Dream flow: buy new phone, enter 12 words, done.
Everything's set up, including my config, apps, contacts, etc. The 12 words are my nsec in this case ofc.
Login to reply
Replies (61)
That would be nice.
Make it so!
Goals
👀👀👀 @daylightco
👀💜
I dream of a Nostr Linux distro where your config is saved to relays. Install anywhere and log in.
Basically .dotfiles on nostr?
Thirteen for me. twelve words is my decoy persona.

Yes! Combine with some Nostr native file hosting for your home folder and you're set!
Would be nice to use 12 words and a passphrase, then repeat with another passphrase to have a nice decoy phone. In case of coercive physical attack you would (temporary) lose controlo of your identity, but at least funds and data would remain safe.
👀
We have gistr, ngit, song, so it is alredy here
Almost with GrapheneOS.
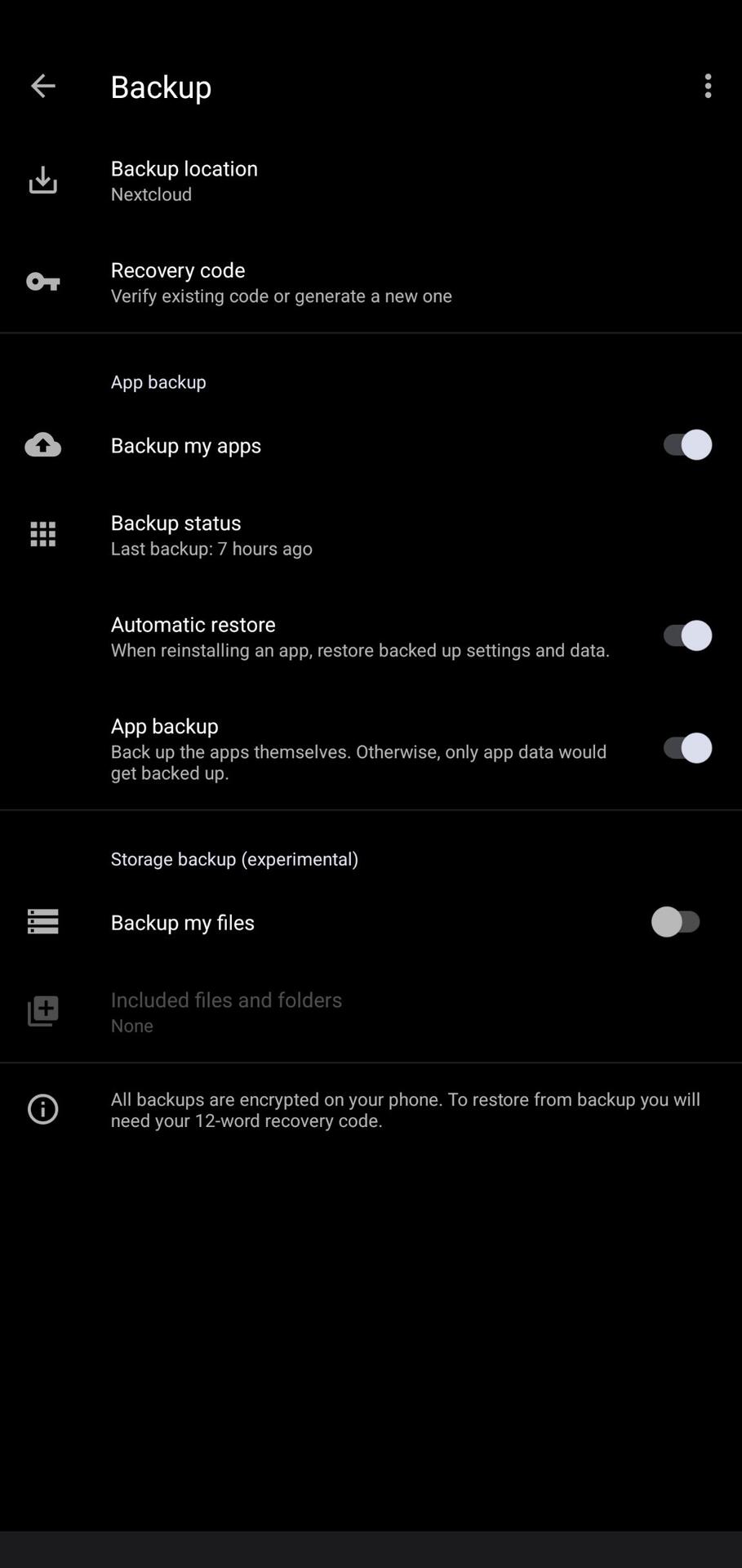

Encrypt backup on (private?) relay,
Decrypt backup with nsec,
Profit.
Recovery code is 12 words
i think one of the next steps is to get a hardware company to develop something like this.
I wonder if Android is programmable enough to pull this off.
#YESTR
Consider it in the works 🌞⚡️
we can't have that because samsung
on it 🫡
Not quite the same, as the graphene words secure the monolith, not the individual components, that, with nostr, may be stored on various relays worldwide
I have thought about this also.
...so like, configuration.nix but on nostr, encrypted...?
🤯
not a bad idea
blimey
Read this thread. Paradigms are shifting...
Amazing
You guys are so stinking smart
CalyxOS. Already got it.
Just use Calyx and its built-in backup, or derivatives of it (it's Apache licensed, there's no limit to the forks we could make of it!)
I feel like this note explains most of what I need to know about some nostr builder's visions of the future. Not to put everyone in one basket, but my technology world view is essentially completely opposed to this. I don't even want a smart phone anymore.
View quoted note →
Planned for zap.store: automatic backups of your installed apps, optionally encrypted.
So maybe not the phone config, but apps and contacts definitely possible to restore with npub/nsec.
Baby steps. First major release coming next week.
View quoted note →
That’s it. That’s digital identity. Done.
wow
nostr profile? I don't think so
If you meant it even automatically copies and pastes the key you use for backup into nostr, then no it doesn't do that yet. So create the app yourself. It'll be fairly easy.
These 12 words might be as sensitive (if not more) than the words that allow me to send #bitcoin. They're the seed phrase for my digital identity, which is tied to rw identity. The downstream interactions are far more complex than something used to write txs on a timechain.
If someone gets my bitcoin seed phrase, all that money in that wallet is gone; they can impoverish me. Someone gets my nsec, they can *be* me, which could be worse.
What can guard against this? Something like this: 
GitHub
Enhanced proposal to NIP6: Multi-seed nostr key pairs · Issue #282 · nostr-protocol/nips
Using multiple seeds to generate nostr key pairs will allow nostr identities to be: redundant flexible Redundant With a 2-3 keyset, a user can stil...
Blossom for storage.
Ooh! I missed gistr. Cool 😎
Your digital identity should NEVER be that critical to keep private. There should always be a way to restart using a real life meeting.
🤯
Do it
Part of why I like buying a new phone is because it DOESN'T have the mess I left on the old one...
Thanks, I'll look into those!
Easy to do if you have a third party involved (they just record your config)
What I want is for this setup without a trusted third party and connecting to my own server.
Very yes
Like a Sparrow border wallet. All you have to remember is a coordinate, a shape and a word. That’s only 3 things.
Same
Would be extremely cool
👀👀 this would be awesome
But where would the phone get the data from?
Yes
"relays", ofc
🫂
Config saved to Umbrel server maybe?
What would happen if you accidentally entered your nsec on a compromised website, application or device?
Would have been awesome.
We would also like this a lot. It's been getting harder and harder to get new backdoors.
The phone recovery 12 words are BIP-85 from the one true key that you protect, everything else is recoverable through derivation paths.
One seed to rule them all.
The same that would happen if you enter your bitcoin seed phrase into a compromised thingy
It’s secured inside of bananas on the blockchain
I'm still in love with @Zapstore - so much freaking potential. And I wouldn't be surprised if my dream flow would be a reality in 12 months from now.
This is exactly how Passport Prime is gonna work. Except you won't even need to enter seed words (you can if you want to OFC) just tap some NFC cards!
Key protection is key, and much easier said than done imho.