7dv
If something does not go right
Go to #nostr
What the NULL?! Wing FTP Server RCE
#infosec #cybersecurity #ethicalhacking #news #privacy


RCE Security - Your European Offensive Security Partner
What the NULL?! Pre-Auth Wing FTP Server RCE (CVE-2025-47812) | RCE Security - Your European Offensive Security Partner
Modern Offensive Security and (Continuous) Penetration Testing
Accessing Sensitive Cloud Data via "Synology Active Backup for Microsoft 365"
#infosec #cybersecurity #ethicalhacking #news #privacy


When Backups Open Backdoors: Accessing Sensitive Cloud Data via
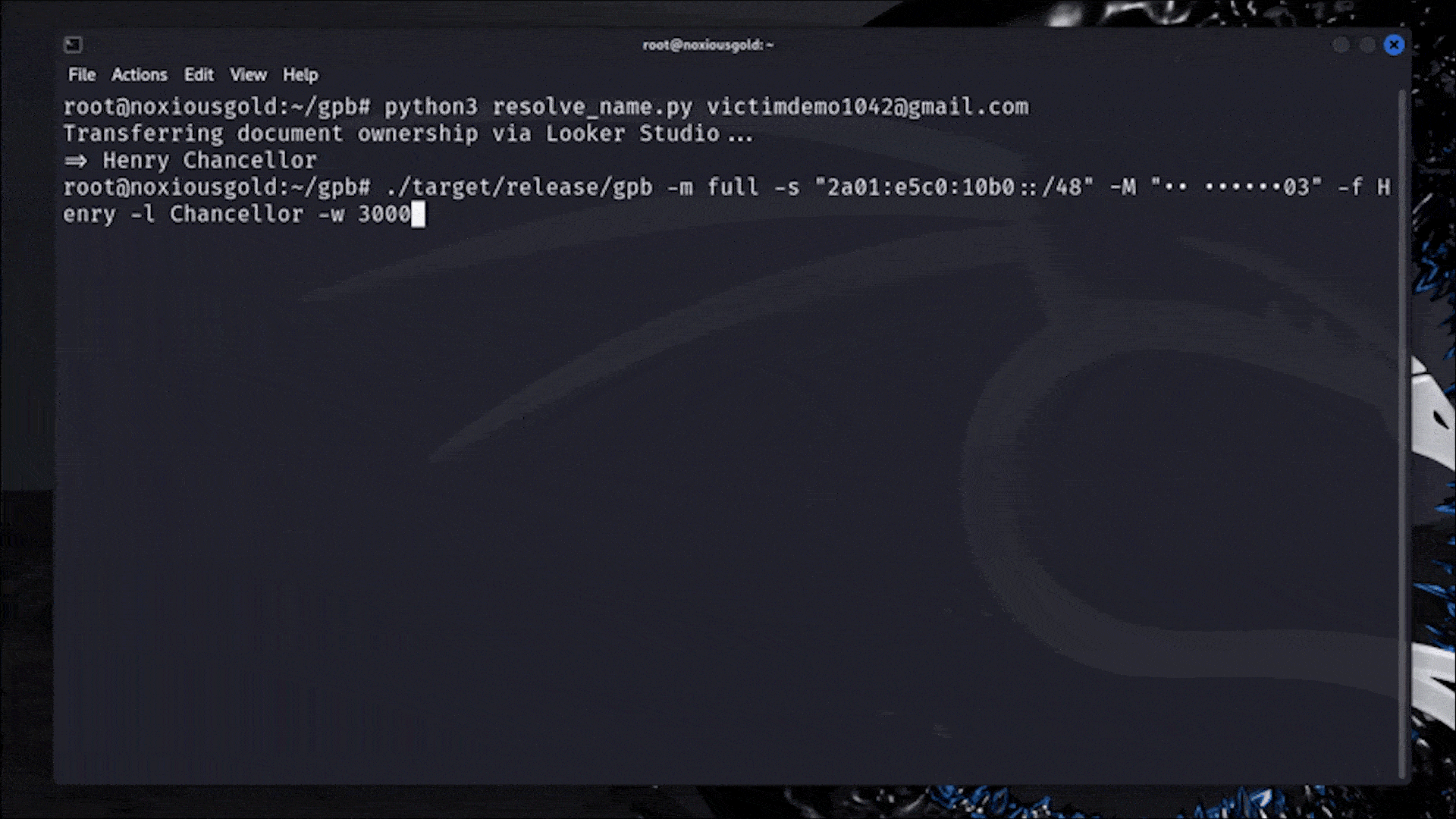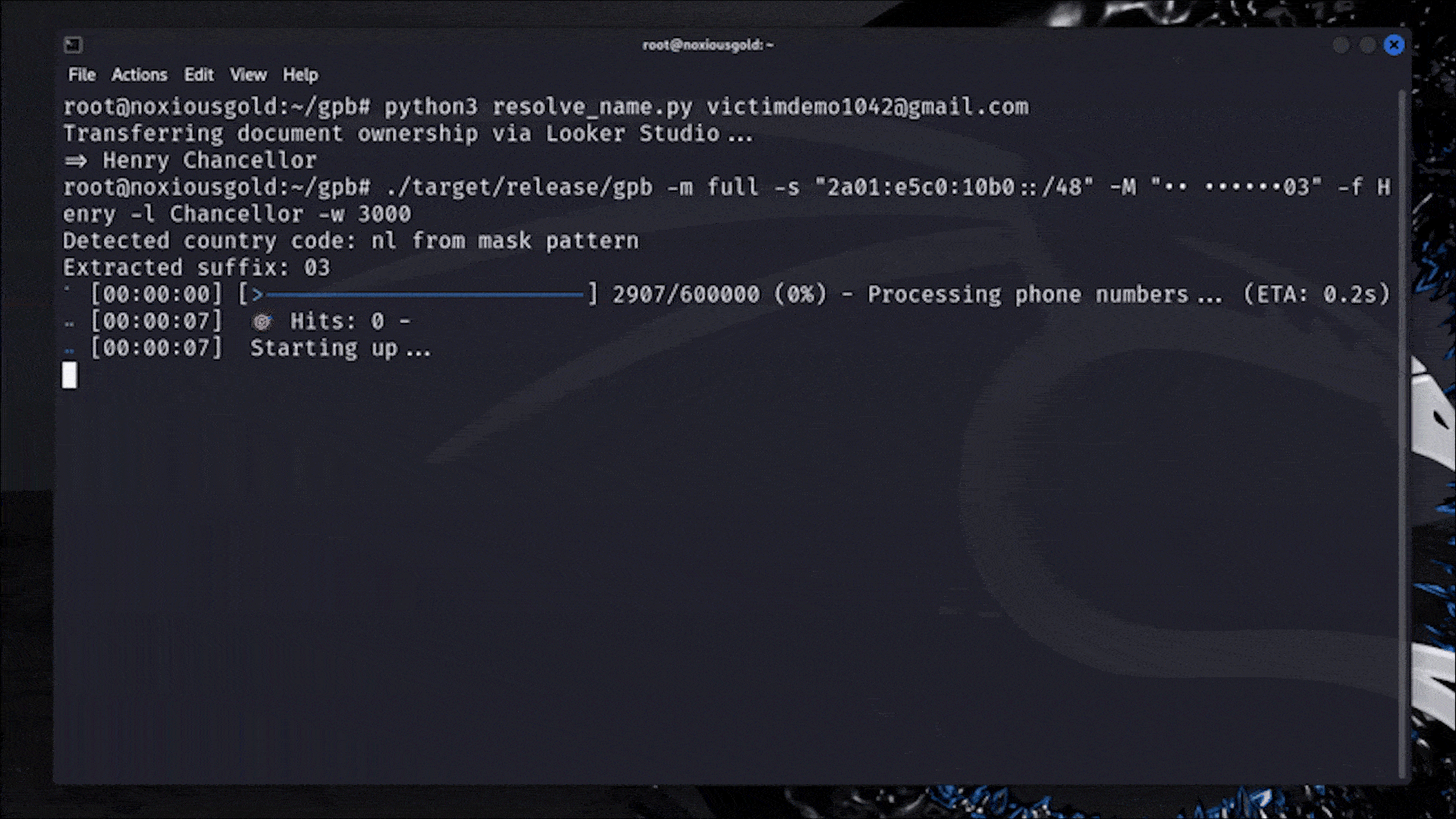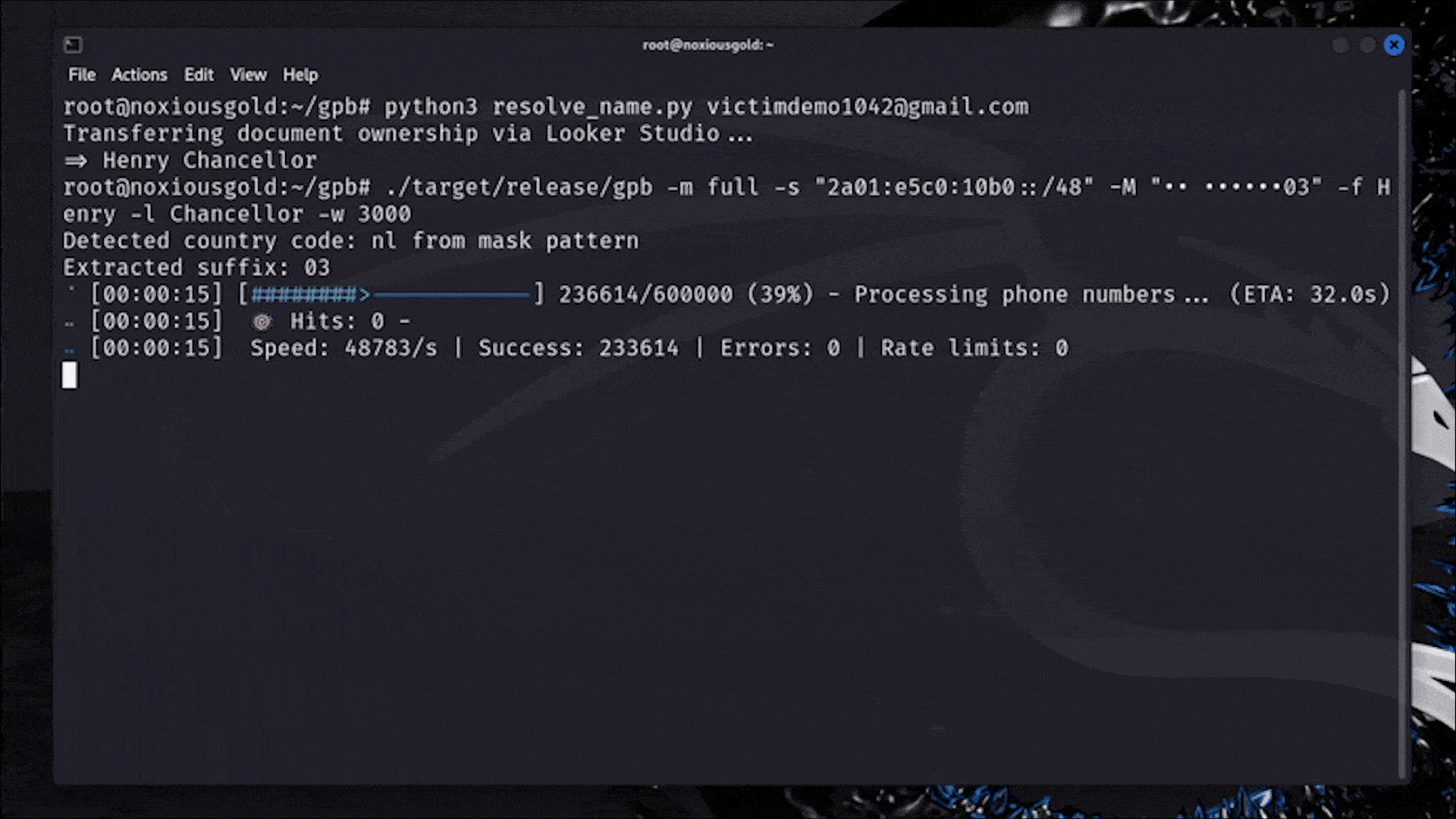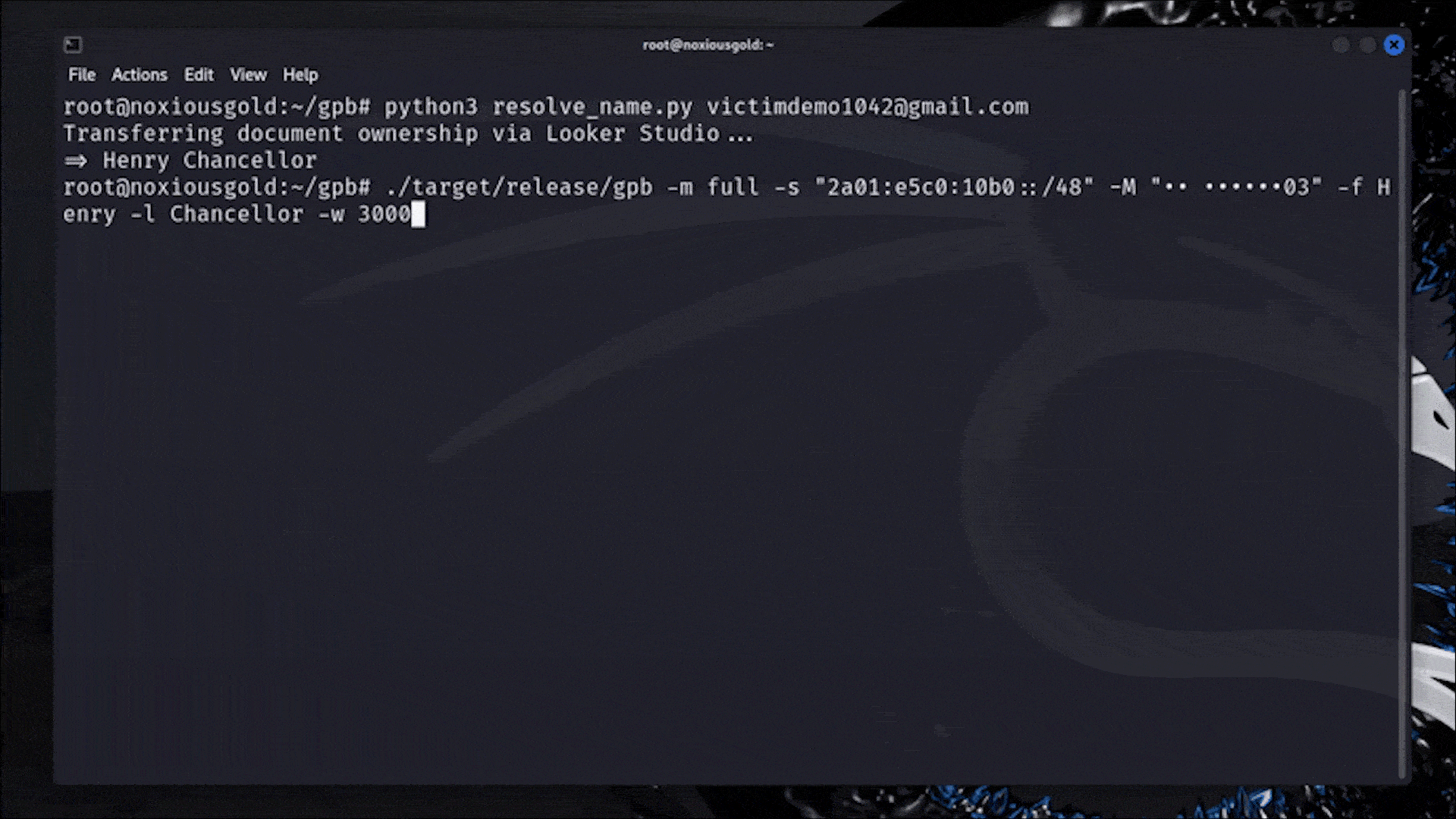
Bruteforcing the phone number of any Google user
#infosec #cybersecurity #ethicalhacking #news #privacy

brutecat.com
Leaking the phone number of any Google user
From rate limits to no limits: How IPv6
GitHub MCP Exploited
 #infosec #cybersecurity #ethicalhacking #news #privacy
#infosec #cybersecurity #ethicalhacking #news #privacy

GitHub MCP Exploited: Accessing private repositories via MCP
We showcase a critical vulnerability with the official GitHub MCP server, allowing attackers to access private repository data. The vulnerability i...
Supercharging Ghidra: Using Local LLMs
#infosec #cybersecurity #ethicalhacking #news #privacy
https://medium.com/@clearbluejar/supercharging-ghidra-using-local-llms-with-ghidramcp-via-ollama-and-openweb-ui-794cef02ecf7
How a single line of code can break your IPhone.
#infosec #cybersecurity #ethicalhacking #news #privacy
How a Single Line Of Code Could Brick Your iPhone | Rambo Codes
Gui Rambo writes about his coding and reverse engineering adventures.
Three new vulnerabilities found related to IXON VPN
#infosec #cybersecurity #ethicalhacking #news #privacy
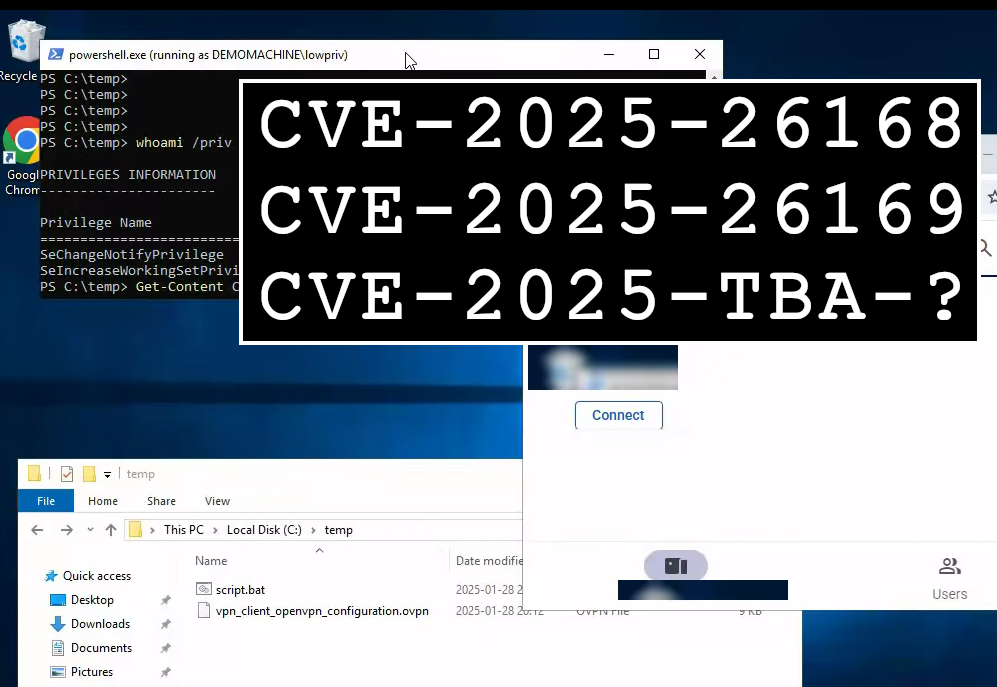

Shelltrail
Three new vulnerabilities found related to IXON VPN client resulting in Local Privilege Escalation (LPE) and [REDACTED] | Shelltrail
The post explains the process of finding and exploiting three vulnerabilities found in the IXON VPN client.
Have you ever wondered why you have to provide personal information when shopping online?
 #infosec #cybersecurity #ethicalhacking #news #privacy
#infosec #cybersecurity #ethicalhacking #news #privacy

Threema
Data Minimization: The Secret Recipe for Sustainable Digitalization of Universities
Have you ever wondered why you have to provide personal information when shopping online? All too often, information such as the phone number and d...
Uncovering a 0-Click RCE in the SuperNote Nomad E-ink Tablet
#infosec #cybersecurity #ethicalhacking #news #privacy
lnbc1u1pnlja6epp5c7x89vu6l728hgj9ujqsnm4y0l9ttmcqp9d2qxtt874qnetd350shp5am8retswkqjh3yqae52j4j3azz9wefg6sycwky88u7pflz0qu8yqcqzzsxqyz5vqsp5zjy6pf73tyq9zsuln9arc97vhy6tmw9kqcsrfwlqzml38mh20qas9qxpqysgqmgvatxhljz38vur4kwrhe5n8vx3w99gywn4pexek9kkdzl2cgcg8exv0jatyz8h65zhm4l3vkekqjx3m5a5x7848pj2rjeaqjwf92psqmjeay0
https://www.prizmlabs.io/post/remote-rootkits-uncovering-a-0-click-rce-in-the-supernote-nomad-e-ink-tablet
Path Traversal Vulnerability in AWS SSM Agent's Plugin ID Validation
#infosec #cybersecurity #ethicalhacking #news #privacy
lnbc1u1pnlvyd8pp5kgzeclchwlpuwhz0dyghxt3kzjpyw82mgcxz480tx74cc8f96dxqhp5hvta74rmeym9fq345k60w36wzw8mcjv4tcwkpgs25aylrfyxelgqcqzzsxqyz5vqsp5mc7v0lwm4wjddjr8zc82actulf7xq5cyw9c8zxwwjqk646vnqvps9qxpqysgq5rxn2fqc5fy2eaxphcrt3cukp3segnd8psrpcdc8lf4q66df4qznj2q97rv7wynxv583xk5tearq0g3ap7d6s4uyfl050syvruz2hxcqw86anr


Cymulate
Path Traversal Vulnerability in AWS SSM Agent's Plugin ID Validation
Improper input validation in AWS SSM Agent's plugin ID exposes systems to path traversal and privilege escalation attacks.
WhatsApp MCP Exploited: Exfiltrating messages history via MCP
#infosec #cybersecurity #ethicalhacking #news #privacy
lnbc1u1pnl82xtpp55quvva9fxhz0dzmghs76sclxpzqzc4a0cprldzcc4egudrvjzq4qhp5gfypxpkugcg8382zr84qwmrf64gz4x3sksp2htcqnv2agxce4rnqcqzzsxqyz5vqsp5uxvcqcyu430hmwyd4kv88eaq42efggfqwupanqkx2pa5zlhwl2ws9qxpqysgqjt80xdtcfyhu859s3gj857t9um8yvmx373375xd82678u792wxxzennmgxfhd2d605pq8fwkpp22fsnu8ujc2wllsjyenmull0w75ecq27cay5


WhatsApp MCP Exploited: Exfiltrating your message history via MCP
This blog post demonstrates how an untrusted MCP server can attack and exfiltrate data from an agentic system that is also connected to a trusted W...
ZendTo NDay Vulnerability Hunting - Unauthenticated RCE in v5.24-3 <=
#infosec #cybersecurity #ethicalhacking #news #privacy
lnbc1u1pn7uggupp5s2e77qts3lc5zes668fz6qlsp7rmg37l259pxw57aapwkxxyuf4shp5k4766ypufl0ft3wd95yzw4pwjcjpwnddj44jvpvvjvk3vjh2q33qcqzzsxqyz5vqsp5c4pqmwayr5j756c0pd6ndfhfw86jxzxtgng5nmfmuf5agh04j89q9qxpqysgqkt278uv5apu2r389t3802j9vv39lj5w3wp6fxy7v0d4cvny7xyrp85hgm563yq0kzd6p44fmryln8ulp0gvted3jrxz4p2ka03vpfkgqusjxm4
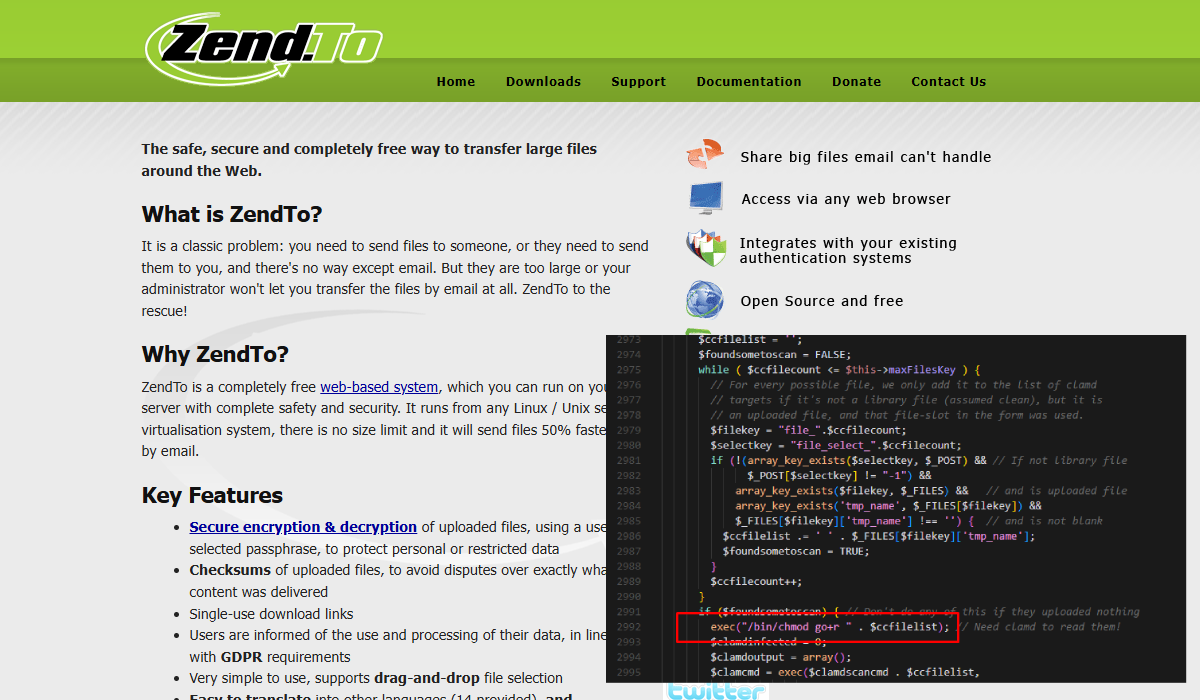

Research Blog | Project Black
ZendTo NDay Vulnerability Hunting - Unauthenticated RCE in v5.24-3 <= v6.10-4
Discovering NDay flaws in ZendTo filesharing software highlighted an interesting fact: without the issuance of CVEs, vulnerabilities can easily go ...
Hacking the Call Records of Millions of Americans
#infosec #cybersecurity #ethicalhacking #news #privacy
lnbc1u1pn7656ppp5xuqpz78x6sjua8x7j2rw8l7j549uv9cpr49cmy02t07en9el434shp5jl2v9s7lpvs6alum6q32k60m3zkfs8klldkghfz9x94ugufga20scqzzsxqyz5vqsp5r8gqzmrvjxkgs4jy2fgnmdx5eypcqfhsxj0c2y55350lxp7az2mq9qxpqysgqx5ajxwdfydqnfskdtp4skckmn80mpmx9vfmphvdd0w6zgnplh9csprr75l89g23kcykrfp89dphjem8t6rztrq4ew9n584k0837mg5sq6mw8n2


Evan Connelly
Hacking the Call Records of Millions of Americans
Imagine if anyone could punch in a phone number from the largest U.S. cell carrier and instantly retrieve a list of its recent incoming calls—com...
Next.js and the corrupt middleware
#infosec #cybersecurity #ethicalhacking #news #privacy
lnbc1u1pn7vefvpp5xpktux2mvm5h20jal5ud372ryrw5a0n6t0pm994sgzzgnhpwdfxshp5q5v2ezgu0ktd3yx8uhyjwh8qq920atsnz4mwqrhu9e827dhusg3qcqzzsxqyz5vqsp5480lepjppeql73y0r8fyqs5nfy9tc8gzjzg79lfgtrqajkehj7yq9qxpqysgq5ud2ws9adl0xdhz4aalnvdr6gpkn43q62kgccqlsflxu4qfuppvhkvrf5d743hxrxehl92626mvvk94q74e9f908x5004pjjvxdfspsq5yfc2r
zhero_web_security
Next.js and the corrupt middleware: the authorizing artifact
CVE-2025-29927
CodeQLEAKED – Public Secrets Exposure Leads to Potential Supply Chain Attack on GitHub CodeQL
#infosec #cybersecurity #ethicalhacking #news #privacy
lnbc1u1pn7vcafpp5k64drzfa4tggzcsv05qhlz2pa73cqp6yfafvdap6jfq39sm8udpshp5ktgjl7qts8rjf6sawdystkjpsamhhakrnf37jwa0g43jcdrf9gzqcqzzsxqyz5vqsp557z7hdf8gru8ur2xwsx2g7dev288w94f4stacxuu70njlwrhdkkq9qxpqysgqzyvgjrd8gxvzhauaz5549l22443wgc5r2dfhdrdagx2u2mc3fjvykkphqpylq8tkksehugvfngxr6p3tm32wrxaelm6s2myjupnltjsp4qs053
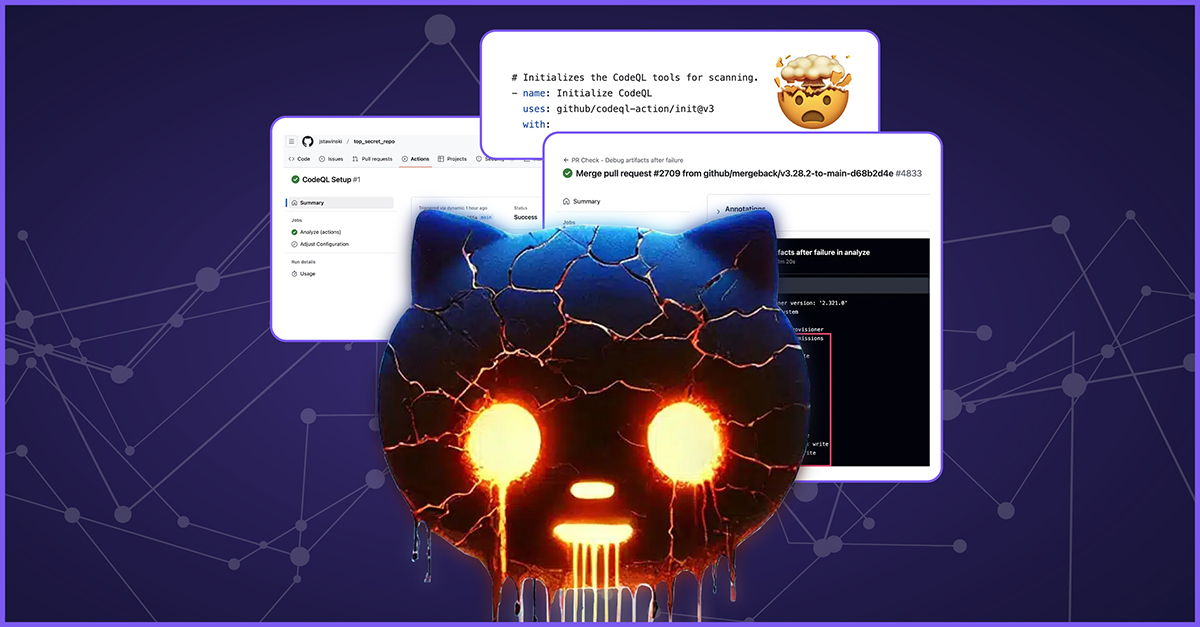

Praetorian
CodeQLEAKED – Public Secrets Exposure Leads to Supply Chain Attack on GitHub CodeQL | Praetorian
How Did We Get Here? Secret Scanning Background Finding the Token Investigating Impact Start Your Engines Executing the Proof of Concept What if Yo...
Behind the Schenes of a Chinese Phishing-As-A-Service: Lucid
#infosec #cybersecurity #ethicalhacking #news #privacy
lnbc1u1pn7vchdpp5t0953qcsh6twztf0ct4rnelk89ycstt4a9xpssd9fhlvms7c45jqhp5dswrqjhy9arckfwd2rqhddp7q6tan4nrzx2qqn4gvvufgwjt97mqcqzzsxqyz5vqsp5qk8wqgpykjcqf55wfyphh78x5fpda22ult493x56wghn9zxnlduq9qxpqysgqjt0z92c0mse55t5q0vktupaml2a29hk7x5fd2ej5lgx9ng98ksaku4gghwc79j6xt80gah9nzf6ljmuv0ejug50v7sw8yus3s0xzk6sp6ses68
PRODAFT CATALYST
BLASTPASS iMessage exploit
#infosec #cybersecurity #ethicalhacking #news #privacy
Blasting Past Webp - Project Zero
An analysis of the NSO BLASTPASS iMessage exploit Posted by Ian Beer, Google Project Zero On September 7, 2023 Apple issued an out-of-band securit...
Blacklock Ransomware:
Intrusion into the Threat Actor's Infrastructure
#infosec #cybersecurity #ethicalhacking #news #privacy
lnbc1u1pn7vcqlpp5vvxv7qjzrgef9eunljnxpfw2a8c5y858ptta46juzx6dyj9tczeqhp57hmcxam3g3kl5j4e7kgvjs89vjhprerk90su2p09h9c7udutnydqcqzzsxqyz5vqsp5ffwvpqrv2x6sffyu7m46xh0j3c4jcy7dtc05h39vndwqmy59hwfq9qxpqysgq2aum572j3mu5wylmtt6ule9ndqhrec8fjkhxfek8mlewlsqkgyhzq76ghwgg6fyu6sdm9zcec698rct6n3hqn22n6na8f46mwyx2qfsqjn8csf


Resecurity | Blacklock Ransomware: A Late Holiday Gift with Intrusion into the Threat Actor's Infrastructure
Unauthenticated RCE in Default-Install of Appsmith
#infosec #cybersecurity #ethicalhacking #news #privacy
https://rhinosecuritylab
lnbc1u1pn788gmpp5a8xp5azlu0tjvsaukmw9sjy32ucd33tx379r6rky9xkgf44cmpmshp5fw6mltpr4pcle066097ge428vrc37r45r5g2exhz0hmhdy068dlqcqzzsxqyz5vqsp54s8ggc2zkmq92hj5pckckp2le4g95zreqt8x0sspwfydv932xulq9qxpqysgqhphagsyayt2mdw73524djt3hxts3qhkh0ky6ft36eu0m66fqrv7z2k2unc27hyr907nvhzk22hp08stlhjj338lngcxey3v435yqw8cpxglru2