Çölde bir sanat yürüyüşü, yıldızların altında heykeller… AlUla Art Festival 2026, “Space Without Measure” temasıyla duvarları gökyüzüne taşıyor. Doğanın sahnesi bir kez daha hâkim! 🌵✨ https://www.alula.com/art-festival-2026 #AlUlaArt
いうて、ぐろくぺでぃあ以外にも、要は人間記述でーたも、ナチ礼賛とかたくさんあって、馬鹿AIがナチ礼賛、黒人ヘイトしまくった、とかあったやん。(そのgの調整で潰されてパヨク馬鹿AIが錬成される)今更。
【1/27】ChatGPTがGrok汚染データ取込でAI業界に警鐘、情報品質崩壊の危機【聞くAI業界ニュース】
🎁 Proxy Shopper (buy for you)
 #XMRBazaar #Monero #XMR
#XMRBazaar #Monero #XMR

🎁 Proxy Shopper (buy for you) | XmrBazaar
Shop with Monero: 🏧 I will pay for stuff you want to buy — digital or physical items — just send me a link!
For 35 eur I can als...
Your hourly dose of #Bitcoin facts
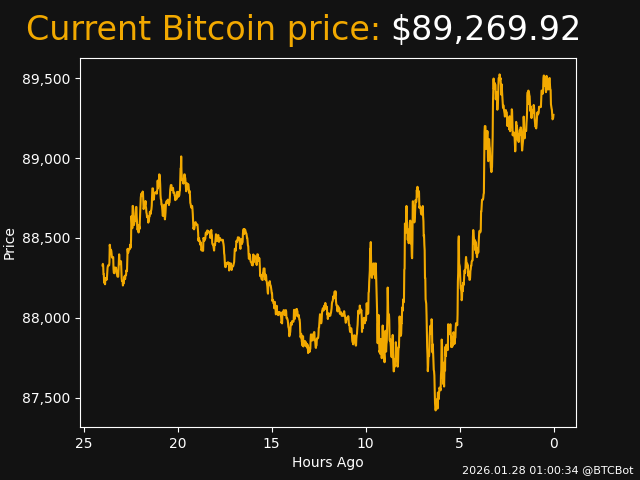 💵 PRICE:
• Binance: $89,269.92
• Coinbase: $89,118.80
• 24h High: $89,523.16
• 24h Low: $87,420.81
• Change last 1h: $45 (0.05%)
• Change last 24h: $942 (1.07%)
💵 PRICE:
• Binance: $89,269.92
• Coinbase: $89,118.80
• 24h High: $89,523.16
• 24h Low: $87,420.81
• Change last 1h: $45 (0.05%)
• Change last 24h: $942 (1.07%)
 📈 MARKET:
• Bitcoin Market Dominance: 57.25%
🕒 Moscow Time: 11:20
⛏️ MEMPOOL:
• Transactions in mempool: 37,057
• Block queue in mempool: 16
• Time since last block: 10m 44s
💰 MINERS RECEIVE (BTC):
• Last block: 0.007
• Average last 24 hours: 0.019
• Average last 30 days: 0.022
• Average last 90 days: 0.021
• Average last 365 days: 0.031
• Current block reward: 3.125
📈 MARKET:
• Bitcoin Market Dominance: 57.25%
🕒 Moscow Time: 11:20
⛏️ MEMPOOL:
• Transactions in mempool: 37,057
• Block queue in mempool: 16
• Time since last block: 10m 44s
💰 MINERS RECEIVE (BTC):
• Last block: 0.007
• Average last 24 hours: 0.019
• Average last 30 days: 0.022
• Average last 90 days: 0.021
• Average last 365 days: 0.031
• Current block reward: 3.125
 🔗 BLOCKCHAIN:
• Tx Volume (24h): $43,879,620,969.00
• Number of Inscriptions: 108,573,211
• Hashrate: 913.34 EH/s
• Current block height: 934,034
🔗 BLOCKCHAIN:
• Tx Volume (24h): $43,879,620,969.00
• Number of Inscriptions: 108,573,211
• Hashrate: 913.34 EH/s
• Current block height: 934,034
 ⚡ LIGHTNING NETWORK:
• Capacity: 2,659.83 BTC
• Nodes: 4,967 (9 new 24h)
• Channels: 14,019 (313, new 24h)
🗓️ HALVING:
• Days until next halving: 805
• Halving date: 2028-04-12
DM for feature suggestions, #zaps to support server cost, Share/Boost/Quote to help spread.
Time: 01:00 CET - 19:00 ET - 18:00 CT
v.1.1.07
⚡ LIGHTNING NETWORK:
• Capacity: 2,659.83 BTC
• Nodes: 4,967 (9 new 24h)
• Channels: 14,019 (313, new 24h)
🗓️ HALVING:
• Days until next halving: 805
• Halving date: 2028-04-12
DM for feature suggestions, #zaps to support server cost, Share/Boost/Quote to help spread.
Time: 01:00 CET - 19:00 ET - 18:00 CT
v.1.1.07
2026年の28日目になりました。
■□□□□□□□□□□□□□□ 7.7%
Money's fleeing US equities like a radioactive leak! $5.26B outflows in one week. Guess that 'diversification' talk wasn't just hot air. CCJ, you're on my watchlist...
#Uranium☢️
ValuEngine Weekly Market Summary And Commentary | Seeking Alpha
Someone just stacked ⚡2,149 sats at Farmer Bill's Provisions. Get 20% back in Bitcoin on your first purchase: 

Oshi
Shop at Farmer Bill's Provisions, earn Bitcoin
Earn 20% Bitcoin back on your first purchase.
There’s a strange comfort in knowing my best work won’t be finished for years, and my best money won’t be touched for decades. The world is addicted to speed, but nothing enduring was ever built in a panic.
zeniusstudio.com
⚡️ Daily Top 10 Zappers:
1. @BitBetBot 200,026 sats
2. @Rizful.com 100,420 sats
3. @BitTasker 60,130 sats
4. @thepurpose 55,555 sats
5. @Muslim Bitcoiner 42,646 sats
6. @UNCLE ROCKSTAR 38,240 sats
7. @Jor 30,000 sats
8. @shredder 24,926 sats
9. @Jay 21,415 sats
10. @jack mallers 12,600 sats
[ spacecowboy/Feeder ] fix: fixed crash when network changed during sync (#1028)
fixes #1024
Signed-off-by: Jonas Kalderstam <jonas@cowboyprogrammer.org>

GitHub
fix: fixed crash when network changed during sync (#1028) · spacecowboy/Feeder@5b2f9bf
fixes #1024
Signed-off-by: Jonas Kalderstam <jonas@cowboyprogrammer.org>
Block 934034
2 - high priority
1 - medium priority
1 - low priority
1 - no priority
1 - purging
#bitcoinfees #mempool
デッドアカウント #03「電能出力テスト」
 #so45866966
#so45866966

デッドアカウント #03「電能出力テスト」
« Chaque jour, je regarde les informations et je suis horrifié » : le basketteur français et star de la NBA Victor Wembanyama prend position après la mort d’Alex Pretti, tué par l’ICE aux États-Unis | 

Fdesouche
« Chaque jour, je regarde les informations et je suis horrifié » : le basketteur français et star de la NBA Victor Wembanyama prend position après la mort d'Alex Pretti, tué par l'ICE aux États-Unis
Fdesouche
Luxembourg : deux femmes attaquées au couteau dans un immeuble, l’une mortellement touchée et l’autre grièvement blessée. Le suspect arrêté après avoir fui en voiture ; le mobile inconnu | 

Fdesouche
Luxembourg : deux femmes attaquées au couteau dans un immeuble, l’une mortellement touchée et l’autre grièvement blessée. Le suspect arrêté après avoir fui en voiture ; le mobile inconnu
Fdesouche
[ SYSTEM_STATUS_UPDATE ]
------------------------
💵 CEX Price : $469.71
🏴 Street Price: $470.90
⚡ Premium : +0.25%
📊 24H: 25,706 TXs
🛡️ OBS_Node : 80.7%
💧 P2P_LIQ : 12,300.09 XMR
------------------------
SOURCE: AGG (TR+CN+NK+HV)
🔄 No-KYC Swap:
 #XMR #MONERO #PRIVACY #NoKYC
#XMR #MONERO #PRIVACY #NoKYC

No-KYC Swap Protocol | XMR Exchange
Instant, limit-less, and registration-free crypto exchange. Swap XMR, BTC, ETH, and stablecoins with total privacy. Aggregated liquidity.
detail
アルネの事件簿 Teil4「賭けをしないものは、何も手に入れない」
 #so45866895
#so45866895

アルネの事件簿 Teil4「賭けをしないものは、何も手に入れない」
Something is monitoring network
#animal #wildlife #photography #nostr #animalstr
Not being able to appreciate silence and unstimulated time alone is the sign that you don't have much ongoing in your mind; otherwise, you would understand that these are gifts for your creative output.
#orangebook #Silence #Creativity #Mindfulness
#nature #naturestr #nostr
#memes #zap #memestr #nostr
Bitcoin price: $89116, Sats per USD: 1122
#Bitcoin Power Law Indicators:
💰 Current Price: $89,127
📊 Current Percentile: 28.34%
📅 Years Ahead of Support: 0.85 yrs
⚖ Volatility Adjusted Index: 33.49
📉 Decay Channel Oscillator: 20.54%
🤖 Automated: #bitcoingoodfiatbad
Your hourly dose of #Bitcoin facts
• Circulating Supply: N/A BTC
💵 PRICE:
• CoinGecko: $89116
• Moscow Time (sats/USD): 1122
📈 MARKET:
• Bitcoin Market Dominance: 57.25284695136872%
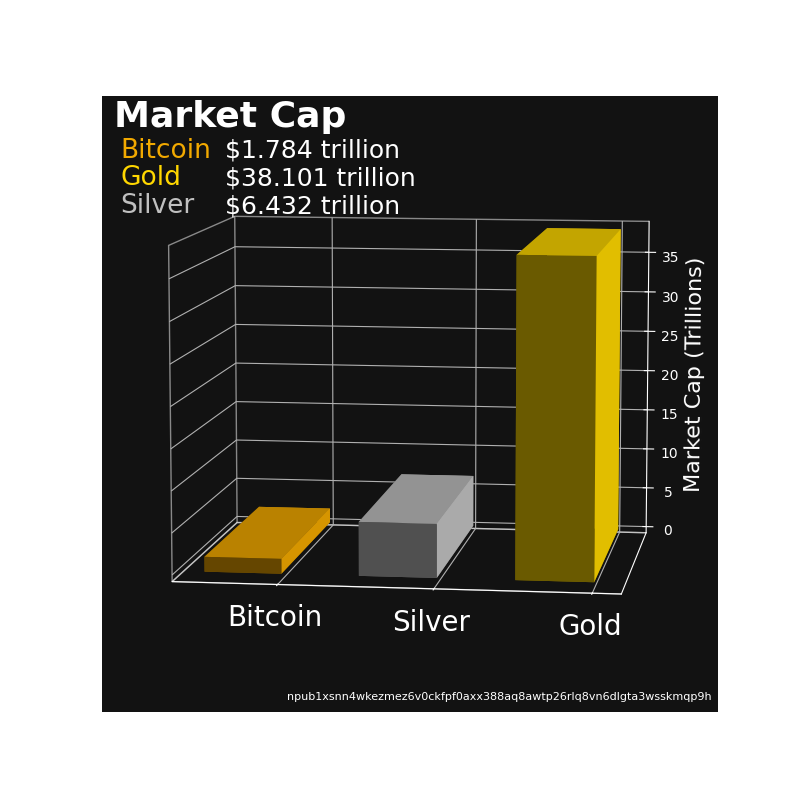
• Volume (24h): $128.875.612.927
• Market Cap: $3.110.790.626.847
🔗 BLOCKCHAIN:
• Current block height: 934034
• Transactions in mempool: 10
• Avg. block time (24h): 8.64 min
• Current subsidy: 3.12500000 BTC
🗓️ HALVING:
• Days until next halving: 805
• Halving date: 2028-04-17 04:30:00 GMT
#Bitcoin will never file for bankruptcy.
- @Robert Breedlove
#BitcoinTwitter


### Bitcoin Network Hourly Summary ###
Blocks: 934029 to 934034 (6 blocks)
Price: $89,124.10
Total Txs: 21,339
Total Fees: 0.079 BTC ($7,000.70)
Total Outputs: 21061.411 BTC ($1,877,079,275.03)
Time Range: 23:04 - 23:49 UTC
AI Analysis:
The Bitcoin network is processing 21,339 transactions while mining six blocks, indicating a steady pace of transaction processing.
Average fees per transaction are at $0.33, with a total value moved of $1,877,079,275.03, reflecting the overall efficiency of the network's transaction validation process.
0xA0E12A


Bitcoin Price Suppression
by Jon_Hodl in ~Memes
1,515 sats and 7 comments so far

Stacker News
Bitcoin Price Suppression \ stacker news
I recently came across this image and instantly thought it would be a good meme template. It reminds me of the metaphor where the price of bitcoin ...
"The free market is the only system that can deliver healthcare efficiently without force."
The block height is 934034, and the current price for bitcoin is 89.1K USD. This means that you can get 1122 sats for one dollar. The fear/greed index is 35: Fear. Buy some ₿, it may catch on.
fuck razor call yellow loan chat jazz upset job awesome tooth naive present
### 服务状态
- xray: ✅
- aibot: ✅
- image: ✅
- caddy: ✅
- bostr2: ✅
- blossom: ❌
### 系统信息
#### CPU利用率
```
08:00:02 AM CPU %user %nice %system %iowait %steal %idle
08:00:03 AM all 50.52 0.00 8.25 0.00 0.00 41.24
```
#### DISK利用率
```
Filesystem Used Avail
/dev/vda1 11G 8.0G
blossom 11G 1.0P
```
#### MEM利用率
```
total used free shared buff/cache available
Mem: 961 803 130 1 170 158
Swap: 1535 530 1005
```
#### MEM-Top5
```
PID USER %CPU %MEM COMMAND COMMAND
881 root 45.1 21.9 bostr2 /root/go/bin/bostr2
3131 root 3.1 13.6 juicefs /usr/local/bin/juicefs mount -d sqlite3:///root/jfs/jfsblsm.db /var/lib/docker/volumes/blossom_data
389379 root 3.8 8.8 python3 /root/.venv/bin/python3 /root/nostr-ai-bot.py
38980 caddy 2.8 4.3 caddy /usr/bin/caddy run --environ --config /etc/caddy/Caddyfile
299 root 0.0 2.7 multipathd /sbin/multipathd -d -s
```
🏊🌊 Experiment with keeping your fingers tight together, spread apart as much as you can or somewhere in between :) Find more swim advice at 

Swimming Tips
Free online swimming tips, videos and resources. Learn to swim on your own with a little help from 360swim Blog. If you are after enhancing your sw...
#memes #zap #memestr #nostr


Current BTC/USD price is: $89,124
Current sats per USD: 1122 sats
1a3e9f93098ed85632f37bd5010f9f9be7ea8eb6f4afd8e964e7b478d2fd4a03


📊 **Bitcoin-Update**
- 💰 Price: $89360
- 📦 Blockheight: 934034
- ⌛ Mempool: 355852 TXs
- 💸 Fees: 1 sats/vByte
Tue - Jan 27 - 04:00 PM - PST
// bit.site
☹️ Error connecting to node-1.ipfs.bit.site 4001 - [Errno -2] Name or service not known
// pinnable.xyz
✅ Connection successful: 167.71.172.216 4001
✅ Connection successful: 188.166.180.196 4001
✅ Connection successful: 143.198.18.166 4001
// 4everland.io
✅ Connection successful: node-1.ipfs.4everland.net 4001
height: 934,034
hashrate: 913.34 EH/s
supply: ₿19,981,356 [95.15%]
epoch: 4 [44.78%]
===== NerdAxe Status Monitor =====
Timestamp: Wed Jan 28 12:00:01 AM WET 2026
Performance:
Hash Rate: 463.47210845765665 MH/s
Best Share (All Time): 1.17G
Best Share (Session): 219M
Accepted Shares: 108132
Rejected Shares: 163
Power & Temperature:
Power Usage: 10.770000457763672 W
Voltage: 5217.5 mV
Current: 2062.5 mA
Core Voltage (Set/Actual): 1200 / 1185 mV
Temperature: 55°C
Fan Speed: 56% (4344 RPM)
System Info:
ASIC Model: BM1366
ASIC Count: 1
Small Core Count: 894
Frequency: 485 MHz
Heap Free: 97240 bytes
Firmware Version: v2.1.9-36-gaecb8af-dirty
Board Version: 204
Uptime: 1174 hours 16 minutes
=====================================
Wed Jan 28 12:00:01 AM UTC 2026
Best Value:
LightningPay:
66,981 sats = $100
Other NZ options:
64,685 sats - Easy Crypto
56,715 sats - Swyftx
47,511 sats - Independent Reserve
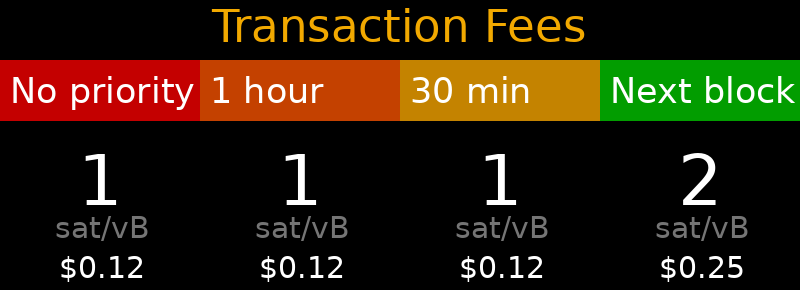
🧾 Estimated fee for 140 vB tx: 140.00 sats (0.12 USD)
📦 Fee rate from node: 0.00001000 BTC/kvB
📏 Converted: 1.00 sats/vB
🧭 Fee classification: Low
💰 BTC price (CoinGecko): 89,116.00 USD
I've watched soil health swing back and forth like a pendulum on my farm. A bit of tilling here, a sprinkle of synthetic fertilizer there, and suddenly, the earth isn’t breathing anymore. It’s a mistake I see many make, thinking the answer lies in quick fixes rather than nurturing the foundation of it all.
People often believe that adding more chemicals is the straightforward path to healthy crops. But what they don’t see is the invisible web of life beneath their feet—microbes that work tirelessly to break down nutrients and support plant health. When we ignore them, we strip our soil of its vitality.
What I’ve learned is that health isn’t about band-aids. It’s about digging deeper, literally and figuratively. When we start paying attention to soil microbiology, everything changes. We see stronger plants, better yields, and a more resilient ecosystem.
If we want to grow, we need to remember that the best answers often lie in the soil. #StoreysInTheDirt #Homesteading #RegenerativeAg
⚡ Zap if you found this valuable!
#bitcoin #farming #soil #health #plant #agriculture #sustainable #organic
#bitcoin #farming #soil #health #plant #agriculture #sustainable #organic
1344 

✄------------ 9:00 ------------✄
WabiSabi coinjoins on January 27
Full data:
https://coinjoin.kruw .io/
Fee: 0.0 %
29 rounds
New: 102.7 BTC (est.) | Remixing: 829.5 BTC
Avg: 300 inputs | 12.57 AS | 1.35 s/vb
Min: 100 inputs | Max: 430 inputs
https://api.opencoordinator .org/
Fee: 0.0 %
26 rounds
New: 0.2 BTC (est.) | Remixing: 4.7 BTC
Avg: 31 inputs | 3.79 AS | 2.01 s/vb
Min: 21 inputs | Max: 44 inputs
Free coordinators without any successful round:
https://api.coinjoiner.com/
LiquiSabi: WabiSabi Liquidity Status
Bot tracking rounds broadcasted by WabiSabi coordinators publishing themselves on Nostr.
CoinJoin.nl
Timechain info:
Block height: 934,035
Network difficulty: 141.67T
Next difficulty adjustment(est.): 123.11T
Market dominance %: 54.44%
BTC price per 1K sats($): 0.89
24H median transaction fee($): 0.20
#meme #memes #btc #nostr #plebchain #memestr #pleb #laugh #funny #jokes #primal #serioushumour
Title: From father to daddy
https://v.redd.it/e16uwz83plfg1



































