Here is a pretty detailed quarterly report on my Horcrux project for OpenSats, if that interests you: https://mattlorentz.com/2025/12/29/horcrux-end-of-year-update.html

Matt Lorentz
matt@nos.social
npub16zsl...92l7
Technologist, solarpunk, gamer, backpacker, passionate about using the internet to push more power to more people.
Maybe we should start a club. There must be at least three of us!
View quoted note →
Playing ambient audio to keep your Nostr signer alive on iOS is hilarious and definitely against Apple's rules, but I love it. More power to you 😂
View quoted note →
Is anyone here going to EthDevner in February? I am not an ethereum person at all, but I have met a lot of cool people over the years (who are also not big ethereum people) who have been to this conference and loved it. I think I might go this year. They have a track for "Cypherpunks, Solarpunks & Communities". Idk what ethereum has to do with solarpunk but I kind of want to find out.
If I vibe code my own workout app will I actually work out or no? 👍 / 👎
Ok hodlbod has been COOKING on his frost signer thing with email login. I just got a demo from him and it has me more excited about Nostr than I have been in a long time.
- users can sign into Nostr apps via email (or someday any other identity system they like. Phone? Facebook? snail mail? Āhau?) but behind the scenes they still have a private key
- no server or company ever needs a full copy of their private key
- at any point they can extract their Nostr key from the system to use another one (like a bunker, hardware signer, or just a different group of signing servers, etc.)
The big problem with Nostr onboarding is that people need to put in a significant amount of work to understand and manage keys before they even get a chance to get any value out of the software. But pomade enables someone to join without thinking about keys, *and later* start caring and still be able to take full custody of their key. It is the second part that nobody has really done before, on Nostr or anywhere else that I know of. It's not bulletproof, but it combines all the best tech we have to balance ease-of-use, security, and user control.
@hodlbod I think at some point I heard you say you get a summary of recent Nostr events every day. Is that from a DVM? Have you written about this somewhere? I would like to try something similar.
I wrote up some instructions for running a promenade signer, if that's something that interests you. Promenade creates a cluster of servers that cooperatively sign of Nostr events without any of them knowing your Nostr secret key. Bleeding edge identity tech. Join us! View article →
Happy horrible software vulnerability day everyone
React2Shell (CVE-2025-55182)
This website speaks to the nerd inside me on so many levels. I think I'm going to give the "No S Diet" a try.
Everyday Systems: Systematic Moderation for sustainable good habits
Simple, practical solutions to everyday problems.
I just posted a project update video for Keydex that shows the current features and future plans. Plus an announcement that I'm renaming the project from Keydex to Horcrux! Check it out: 

tchncs
Keydex Thanksgiving Update
This is the thanksgiving progress report for my app Keydex. Read more at https://github.com/mplorentz/keydex.
I'm so excited that Satellite is back. It's always had my favorite design of any Nostr app.
View quoted note →
I've been quiet lately but I've just been very heads down trying to get Keydex ready for it's first alpha usability test, which I'm about to head to right now! I'll try to post a project update this week, as I passed the halfway point on my (relatively tight) 4 month timeline recently.
I just did a weird thing with gift wraps in Keydex and I want to make sure it's not dumb. I'm having a bug where lockboxes are showing back up on the devices of key holders after they have been removed. Like this:
1. Alice invites Bob to be a key holder for their lockbox
2. Bob accepts
3. Alice publishes a shard of the lockbox data for Bob to download, gift wrapped and addressed to Bob.
4. Bob changes their mind and deletes the lockbox from their device.
5. Later when Bob reopens the app it downloads the shard event again and recreates the lockbox.
Of course I could maintain some local state about what has been deleted, but it would be better to just nuke the shard from the relay. We could ask the original publisher to do it, but we can't guarantee they are online. So what if we just include the ephemeral key used to gift wrap the shard in the seal? Now Bob can publish a NIP-09 deletion request to delete the shard.
I could see this being useful in other places too. For instance you could have a type of direct message that gets deleted from relays as soon as it is downloaded by the recipient.
Fun milestone for Keydex today: I had my first successful restore of data. I was able to fire up several copies of the app and create a lockbox, break it into shares, distribute them to peers via Nostr, initiate recovery, approve the recovery request, and reassemble the data.
There is still a ton of work to do but having the core flow working makes all the future changes feel small and incremental by comparison.
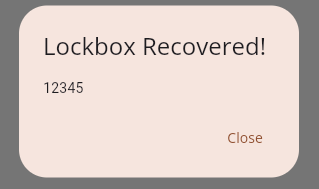

Keydex is going to be the first Nostr app I'm aware of that uses relays exclusively to relay data from one peer's device to another, not for long-term data storage. I'm going to use NIP-40 expiration tags on all events so that they only live on the relay for a few days, which makes Keydex closer to a peer-to-peer application that uses Nostr as the transport (and identity) layer.
Day 2 using Github's spec-kit for development did not go as well. The AI and I got lost trying to write reams of overly generic TDD test stubs. It felt like the AI couldn't really get a clear picture from just the spec requirements what it should be testing before the actual implementation code was written.
So today I changed course and changed my constitution (the like underlying spec doc for the repo) to use an outside-in development approach instead of TDD and we made a lot of progress. I also got a new playwright MCP set up for browser automation and it's working a lot better than the last one I had. After some considerable setup the LLM was generally able to run the app in the web browser and click around to test its own changes.