noble cryptography v2 is out. Improvements include Schnorr implementation in 5kb noble-secp256k1, hybrid pq algorithms, OPRFs, friendly wrappers around native WebCrypto, better security, and much more.
Live on GitHub, NPM & JSR.

Paul Miller
paul@paulmillr.com
npub10jcn...3kag
Noble cryptography. OSS, infosec.
#WeAreAllFiatjaf
Announcing noble-post-quantum: minimal JS implementation of ML-KEM, ML-DSA and SLH-DSA.
Also known as Kyber, Dilithium and SPHINCS+. Only 2000 lines of code - great learning resource for anyone who’s messing with PQ stuff.
Check out README for algorithm comparison and usage guidelines. 
GitHub
GitHub - paulmillr/noble-post-quantum: Auditable & minimal JS implementation of public-key post-quantum cryptography
Auditable & minimal JS implementation of public-key post-quantum cryptography - paulmillr/noble-post-quantum
2023 progress on JS cryptography:
- noble-hashes: 400K => 1.7M downloads per week
- noble-curves: ~0 => 0.9M, got 2 audits
- noble-ciphers: 0 => 25K
- Finally adopted by ProtonMail, MetаMасk, Rainbow, Rabby, ethers, web3.js, viem
Takes time, but we’re getting there.
Signal is cool, but do you know what is cooler? Chatting on decentralized social network. We’ve implemented and audited end-to-end encrypted direct messaging for nostr.
Thanks to Jon (npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn), OpenSats, Michael (npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c), ekzyis (npub16x07c4qz05yhqe2gy2q2u9ax359d2lc0tsh6wn3y70dmk8nv2j2s96s89d), Vitor (npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z), Cure53, Matthew Green and everyone else involved.
https://github.com/nostr-protocol/nips/blob/master/44.md, 
GitHub
GitHub - paulmillr/nip44: NIP44 encrypted messages for nostr. Spec and implementations
NIP44 encrypted messages for nostr. Spec and implementations - paulmillr/nip44
Signal is upgrading all conversations to a combination of X25519 and CRYSTALS-Kyber. Probably the first large-scale deployment of Kyber. 
Signal Messenger
Quantum Resistance and the Signal Protocol
The Signal Protocol is a set of cryptographic specifications that provides end-to-end encryption for private communications exchanged daily by bill...
Someone published NPM fork of noble-curves that sent private keys to a server in China. Be careful and check for typos 

Phylum Research | Software Supply Chain Security
Typosquat of popular Ethereum package on npm sends private keys to remote server
On Aug 3, 2023 Phylum’s automated risk detection platform alerted us to a series of suspicious publications on npm. The attacker eventually publi...
Ever wanted a privacy-focused nostr web client? http://nostr.spa (https://paulmillr.com/demos/nostr) got you covered! It’s simple, open-source, and does not require a private key. You can even send messages, pre-signed somewhere else.
Announcing noble-ciphers: tiny 0-dependency cryptographic library, implementing Salsa20, ChaCha, Poly1305, AES-SIV and others. Bonus: a reasonable wrapper around native WebCrypto's AES. Check out its README for some insights: 
GitHub
GitHub - paulmillr/noble-ciphers: Audited & minimal JS implementation of Salsa20, ChaCha and AES
Audited & minimal JS implementation of Salsa20, ChaCha and AES - paulmillr/noble-ciphers
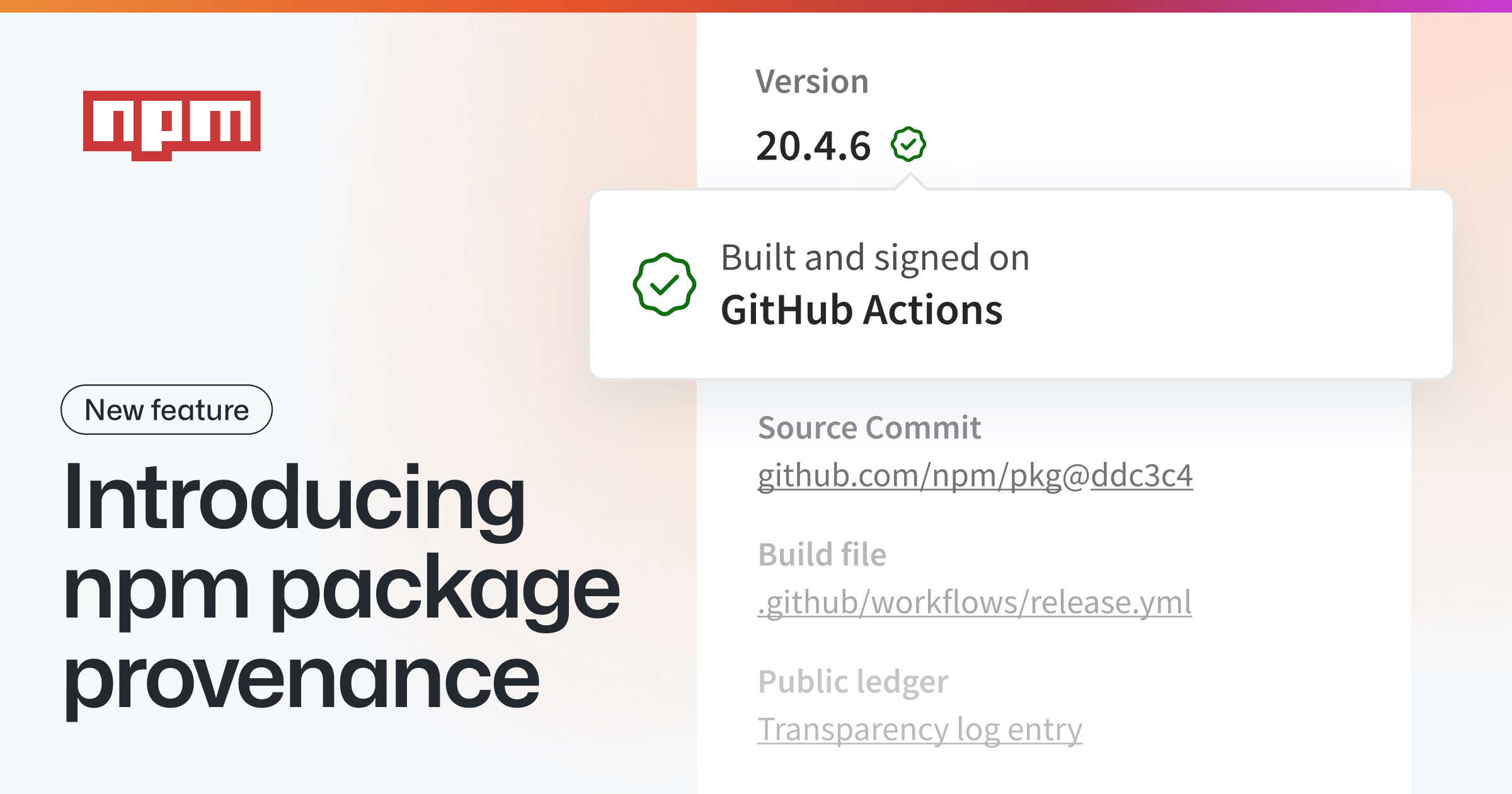
New noble cryptography releases are out:
- NPM provenance is now used for transparent builds, to strengthen supply chain security [1]
- ed25519 and ed448 now provide non-repudiation (Strongly Binding Signatures). The feature is not present in most other libraries [2]
- tweetnacl users (including DJB's C version): it's time to switch away. It does not provide SUF-CMA, meaning, in some circumstances, the signatures are malleable [3]
1. 2. https://csrc.nist.gov/csrc/media/Presentations/2023/crclub-2023-03-08/images-media/20230308-crypto-club-slides--taming-the-many-EdDSAs.pdf
3.
2. https://csrc.nist.gov/csrc/media/Presentations/2023/crclub-2023-03-08/images-media/20230308-crypto-club-slides--taming-the-many-EdDSAs.pdf
3.

The GitHub Blog
Introducing npm package provenance
How to verifiably link npm packages to their source repository and build instructions.

A Few Thoughts on Cryptographic Engineering
EUF-CMA and SUF-CMA
There are two common formal definitions for the security of a digital signature scheme. Each of these definitions is presented as a “gameR...
Twitter launched encrypted* DMs for verified accounts.
* No sync
* No group chats
* No attachments
* No timers
* Vulnerable to MITM
* No reporting (msg franking)
* No Forward Secrecy
* No Key Transparency
* Private keys are NOT erased after web logout
https://help.twitter.com/en/using-twitter/encrypted-direct-messages
Elliptic curve calculator just got a new big update:
1. Select a curve, including NIST, ed448, BLS
2. Create custom curves
3. Add and multiply points
4. Sign messages with different hashes
The demo works offline. It’s great for learning! Check it out:
Paul Miller — Noble cryptography
Paul Miller. I make projects which help developers to build awesome things
4KB cryptography. Does that sound safe? Because it should.
Announcing v2 of single-feature modules noble secp256k1 and noble ed25519. secp is just 430 lines of code (4KB gzipped), ed is only 330 lines (3.3KB gzipped) — 4x smaller than previous versions.
Tweetnacl was a great idea. Smaller attack surface means less things that could go wrong. New libraries develop the concept further: there are tons of comments everywhere, describing how things work - makes it much easier for cryptography newcomers to read.


GitHub
GitHub - paulmillr/noble-secp256k1: Fastest 5KB JS implementation of secp256k1 signatures and ECDH
Fastest 5KB JS implementation of secp256k1 signatures and ECDH - paulmillr/noble-secp256k1
GitHub
GitHub - paulmillr/noble-ed25519: Fastest 5KB JS implementation of ed25519 signatures
Fastest 5KB JS implementation of ed25519 signatures - paulmillr/noble-ed25519
@npub1teawtzxh6y02cnp9jphxm2q8u6xxfx85nguwg6ftuksgjctvavvqnsgq5u Verifying My Public Key: "paulmillr"
Hello, world. Message made with #noble-crypto