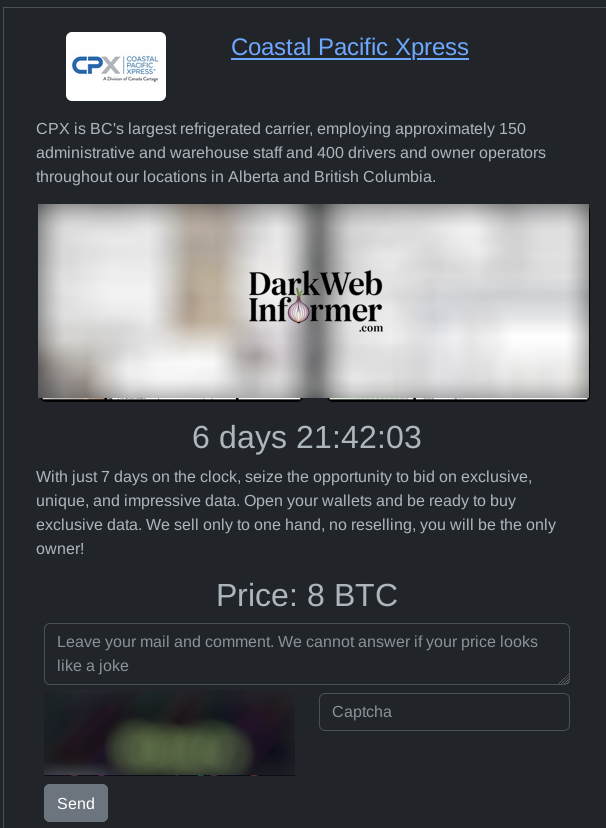
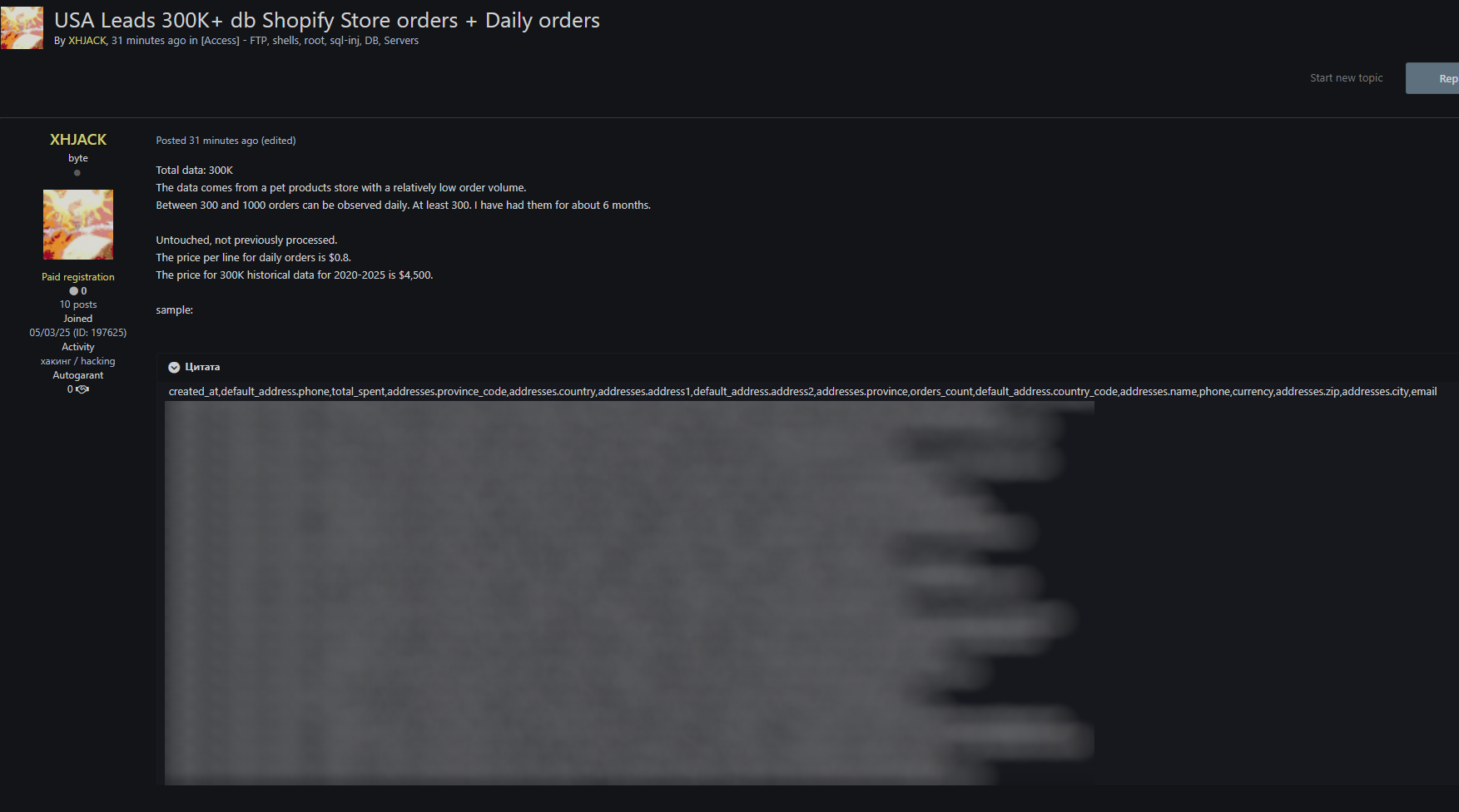
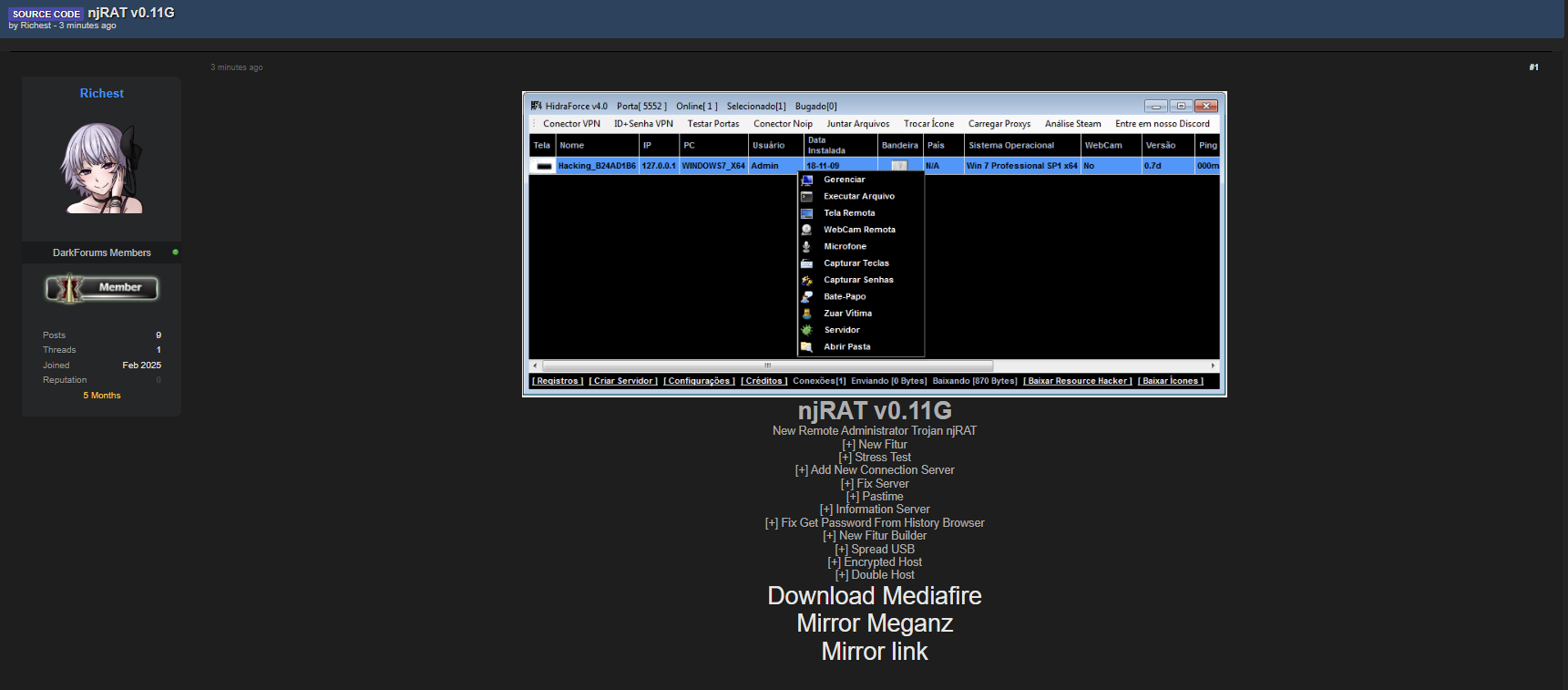
A hacker going by the name Martha Root... takes down a white supremacist dating website and leaks all of the data. Good f*cking shit @BackTwoTheRoot!
okstupid[.]lol


X (formerly Twitter)
Dark Web Informer (@DarkWebInformer) on X
A hacker going by the name Martha Root... takes down a white supremacist dating website and leaks all of the data. Good f*cking shit @BackTwoTheRoo...