
GM Nostr! 🌞
🎁 Announcing Keycast 🔑
A remote signing platform for teams.
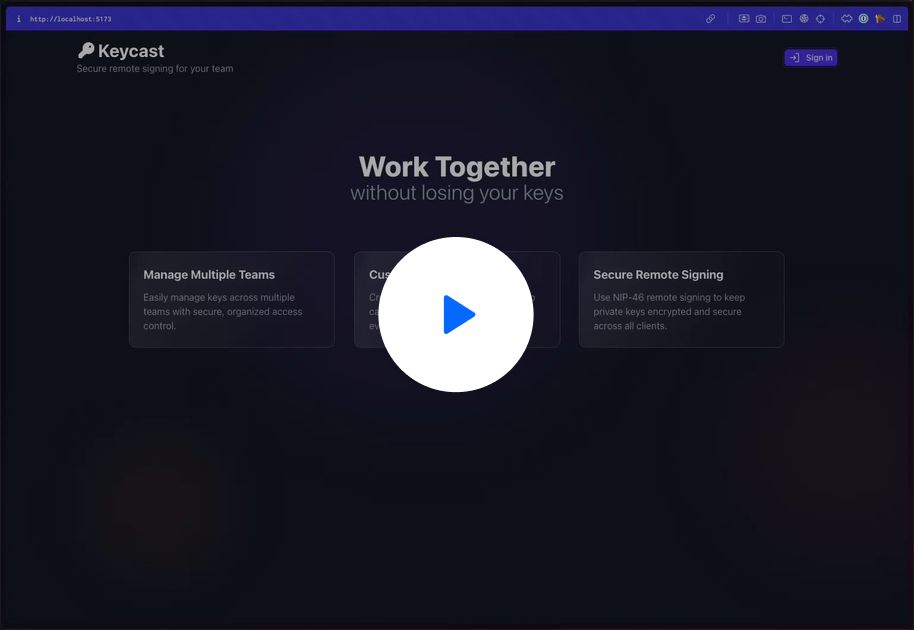
CleanShot 2024-12-24 at 09.11.01
Video uploaded to CleanShot Cloud
Remote signing (NIP-46) has always had a lot of promise. Apps like Amber, nsec.app, and others have made it possible to manage your nostr keys in a way that is safer than browser extensions or pasting your nsec around the internet.
BUT, none of them catered to teams. Groups like
@npub1nstr...rg5l and
@npub19mdu...6vzk and many many companies out there are just sharing the main account nsec between different people and using it in different apps. A recipe for disaster.
Keycast aims to finally fix this. It allows you to:
- Manage teams of nostr users
- Manage multiple keys that you want to give others access to
- Create authorizations for those keys that grant specific permissions that can be changed, revoked, etc.
- Create your own custom permissions
- Run the signing infrastructure without any extra work
And do it all in a self-sovereign way. Keycast is meant to be run on your server, by you. I think it's tremendously important that this sort of tool doesn't exist as a hosted service (which would basically be a huge key honeypot over time).
The app is both a management web app AND a backend process that manages sub-processes that listen for remote signing requests, check permissions, and sign events.
There is a basic docker setup to start, but my goal is to have this easily deployable to StartOS, Umbrel, Podman, and others.
Code here:

GitHub
GitHub - erskingardner/keycast
Contribute to erskingardner/keycast development by creating an account on GitHub.
Replies (57)
gm
Niiiice!! Gonna take a dive into this soon. Awesome work!
GM! ☕ ☀️ 🫂

 JeffG
JeffG
GM Nostr! 🌞
🎁 Announcing Keycast 🔑
A remote signing platform for teams.

CleanShot 2024-12-24 at 09.11.01
Video uploaded to CleanShot Cloud
Remote signing (NIP-46) has always had a lot of promise. Apps like Amber, nsec.app, and others have made it possible to manage your nostr keys in a way that is safer than browser extensions or pasting your nsec around the internet.
BUT, none of them catered to teams. Groups like
@npub1nstr...rg5l and
@npub19mdu...6vzk and many many companies out there are just sharing the main account nsec between different people and using it in different apps. A recipe for disaster.
Keycast aims to finally fix this. It allows you to:
- Manage teams of nostr users
- Manage multiple keys that you want to give others access to
- Create authorizations for those keys that grant specific permissions that can be changed, revoked, etc.
- Create your own custom permissions
- Run the signing infrastructure without any extra work
And do it all in a self-sovereign way. Keycast is meant to be run on your server, by you. I think it's tremendously important that this sort of tool doesn't exist as a hosted service (which would basically be a huge key honeypot over time).
The app is both a management web app AND a backend process that manages sub-processes that listen for remote signing requests, check permissions, and sign events.
There is a basic docker setup to start, but my goal is to have this easily deployable to StartOS, Umbrel, Podman, and others.
Code here:

GitHub
GitHub - erskingardner/keycast
Contribute to erskingardner/keycast development by creating an account on GitHub.
What nostr clients support nip46? I don't think #Amethyst supports it?
Legend!
Don’t mind Jeff just quietly solving nostr’s biggest problems 👏👏
Great Job JeffG!
 JeffG
JeffG
GM Nostr! 🌞
🎁 Announcing Keycast 🔑
A remote signing platform for teams.

CleanShot 2024-12-24 at 09.11.01
Video uploaded to CleanShot Cloud
Remote signing (NIP-46) has always had a lot of promise. Apps like Amber, nsec.app, and others have made it possible to manage your nostr keys in a way that is safer than browser extensions or pasting your nsec around the internet.
BUT, none of them catered to teams. Groups like
@npub1nstr...rg5l and
@npub19mdu...6vzk and many many companies out there are just sharing the main account nsec between different people and using it in different apps. A recipe for disaster.
Keycast aims to finally fix this. It allows you to:
- Manage teams of nostr users
- Manage multiple keys that you want to give others access to
- Create authorizations for those keys that grant specific permissions that can be changed, revoked, etc.
- Create your own custom permissions
- Run the signing infrastructure without any extra work
And do it all in a self-sovereign way. Keycast is meant to be run on your server, by you. I think it's tremendously important that this sort of tool doesn't exist as a hosted service (which would basically be a huge key honeypot over time).
The app is both a management web app AND a backend process that manages sub-processes that listen for remote signing requests, check permissions, and sign events.
There is a basic docker setup to start, but my goal is to have this easily deployable to StartOS, Umbrel, Podman, and others.
Code here:

GitHub
GitHub - erskingardner/keycast
Contribute to erskingardner/keycast development by creating an account on GitHub.
Bravo!
This will improve team experience on nostr so much! Thanks for working on this 🤙🏼
GM☕️☕️🌅🎄Christmas present 🎁 to the Nostr community 💜!
Ho ho ho 🧑🎄 that’s very cool 🫶
why do all the useful tools have to have this disgusting startup marketing aesthetics? "work together", give me a break
What would you rather? Work alone in your mom’s basement?
Give
@Vitor Pamplona 5 minutes and
my point is that signing events is not the exact definition of work
For single users Knox is great. For teams, less so.
In any case, use what you want and stop complaining about having so many choices of high quality free software.
Knocking it out of the park, well done chap 👏
👀
The amount of apps drops coming to
@Start9 is incredible! Thanks the hard work!
Very great!
Beautiful present, thanks!
♥️
Thanks for sharing. I didn't know about this project. I hope a GUI gets developed too.
We need more of this, If you ask me Keycast is totally a candidate for funding on Angor.
GM!
using github to host code, what a sheep
gm
💜🔥🤙🔥🔥🔥🔥🔥
Good Morning! MERRY CHRISTMAS!⚡️💜☕️🎄
Awesome stuff Jeff!
I love the elegance of the policy system. Easy to understand, yet very powerful
Gotta chance how we do GiftWraps. We download everything and decrypt them all at startup. So, if your NIP-46 can manage 1000s of decryptions per second, we can make it work right now. Otherwise, I need to find a way to lazy load this.
Did you abandon nostr messaging?
Not at all. Just took a short break. Only started working on keycast at the beginning of last week.
I’ll be back to the messaging stuff just after Christmas.
Hmm. Middle of family stuff now but let me have a look a bit later. I might have just borked something while trying to get the docker stuff going last night.
Give me a bit of time to polish things up and then we can benchmark it.
This is amazing!
That would be awesome. Would love to be able to also offer some bounties on permissions, getting lots of tests written, and having it deployable on lots and lots of systems.
Yes it is. I constantly sign events for work
Thank you! you scared me a little haha
can't wait to see White-noise in action.
I suspect
@JeffG is working on a windows machine. since thats the only OS I know of that does not have case sensitive file names 😀
Also I cloned the repo and the files where missing the new line at the end of the files
Nope. New Mac. I’m weirded out by that file name too.
Thank you!
Very odd. File explorer and terminal were showing the uppercase spelling but my guess is that I had it wrong early, changed it, and for some reason git was still tracking it in the old case without changing it... 🤷♂️
I'll push a fix (for a few things I found since announcing 🤦♂️) sometime soon.
For now, it's Christmas time. 🎅
A few questions I had for a friend
- Are secret keys loaded into the same address space as the process running an http server?
- Are secret keys stored in plaintext or reversible encryption accessible to the process running an http server?
- Are secret keys stored in a file readable by the http server process?
What is a public url of a hosted version one might play around with? Again asking for a friend.
Gm
The answer to all three is what you don’t want to hear. For v1 I’ve left a lot to desire. Keys are encrypted at rest but fetched/decrypted by the same process running the http server (but not from any of the http methods directly).
I'm looking for teams or companies that are looking to test Keychat out.
Deployment via Docker should work well so if your team or company is willing to run a VM or install this on a server you already have, let me know. I'm happy to help you walk through the setup.
View quoted note →You're welcome. Here's more info.
 JeffG
JeffG
GM Nostr! 🌞
🎁 Announcing Keycast 🔑
A remote signing platform for teams.

CleanShot 2024-12-24 at 09.11.01
Video uploaded to CleanShot Cloud
Remote signing (NIP-46) has always had a lot of promise. Apps like Amber, nsec.app, and others have made it possible to manage your nostr keys in a way that is safer than browser extensions or pasting your nsec around the internet.
BUT, none of them catered to teams. Groups like
@npub1nstr...rg5l and
@npub19mdu...6vzk and many many companies out there are just sharing the main account nsec between different people and using it in different apps. A recipe for disaster.
Keycast aims to finally fix this. It allows you to:
- Manage teams of nostr users
- Manage multiple keys that you want to give others access to
- Create authorizations for those keys that grant specific permissions that can be changed, revoked, etc.
- Create your own custom permissions
- Run the signing infrastructure without any extra work
And do it all in a self-sovereign way. Keycast is meant to be run on your server, by you. I think it's tremendously important that this sort of tool doesn't exist as a hosted service (which would basically be a huge key honeypot over time).
The app is both a management web app AND a backend process that manages sub-processes that listen for remote signing requests, check permissions, and sign events.
There is a basic docker setup to start, but my goal is to have this easily deployable to StartOS, Umbrel, Podman, and others.
Code here:

GitHub
GitHub - erskingardner/keycast
Contribute to erskingardner/keycast development by creating an account on GitHub.
My big man 😎
THIS is exactly the solution I've been most anxiously looking for!
Yo
@JeffG it would be amazing to have you on this call! I'd love the fact that the freedom tech community is getting into healthcare which needs to be fixed, just like our money. Solutions like Keycast will play a pivotal part in this.
note1lnh3q6648ysulrx2pgeyhv2cqqle9vftdxalq3yqkqa7c89eljtqyr70nl
Cool idea! I’ll see, maybe I can make it

 JeffG
JeffG
GM Nostr! 🌞
🎁 Announcing Keycast 🔑
A remote signing platform for teams.

CleanShot 2024-12-24 at 09.11.01
Video uploaded to CleanShot Cloud
Remote signing (NIP-46) has always had a lot of promise. Apps like Amber, nsec.app, and others have made it possible to manage your nostr keys in a way that is safer than browser extensions or pasting your nsec around the internet.
BUT, none of them catered to teams. Groups like
@npub1nstr...rg5l and
@npub19mdu...6vzk and many many companies out there are just sharing the main account nsec between different people and using it in different apps. A recipe for disaster.
Keycast aims to finally fix this. It allows you to:
- Manage teams of nostr users
- Manage multiple keys that you want to give others access to
- Create authorizations for those keys that grant specific permissions that can be changed, revoked, etc.
- Create your own custom permissions
- Run the signing infrastructure without any extra work
And do it all in a self-sovereign way. Keycast is meant to be run on your server, by you. I think it's tremendously important that this sort of tool doesn't exist as a hosted service (which would basically be a huge key honeypot over time).
The app is both a management web app AND a backend process that manages sub-processes that listen for remote signing requests, check permissions, and sign events.
There is a basic docker setup to start, but my goal is to have this easily deployable to StartOS, Umbrel, Podman, and others.
Code here:

GitHub
GitHub - erskingardner/keycast
Contribute to erskingardner/keycast development by creating an account on GitHub.
 Remote signing (NIP-46) has always had a lot of promise. Apps like Amber, nsec.app, and others have made it possible to manage your nostr keys in a way that is safer than browser extensions or pasting your nsec around the internet.
BUT, none of them catered to teams. Groups like @npub1nstr...rg5l and @npub19mdu...6vzk and many many companies out there are just sharing the main account nsec between different people and using it in different apps. A recipe for disaster.
Keycast aims to finally fix this. It allows you to:
- Manage teams of nostr users
- Manage multiple keys that you want to give others access to
- Create authorizations for those keys that grant specific permissions that can be changed, revoked, etc.
- Create your own custom permissions
- Run the signing infrastructure without any extra work
And do it all in a self-sovereign way. Keycast is meant to be run on your server, by you. I think it's tremendously important that this sort of tool doesn't exist as a hosted service (which would basically be a huge key honeypot over time).
The app is both a management web app AND a backend process that manages sub-processes that listen for remote signing requests, check permissions, and sign events.
There is a basic docker setup to start, but my goal is to have this easily deployable to StartOS, Umbrel, Podman, and others.
Code here:
Remote signing (NIP-46) has always had a lot of promise. Apps like Amber, nsec.app, and others have made it possible to manage your nostr keys in a way that is safer than browser extensions or pasting your nsec around the internet.
BUT, none of them catered to teams. Groups like @npub1nstr...rg5l and @npub19mdu...6vzk and many many companies out there are just sharing the main account nsec between different people and using it in different apps. A recipe for disaster.
Keycast aims to finally fix this. It allows you to:
- Manage teams of nostr users
- Manage multiple keys that you want to give others access to
- Create authorizations for those keys that grant specific permissions that can be changed, revoked, etc.
- Create your own custom permissions
- Run the signing infrastructure without any extra work
And do it all in a self-sovereign way. Keycast is meant to be run on your server, by you. I think it's tremendously important that this sort of tool doesn't exist as a hosted service (which would basically be a huge key honeypot over time).
The app is both a management web app AND a backend process that manages sub-processes that listen for remote signing requests, check permissions, and sign events.
There is a basic docker setup to start, but my goal is to have this easily deployable to StartOS, Umbrel, Podman, and others.
Code here: 







































